All of the following are specific security challenges that threaten the communications lines in a client/server environment except:
A) errors.
B) tapping.
C) theft and fraud.
D) radiation.
E) sniffing.
Answers
All of the following are specific security challenges that threaten the communications lines in a client/server environment except Radiation.
What is Radiation?
Radiation is energy that moves from one location to another in the form of waves or particles. In our day to day lives, we are always exposed to radiation.
The sun, microwave ovens in our kitchens, and radios we listen to in our cars are all common sources of radiation. The vast majority of this radiation poses no threat to our health.
However, some do. In general, radiation poses a lower risk at lower doses but can pose a higher risk at higher doses. Depending on the type of radiation, different precautions must be taken to protect our bodies and the environment while still allowing us to benefit from its numerous applications.
To learn more about Radiation, visit: https://brainly.com/question/10023527
#SPJ4
Related Questions
Which example best describes an unethical use of computers?
A. Individuals create fake identities in order to trick recipients into
giving them money or private data.
B. Teachers record attendance, grades, assignments, and student
progress in a school database.
O C. High school seniors submit applications to colleges that include
their written essay responses.
D. A coach organizes players' positions on the field and the batting
order of the team.
Answers
Th most unethical use of computers is when individuals create fake identities in order to trick the recipients for giving money or private data. Thus, option A. is correct.
What is unethical behavior or use?The unethical behavior or use means using the electronic device for wrong purpose. It is for performing such an activity that is against the rules of society and harmful for general public.
The computer can be easily used unethically by the hackers or computer experts for fetching personal data of general public. These hackers uses different and fake identities to target the innocent public easily.
Therefore, Option A is correct. The best example for an unethical use of computer is by the individuals who create fake identities.
Learn more about unethical behavior, here:
https://brainly.com/question/14701608
#SPJ5
Which tool is used by an administrator to manage many routers and provide an overall view of all the network? group of answer choices
Answers
A tool which is used by an administrator to manage many routers and provide an overall view of all the network is called: C. Network Management System (NMS).
What is a router?A router can be defined as a network device (node) that is designed and developed to connect two (2) different computer networks together, in order to allow them communicate by forwarding and receiving packets.
In Computer Networking, a Network Management System (NMS) simply refers to a tool which is designed and developed to be used by a network administrator in order to manage several routers while providing an overall view of all the network.
Read more on router here: brainly.com/question/24812743
#SPJ1
Complete Question:
Which tool is used by an administrator to manage many routers and provide an overall view of all t.
A. traceroute
B. ping
C. Network Management System (NMS)
D. MTR
how can i stop sharing my location without someone knowing
Answers
To stop sharing your location without someone knowing, follow these steps:
1. Access your device's location settings: On Android, go to Settings > Location. On iOS, go to Settings > Privacy > Location Services.
2. Find the app or service sharing your location: Look for the app or feature that shares your location with the person in question, such as "Find My Friends" on iOS or " Maps" on Android.
3. Disable location sharing: For iOS, select the app and toggle off "Share My Location." On Android, open the app, find the sharing settings, and disable the sharing feature.
4. Turn off location services (optional): If you want to be extra cautious, disable location services altogether.
Remember, communication is key. Discuss privacy preferences with the person involved to establish mutual understanding and avoid misunderstandings.
learn more about sharing your location here:
https://brainly.com/question/27835027
#SPJ11
One definition of culture suggests that culture is everything you think, everything you do and
everything you possess. The drawing of a cultural system mirrors that definition. In the
drawing, everything you think is represented by:
Technology
Social
Institutions
Ideology
The rectangle
Answers
The drawing that usually represent culture is ideology. The correct option is D.
What is ideology?An ideology is a set of beliefs or philosophies attributed to a person or group of people, particularly those held for reasons other than epistemic ones, in which "practical elements are as prominent as theoretical ones."
Ideology is a type of social or political philosophy in which practical as well as theoretical elements are prominent. It is an idea system that seeks to both explain and change the world.
Culture can be defined as all of a population's ways of life, including arts, beliefs, and institutions that are passed down from generation to generation.
It has been defined as "an entire society's way of life." As being such, it includes etiquette, dress, language, religion, rituals, and art.
Thus, the correct option is D.
