1. in the e-r model, an entity that is existence dependent on another and does not have a key of its own is called. a. a weak entity b. a dominant entity c. a parent entity d. a referential entity 2. serve as the intermediary between the user and the database. a. dbmss b. metadata c. end-user data d. programming languages 3. the term refers to an organization of components that define and regulate the collection, storage, management and use of data within a database environment. a. structured data b. transaction c. management system d. database system 4. a is the primary key of one table that has been placed into another table to create a common attribute. a. superkey b. composite primary key c. candidate key d. foreign key 5. a(n) is the set of possible values for a given attribute. a. domain b. range c. identifier d. key
Answers
a. a weak entity . The answer is a. a vulnerable entity. In the E-R paradigm, a weak entity is one that lacks its own unique identity or key and is dependent on another entity known as the owner entity.
for its existence. The primary key of the owner entity is combined with the primary key of the weak entity to generate a composite primary key. The correct answer is a. DBMSs (Database Management Systems) (Database Management Systems). DBMSs are software systems that serve as go-betweens for end-users and B database. They are in charge of the database's organization, storage, retrieval, security, and integrity. The solution is d. database system. A database system is a set of components that define and govern the collection, storage, administration, and use of data inside a computer system.
Learn more about database here:
https://brainly.com/question/12523523
#SPJ4
Related Questions
Do you think more devices connect to the internet wirelessly or wired? Why?
Answers
Answer:
yes morr devices connect to the internet wirelessly b cos no wire in BTW dat can cos destruction like if d wire has been peeled
Explanation:
plz give me brainiest
Someone help its about LA Doña 2
so basically I just wanted to know who has seen it all and where i can watch it
Answers
Answer:
If you look on Just watch it will show you the different people that currently have it right now it is sadly not on Netflix from what I could find out but it will probably be added later on.
Explanation:
Netflix sometimes takes its time adding shows which is sad but that is just how they work. I would recommend maybe trying it on a website that Just watch list or just buy the disc from eBay. either way, I wish you luck!
The ____ effect diffuses or softens the edges of the object. (I'm using InDesign)
ruler
gradient
feather
stroke
please help me
Answers
Answer:
Feather
Explanation:
Directional Feather softens the edges of an object by fading the edges to transparent from directions that you specify.
The feather effect diffuses or softens the edges of the object. THe correct option is C.
What is feather effect?In computer graphics software, feathering is most commonly used on a paintbrush tool.
This type of feathering gives the painted area a smooth appearance. It has the appearance of an airbrush or spraypaint. The color is concentrated in the brush area and blends out toward the edges.
In Photoshop, feathering is used to soften the edge of an image, brush, or layer. A brush stroke with a high feather, for example, will have blurred edges that blend into the image.
A brush stroke with a low feather, on the other hand, will have a hard edge and be more useful when painting close to objects.
Thus, the correct option is C.
For more details regarding photoshop, visit:
https://brainly.com/question/2801496
#SPJ2
can someone help me with this trace table - its computer science

Answers
TThe while loop keeps going until count is greater than or equal to 10.
count = 0, sum = 0
count = 2, sum =2
count = 4, sum = 6
count = 6, sum = 12
count = 8, sum = 20
count = 10, sum = 30
Now that count is equal to 10, it exits the while loop and the program ends. The values above complete your trace table.
Which securities protect data through processes, procedures,decisions,and user pernissions. Determines where and how data can be shared or stored
Answers
Answer:
Data can be stored on storage devices.
Explanation:
Network security, Application security and information security are the securities that protect data. Data can be stored on storage devices such as hard disk drives, solid state drives, external hard drives, USB flash drives and SD cards etc. Hard disk drives, floppy disks and tapes store data magnetically. The data can be stored with a device that spins the disk with magnetic coatings and heads has the ability to read and write information in the form of magnetic patterns.
Select the correct text in the passage.
Which software development agreement helps distribute risks between the software developer, client, and third parties?
Software developers and clients make software development agreements that legally define duties, payment, and ownership. Unless the developer is the client's employee, the software developer owns the copyright of the software Software development agreements also delineat
maintenance tasks in terms of validity, time, and criteria. These include as UPDATES, UPGRADES, WARRANTIES, and SUPPORT SERVICES.
The options for this question are the capitalized words: updates, upgrades, warranties, support services
Answers
Answer:
support services
Explanation:
What is a string in Python language?
A) An ordered set of characters
B) An ordered set of values
C) A sequence of Booleans
D) A sequence of numbers
Answers
Answer:
A
Explanation:
a string consists of letters and numbers
like "myUsername123" can be a string
now their order is important.
but they are not booleans, and they are not necessarily only numbers, and "values" is too vague
so its A
32.