For more details regarding ideology, visit:
https://brainly.com/question/24353091
#SPJ1
For questions 1-3, consider the following code:
x = int (input ("Enter a number: "))
if x 1 = 7:
print("A")
if x >= 10:
print("B")
if x < 10:
print("C")
if x % 2 == 0:
print("D")
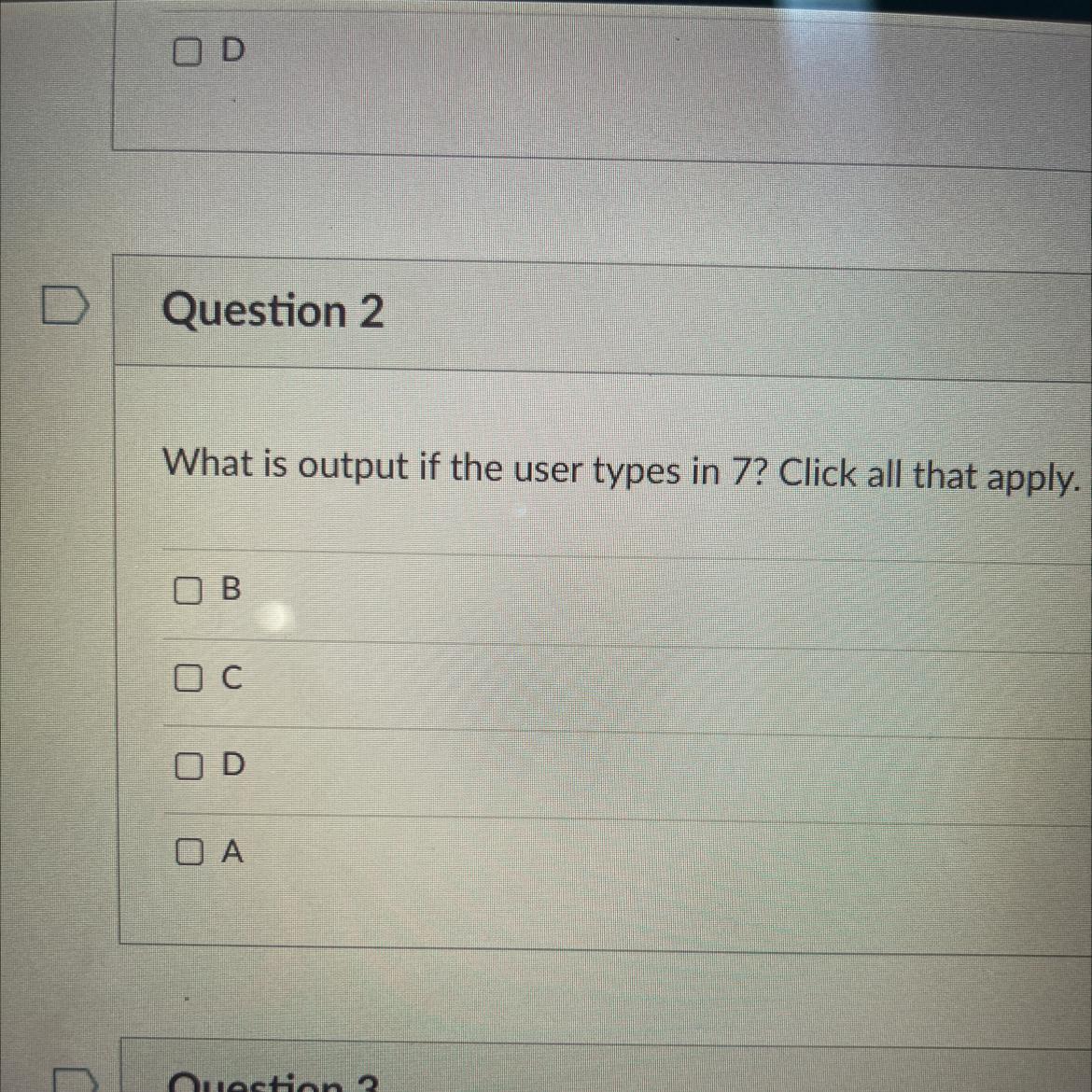
Answers
A user and a program might need to exchange messages. It might do this to display the program's results or to ask for more data so that it can function. This is referred to as output and is frequently displayed as text on the user's screen.
What do you mean by Python's input and output?The print() method in Python is used to output data to the screen. We may occasionally want to solicit user input. We can use the input() function to accomplish this. By default, Python treats every input as a string input. We must explicitly transform the input in order to convert it to any other data type.Program Justification: defining a variable "x" that accepts an integer value using the input method and the int type.Defining several if statements to examine the input valueIn the first, if the input value is less than 7, it is verified, and if it is true, the message "A" is printed.In the second, if the input value is larger than 10 and the condition is true, the message "B" will be printed.In the third, if the input value is less than 10, and it is, the message "C" will be printed.The message "D" will be printed in the fourth if it determines that the input value is an odd integer, which it does.Program:
x = int (input ("Enter a number: "))#defining a variable x that inputs value
if (x != 7):#use if that check value not equal to 7
print ("A")#print message
if (x >= 10):#use if that check value greater than equal to 10
print ("B")#print message
if (x < 10): #use if that check value less than 10
print ("C")#print message
if (x % 2 == 1):#use if that check value %2 equal to 1
print ("D")#print message
To Learn more about Python output refer to :
https://brainly.com/question/26497128
#SPJ1
The way a student prepares for a test or reviews academic material is referred to as
a study environment.
study habits.
study hall.
a study schedule.The way a student prepares for a test or reviews academic material is referred to as
Answers
Answer:
study habits
Explanation:
Answer:
The Answer is Study Habits
Explanation:
Just got it right on edge
By clicking on totals in the show/hide group of the query design ?
A. A new column will appear In the data
B. A new row will show in the design grid
C. All of the numbers will be added
D. Selected numbers will be totaled
Answers
D. Selected numbers will be totaled.
Clicking on "Totals" in the Show/Hide group of the query design in Microsoft Access will add a Totals row to the query design grid. This Totals row will allow you to specify aggregate functions (such as SUM, COUNT, AVG, etc.) for selected fields in the query. When you run the query, the selected numbers will be totaled or aggregated according to the function specified.
Learn more about count here:
brainly.com/question/32059027
#SPJ11
A for statement usually contains three expressions: initialization, test, and __________________. Group of answer choices relational expression summation declaration update answer
Answers
A for statement usually contains three expressions: initialization, test, and update. The three expressions in a for statement, namely initialization, test, and update, work together to define the loop's behavior and control its execution.
In the syntax of a for statement, there are typically three expressions separated by semicolons. These expressions serve different purposes in controlling the execution of the loop:
Initialization: This expression is executed before the loop starts and is used to initialize any variables or set up the initial conditions required for the loop.
Test: Also known as the condition or relational expression, this expression is evaluated at the beginning of each iteration of the loop. If the test evaluates to true, the loop continues executing. If it evaluates to false, the loop terminates, and control passes to the next statement after the loop.
Update: This expression is executed at the end of each iteration of the loop. It is typically used to update the loop control variable or perform any necessary changes to the loop state for the next iteration.
Together, these three expressions control the flow and behavior of the for loop, ensuring that the loop executes for a specified number of times or until a certain condition is met.
Understanding and properly configuring these expressions is essential for designing effective loops in programming.
To learn more about loop, visit
brainly.com/question/26568485
#SPJ11
benefits of programming
Answers
Answer:
It develop problem-solving skills.Encourages curiosity.Learning to code helps a students' creativity also.Also can improve carreer prospects. It teaches collaboration.Convert your assigned decimal number to IEEE754 Single Precision Floating Point Format. Show your complete solution labelling all necessary variables and results. Round your answer if necessary, using 3 guard bits. E. 9.648
Answers
This below discussed process allows us to represent decimal numbers as binary floating-point numbers in a standardized format.
To convert a decimal number to IEEE754 Single Precision Floating Point Format, we follow these steps:
Step 1: Determine the sign of the number. For positive numbers, the sign bit is 0, and for negative numbers, it is 1.
Step 2: Convert the decimal number to binary. For example, 9.648 becomes 1001.10100100.
Step 3: Normalize the binary number by moving the decimal point to the left until there is only one digit to the left of the binary point. In this case, it becomes 1.00110100100.
Step 4: Determine the exponent. Count the number of places the decimal point was moved. In this case, it is 3. Add the bias (127) to the exponent to get the final value. 3 + 127 = 130. Convert 130 to binary, which is 10000010.
Step 5: Combine the sign, exponent, and mantissa. The sign bit is 0 (positive number). The exponent is 10000010, and the mantissa is the normalized binary number without the leading 1 (00110100100).