To give an existing document a different name
A. retype and give it another name,
B. use the save command
C. use the same as command
D. use windows explorer to copy.
Answers
Answer:
B.
Explanation:
If you are trying to save an existing document you would use the save command and you will be prompted if you want to rename it to what ever you wish
Hope this helps :)
what are some scams you should avoid when looking for a credit counselor?
Answers
Before any credit counseling services are offered, the company requires money.
What exactly does a credit advisor do?Organizations that provide credit counseling can help you with your finances and bills, assist you with creating a budget, and provide training on money management. Its Fair Debt Collection Act's specific provisions have been clarified by the CFPB's debt recovery rule (FDCPA)
How is a credit counselor compensated?Non-profit organizations typically obtain some funding to cover their costs from two sources: clients who pay to use their debt payback program and clients' creditors who agree to cover those costs as part of the credit counseling organization's negotiated agreements with creditors.
To know more about credit counselor visit:
https://brainly.com/question/15563363
#SPJ4
write an sql query to fetch the sum of salary working in the department id =90
Answers
SELECT SUM(salary) AS TotalSalary FROM employees WHERE department_id = 90;
Surely, I can help you write an SQL query to fetch the sum of salaries of employees working in the department id=90.
SQL query to fetch the sum of salary working in the department id=90
The SQL query to fetch the sum of salary working in the department id=90 is as follows:
SELECT SUM(salary) AS TotalSalary FROM employees WHERE department_id = 90;
The above SQL query retrieves the sum of the salaries of all the employees who work in the department id = 90.
Here, the 'SUM()' function adds the values of the 'salary' column for each employee. The 'AS' keyword is used to provide an alias 'TotalSalary' to the 'SUM()' function.
Lastly, the 'WHERE' clause filters the rows based on the 'department_id' column value equal to 90 to retrieve the sum of salaries of employees in that department.
Learn more about queries at: https://brainly.com/question/31588959
#SPJ11
Why must web designers select a common font?
Answers
to ensure visitors can view it
to keep the page consistent
to make the page easier to read
classify the computer on the basis of working principle and on the basis of their size. Also define one of a type in each category.
Answers
Answer:
Supercomputer, Mainframe Computer, Minicomputer, Microcomputer,
Explanation:
Supercomputer is the fastest, most expensive, big in size, and most powerful computer that can perform multiple tasks within no second. It has multi-user, multiprocessing, very high efficiency and large amount of storage capacity. It is called super computer because it can solve difficult and complex problem within a nano second.
Mainframe Computer is the large sized computer that covers about 1000 sq feet. It is general purpose computer that is designed to process large amount of data with very high speed. It accepts large amount of data from different terminals and multiple users and process them at same time. More than 100 users are allowed to work in this system. It is applicable for large organization with multi-users for example: large business organization, Department of examinations, Industries and defense to process data of complex nature. It uses several CPU for data processing.
Mini Computers are medium sized computer. So, these are popular as middle ranged computer. It is also multiple user computer and supports more than dozen of people at a time. It is costlier than microcomputer. It is also used in university, middle range business organizations to process complex data. It is also used in scientific research, instrumentation system, engineering analysis, and industrial process monitoring and control etc.
Most popular general purpose computers which are mostly used on day to day work are microcomputers. These are popular as Home PC or Personal Computer (PC) because these are single user computers and mostly used for personal use and application. These support many higher level application cost and easy in operation.
The company generates a lot of revenue and is rapidly growing. They're expecting to hire hundreds of new employees in the next year or so, and you may not be able to scale your operations at the pace you're working.
Answers
Answer:
The most appropriate way to deal with the situation presented above is to acquire more space at the current office site at additional rent beforehand.
Explanation:
The Scaling of a revenue-generating business is a crucial task in which a lot of pre-planning and thinking is required.
In order to scale the business in the next year, the planning of it is to be carried out at the moment and proper necessary arrangements are ensured. These steps could be one from:
Looking for bigger spaces for renting for a full shift of the operationsLooking for a site office for an additional officeAcquiring more space in the current office site.This process would result in acquiring a bigger place beforehand but in order to mitigate the risk, try to keep the place in view by providing them a bare minimum advance for the additional units.
how does air conditioner work
please short answer please
Answers
which statements compares the copy and cut commands
Answers
The statement that accurately compares the copy and cut commands is 2)Only the cut command removes the text from the original document.
When using the copy command, the selected text is duplicated or copied to a temporary storage area called the clipboard.
This allows the user to paste the copied text elsewhere, such as in a different location within the same document or in a separate document altogether.
However, the original text remains in its original place.
The copy command does not remove or delete the text from the original document; it merely creates a duplicate that can be pasted elsewhere.
On the other hand, the cut command not only copies the selected text to the clipboard but also removes it from the original document.
This means that when the cut command is executed, the selected text is deleted or "cut" from its original location.
The user can then paste the cut text in a different place, effectively moving it from its original location to a new location.
The cut command is useful when you want to relocate or remove a section of text entirely from one part of a document to another.
For more questions on cut commands
https://brainly.com/question/19971377
#SPJ8
Question: Which statement compares the copy and cut commands?
1. only the copy command requires the highlighting text
2. only to cut command removes the text from the original document
3. only the cut command uses the paste command to complete the task
4. only the copy command is used to add text from a document to a new document
This resource is a collection of 20,000 detailed job profiles. O*NET, the online version of the DOT, is a database of job profiles
Answers
Answer:
The ONET database holds data or details of job profiles available to applicants on the internet.
Explanation:
A database is an important tool in web development. Commercial or e-commerce websites use databases to store important information needed by the customers to make purchases of goods and services.
Other websites like government agencies and research communities use these databases to collect and store data retrieved from visitors to the sites.
Have you watched, or listened to, a documentary on your computer, smartphone, or on demand? Do you think these new distribution choices help or hurt future opportunities for video journalists? Support your answer.
Answers
Answer:
Yes, and No it does not hurt their opportunities
Explanation:
The main goal of video journalism is to get their work in front of as many people as possible so they can share their stories with the entire world. These platforms allow for this to happen. Smartphones, Computers, On-demand video platforms, etc. all allow Video Journalists to publish their work in various different platforms and formats in order to get their work seen by hundreds, thousands, or even millions of individuals. Therefore, It does not hurt video journalists, but instead encourages them and helps them further their work by creating more opportunities.
which multicast reserved address is designed to reach solicited-node addresses?
Answers
The multicast reserved address that is designed to reach solicited-node addresses is: FF02::1:FF00:0000/104.
What is multicast reserved address?
A multicast reserved address is an address utilized in IPv6 and IPv4. Multicast refers to one-to-many communication, with the sending host sending a single message to a specified group of hosts.
The multicast address FF02::1:FF00:0000/104 has a unique use in the context of the Neighbor Discovery Protocol (NDP).Solicited-node multicast addresses are formed by taking the lower 24 bits of an address and appending it to the solicited-node multicast address prefix FF02::1:FF00:0000/104.
The multicast reserved address that is designed to reach solicited-node addresses is: FF02::1:FF00:0000/104.
Note: Solicited-node multicast addresses are a part of the Neighbor Discovery Protocol (NDP) that aids in the discovery of IPv6 nodes and the resolution of IPv6 addresses to MAC addresses in an Ethernet network.
Learn more about IP address:
brainly.com/question/24930846
#SPJ11
Which group contains the command to manually conduct a spell check ?
Answers
Answer:To check spelling in a Word document, open up the document, head to the “Review” tab, then click on “Spelling & Grammar” (part of the “Proofing” group of tools). Then a window will appear showing the first word the program believes to be misspelled. Click through the options to review the whole document.
Explanation:Hope this helped u out btw can i plz have brainlist only if u wanna give me brainlist though have an great day kind sir or ma'am!
Explain why this scenario could put an organization in jeopardy of losing some of its workforce.
Situation: The IT manager decides to add a new software application to replace an older albeit less efficient software application.
Answers
Answer:
Not educating its employees on the new software.
You are a cleared employee. You discovered fraud and waste of money related to a classified program within your agency. If you report this fraud and waste through appropriate channels, you may receive protection under the Presidential Policy Directive 19 (PPD-19), Protecting Whistleblowers with Access to Classified Information.A. TrueB. False
Answers
Answer:
A. True.
Explanation:
If you are a cleared employee, who discovered fraud and waste of money related to a classified program within your agency. When you report this fraud and waste through appropriate channels, you may receive protection under the Presidential Policy Directive 19 (PPD-19): Protecting Whistleblowers with Access to Classified Information.
In the United States of America, President Barack Obama signed the Presidential Policy Directive 19 (PPD-19) in 2012. The PPD-19 is an executive order designed to provide significant protection for an employee who have access to classified informations such as waste of money and frauds, as well as prohibiting any form of retaliation against this cleared employee.
now, it’s time to process the data. as you know, this step involves finding and eliminating errors and inaccuracies that can get in the way of your results. while cleaning the data, you notice there’s missing data in one of the rows. what might you do to fix this problem? select all that apply.