So, the IEEE754 Single Precision Floating Point representation of 9.648 is:
0 10000010 00110100100000000000000
Note: The above representation is in binary. For a decimal representation, it becomes:
0 10000010 00110100100000000000000 (in scientific notation: 1.00110100100000000000000 x 2¹³⁰)
This process allows us to represent decimal numbers as binary floating-point numbers in a standardized format.
To know more about decimal number, visit:
https://brainly.com/question/4708407
#SPJ11
Need answer to 13.1.1 codehs

Answers
Using the knowledge in computational language in python it is possible to write a code that have to make a half pyramid out of circle's need to have a function, a variable named circle_amount.
Writting the code:speed(0)
circle_amount = 8
def draw_circle():
pendown()
circle(25)
penup()
forward(50)
def move_up_a_row():
left(90)
forward(50)
right(90)
backward(circle_amount*50)
penup()
setposition(-175,-200)
for i in range(circle_amount):
for i in range(circle_amount):
draw_circle()
move_up_a_row()
circle_amount = circle_amount - 1
See more about python at brainly.com/question/19705654
#SPJ1

Which of the following describes organizations that
self-regulate via feedback loops?
Group of answer choices
Cybernetics
Chaos Theory
Scientific Management
Classical Organization Theory
Answers
Organizations that self-regulate via feedback loops can be described as applying principles of cybernetics.
Cybernetics is a field that deals with systems and control processes, specifically focusing on the study of feedback loops and self-regulation. Organizations that employ self-regulation through feedback loops can be seen as applying cybernetic principles to their operations. In this context, feedback loops refer to the process of gathering information about a system's performance, comparing it to desired outcomes, and making necessary adjustments to achieve those outcomes.
By using feedback loops, organizations can monitor their activities, evaluate their performance, and make continuous improvements. Feedback loops involve collecting data, analyzing it, and using the insights gained to adjust behaviors, processes, or strategies. This iterative process enables organizations to adapt to changes, optimize their performance, and achieve desired outcomes.
In summary, organizations that self-regulate via feedback loops can be understood as implementing principles from cybernetics. They utilize feedback mechanisms to monitor and adjust their operations, aiming to improve performance and achieve their goals.
Learn more about Cybernetics here:
https://brainly.com/question/32095235
#SPJ11
write a program limited to the instructions provided in the cornell interpreter used in class. the string will not exceed 9 characters. it is the verification of a possible palindrome. display a 0 in a register that i will specify the day of the presentation (if any is required) if it is not and a 1 if it is. the string will be stored in memory location 0x8000. comments will be needed to justify the usage of any instruction.
Answers
Two important concerns that the IT technician must discuss with the customer in order to determine if the OS upgrade can be done are:
1.Compatibility of existing applications and custom software with the new OS: The IT technician needs to check if all the existing applications and custom software used by the customer are compatible with Windows 10. Some older applications may not be compatible with the newer operating system, and upgrading could result in functionality issues or even data loss.
2.Minimum memory and processor requirements for Windows 10: The IT technician needs to check if the older computers meet the minimum hardware requirements for running Windows 10. Windows 10 requires more system resources than Windows XP, so the customer's computers may need to be upgraded with additional memory or processor upgrades to handle the new OS efficiently.
To know more about IT technician click this link -
brainly.com/question/14290207
#SPJ11
Define "the Internet" in your own words.
Answers
Answer it is freedom for everyone
Explanation:
Answer:
the internet is a place that has information about anything like how to's or scientific facts.
Explanation:
Who is the CEO of Epic Games?
Answers
Answer:
it's tim sweeney....
Explanation:
hope it helps
Answer:
Tim Sweeney
Explanation:
some critics aruge that excessive media consumption can encourage______.
A. deeper reading
B. taking breaks from using digital media
C an unhealthy lifestyle
D. healthy friendships
Answers
A Question 1 (3 points) Retake question Listen ▶ Lyrics, melodies and underlying musical notes all refer to the.... sound recording copyright music copyright master recording mechanical license
Answers
Lyrics, melodies, and underlying musical notes all refer to the music copyright.
Copyright is the legal right that belongs to an artist, publisher, or producer to be the sole user of a literary, musical, dramatic, or artistic work. Copyright laws grant creators of original works exclusive rights to the use, distribution, and display of their works. Copyright infringement happens when someone uses a creative work without the owner's permission.
In the context of music, the term "copyright" refers to the protection provided to original songs and music compositions. Lyrics and musical notes that make up a song are both protected by copyright. This means that anyone who wishes to use, record, or reproduce the song or composition must first acquire the necessary rights or licenses.