Answers
The thing that a person need to do that might fix this problem are:
Ask a colleague on your team how they've handled similar issues in the pastAsk you supervisor for guidance.Check more about errors below.
What are errors in quantitative analysis?The term error is known to be a word that connote a mistake in a given work. Note that the types of errors in lab measurements are random error, systematic error, and others.
To be able to remove or correct error, one must have the knowledge of what the error is and when you do not know, it is good you ask others.
Therefore, The thing that a person need to do that might fix this problem are:
Ask a colleague on your team how they've handled similar issues in the pastAsk you supervisor for guidance.Learn more about Data Error from
https://brainly.com/question/12600423
#SPJ1
See options below
Sort the spreadsheet so the row with missing data is at the bottom
Ask a colleague on your team how they've handled similar issues in the past
Ask you supervisor for guidance
Delete the row with the missing data point
answer these guys thanks
nonsense answers well be reported
What are the different types of fiber connectors? Cite their advantages and disadvantages
Answers
Answer:types of fiber connectors
Bionic Connector · Standard Connector (SC) · Ferrule Core Connector (FC) · ST Connector (ST) · SMA Connector · Lucent Connector (LC) · LC Duplex CouplerAdvantages:
Speed in internetsupport better healthconnect multiple deviceinternet reliabilityDisadvantages
The optical fibers are difficult to splice, there are loss of the light in the fiber due to scattering. They have limited physical arc of cables. If you bend them too much, they will break. The optical fibers are more expensive to install, and they have to be installed by the specialists.explain how a database management system might incrementally maintain this view in response to insertions and deletions into the enrollment table. what assumptions do you need to make about indexes in order to make maintenance truly incremental?
Answers
A DBMS can maintain a view incrementally using triggers and stored procedures, but it needs efficient and optimized indexes and a reliable backup and recovery system to ensure accuracy and prevent data loss.
1. Triggers and stored procedures can be programmed in a DBMS to update a view automatically when changes are made to a table, such as an enrollment table.
2. To ensure incremental maintenance, the DBMS needs efficient and optimized indexes. These indexes need to be designed to quickly locate relevant data, even as the table grows in size. The DBMS must also monitor index performance and make adjustments as necessary to maintain efficiency.
3. A robust backup and recovery system is necessary to prevent data loss or errors during incremental maintenance. The DBMS should have a reliable system in place for backing up the database and restoring it in case of any issues.
4. In summary, an efficient and optimized DBMS with well-designed indexes, reliable backup and recovery mechanisms, and effective triggers and stored procedures can ensure successful and accurate incremental maintenance of views.
Learn more about DBMS :
https://brainly.com/question/31715138
#SPJ11
How many bits would be needed to count all of the students in class today?
10 students in the class
Answers
Answer:
If you have 12 students in class you will need 4 bits.
what is MS-DOS ?
pls ans
Answers
Answer:
MS-DOS is one of the oldest and widely used operating system which allows the user to navigate, open, and otherwise manipulate files on their computer from a command line instead of a GUI like Windows.
How should a common data source like social media comments be categorized? 1 structured data 2 unstructured data 3 temporary data 4 dirty data
Answers
Unstructured data is information that is not stored in a predefined model. This signifies that the data is not kept in a structured manner. Unstructured data examples include social media comments, blog posts, videos, and papers.
Unstructured data is information that lacks a predefined data model or is not organized in a predefined way. Unstructured data is often text-heavy, although it may also include data such as dates, figures, and facts.
This causes anomalies and ambiguities that make traditional programs difficult to understand as compared to data kept in fielded form in databases or annotated (semantically labeled) in papers.
To know more about Unstructured data, visit;
brainly.com/question/28333364
#SPJ4
As a student, what are the things you need to know to start building a program?
Answers
Answer:
Get the basics right. When you start learning, the first thing you need to be sure of are the“basics”. ...
Build patience. The number one prerequisite for being successful as a programmer is building patience. ...
Set a goal & move towards it. ...
Do more projects. ...
Get into social coding. ...
Balance your learning.
One of the disadvantages of cable technology is that: while it works well for television signals, it is ineffective for data transmissions required by the Internet. while it works well for television signals, it is ineffective for data transmissions required by the Internet. none of the available options are true. none of the available options are true. it is incompatible with most modern communication systems. it is incompatible with most modern communication systems. systems used by many providers require customers to share bandwidth with neighbors. systems used by many providers require customers to share bandwidth with neighbors.
Answers
Answer:
systems used by many providers require customers to share bandwidth with neighbors
Explanation:
One of the disadvantages of cable technology is that systems used by many providers require customers to share bandwidth with neighbors. This ultimately causes many problems since cables would need to be extended to reach every single user that will be sharing the bandwidth. This would mean cables all over the place. Also, it is very difficult to limit the bandwidth per person, meaning that if anyone is using up all of the bandwidth through the cable, the rest of the individuals connected would not have the bandwidth that they need or are paying for.
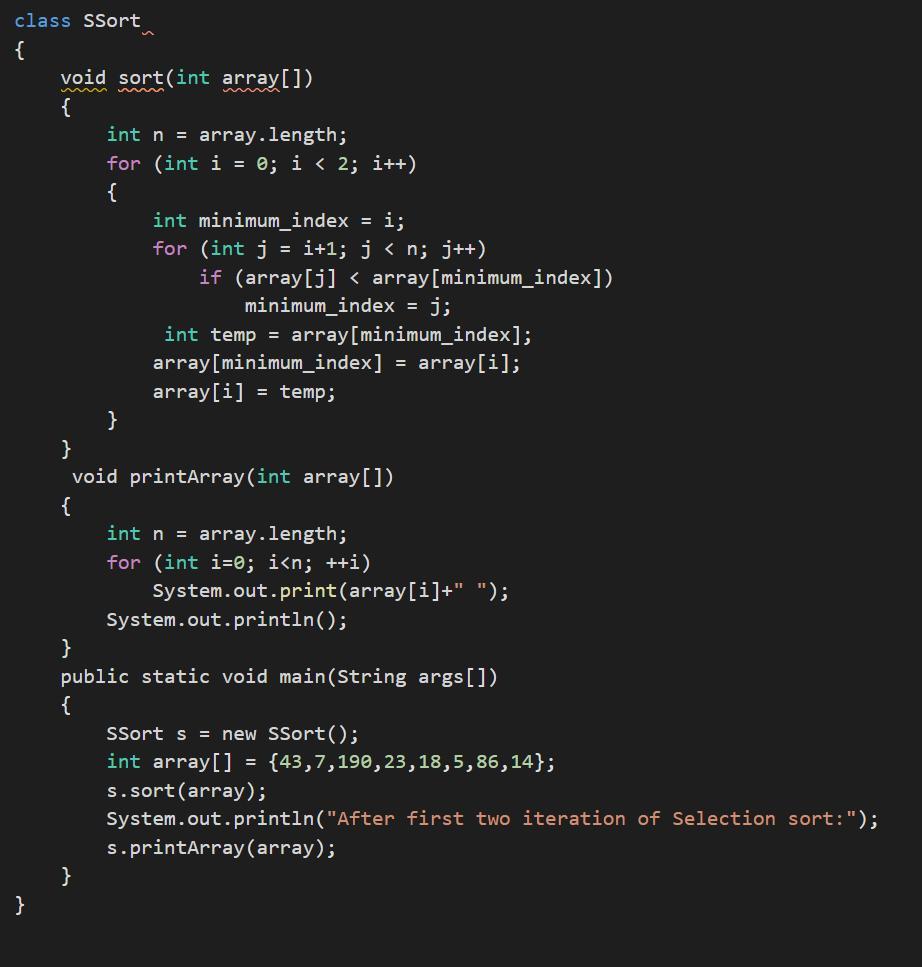
Show the contents of the array {43, 7, 190,23,18, 5,86,14} (sort in ascending order) after the first two iterations of Selection Sort. How many comparisons would be needed to sort an array containing 10 elements using Bubble sort in the worst case
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that organizes the values in larger and smaller in arguments.
Writing the code in JAVA we have:class SSort
{
void sort(int array[])
{
int n = array.length;
for (int i = 0; i < 2; i++)
{
int minimum_index = i;
for (int j = i+1; j < n; j++)
if (array[j] < array[minimum_index])
minimum_index = j;
int temp = array[minimum_index];
array[minimum_index] = array[i];
array[i] = temp;
}
}
void printArray(int array[])
{
int n = array.length;
for (int i=0; i<n; ++i)
System.out.print(array[i]+" ");
System.out.println();
}
public static void main(String args[])
{
SSort s = new SSort();
int array[] = {43,7,190,23,18,5,86,14};
s.sort(array);
System.out.println("After first two iteration of Selection sort:");
s.printArray(array);
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1