The mechanical license, master recording, and sound recording copyright are all related to the music industry and refer to different types of licenses and rights granted to music producers, artists, and copyright owners.
The mechanical license is granted to anyone who wants to create a cover or new version of a song. The master recording refers to the final version of a song that is used for commercial purposes, and the sound recording copyright refers to the protection provided to the sound recording of a song or musical composition.
To learn about copyright here:
https://brainly.com/question/357686
#SPJ11
which of the following online creation tools will be used if a person wants to create a video presentation?
a. Piktochart
b. Prezi
c. Powtoon
d. Zamzar
Answers
Answer:
C
Explaination:
Powtoon
I need help with this :(( In java
Write a program that has a user guess a secret number between 1 and 10.
Store the secret number in a variable called secretNumber and allow the user to continually input numbers until they correctly guess what secretNumber is.
For example, if secretNumber was 6, an example run of the program may look like this:
I'm thinking of a number between 1 and 10.
See if you can guess the number!
Enter your guess: 4
Try again!
Enter your guess: 3
Try again!
Enter your guess: 1
Try again!
Enter your guess: 10
Try again!
Enter your guess: 6
Correct!
Note:
Make sure that the the secretNumber is 6 when you submit your assignment! It will only pass the autograder if the value is 6.
Answers
Java is an object-oriented coding software used to develop software for a variety of platforms.
What does programmer do in Java?When a programmer creates a Java application, the compiled code is compatible with the majority of operating systems (OS), including Windows, Linux, and Mac OS.
For writing a program that has a user guess a secret number between 1 and 10 it can be done as follows:
import random
secretNum = random.randint(1,10)
userNum = int(input("Take a guess: "))
while(userNum != secretNum):
print("Incorrect Guess")
userNum = int(input("Take a guess: "))
print("You guessed right")
Thus, by using this program, one can execute the given condition.
For more details regarding Java, visit:
https://brainly.com/question/12978370
#SPJ1
A fundamental part of market research is studying what your competitors have done so that you don't copy anything from those projects and create something wholly original.
A.
True
B.
False
Answers
Answer:
I'll go with option A. True. Hope this helps please mark me BRAINLIEST
Constraints for mining headgear
Answers
Learn more:
brainly.com/question/18293588
What does the frame rate of a Virtual Reality headset indicate?A. the number of users connected to the applicationB. the resolution and quality of the displayC. the strength of the device's internet connectionD. the number of images displayed per second
Answers
The frame rate of a Virtual Reality headset indicates the number of images displayed per second. Thus, the correct option for this question is D.
What is a Virtual Reality headset?A Virtual Reality headset may be characterized as a type of heads-up display (HUD) that significantly permits users to interact with simulated environments and experience a first-person view (FPV).
Frame rate refers to the speed at which successive images are expressed. It is usually expressed as “frames per second,” or FPS. According to scientific research, the standard frame rate of 24fps is used in movies, TV broadcasts, streaming video material, and even smartphones.
Therefore, the frame rate of a Virtual Reality headset indicates the number of images displayed per second. Thus, the correct option for this question is D.
To learn more about Frame rate, refer to the link:
https://brainly.com/question/29590566
#SPJ1
1. Word Module 2 SAM Textbook Project
2. Word Module 2 SAM Training
3. Word Module 2 SAM End of Module Project 1
4. Word Module 2 SAM End of Module Project 2
5. Word Module 2 SAM Project A
6. Word Module 2 SAM Project B
Answers
The raise To Power Module of the program's calling error can be found in the real and integer values of the argument variables.
String should be spelled Sting. The set Double Module instead of returning an integer, does such. Access to local variables declared in the Main module is restricted to that module only. The raise To Power Module of the program's calling argument variables' real and integer values can be used to pinpoint the issue. Although the arguments for the raise To Power Module (Real value and Integer power) have been defined. The integer power is represented as "1.5," and the real value is supplied as "2." A real number, on the other hand, is a number with a fractional part. thus, a number without a fraction is considered an integer. 1.5 is a real number, whereas 2 is an integer. The parameters' contents when invoking raise To Power.
Learn more about The raise To Power Module here:
https://brainly.com/question/14866595
#SPJ4
This logo bby im sorry huhu

Answers
Answer:
I believe this was for someone else online, Unfortunately that's a little weird to be dating here ya know, Never know if there is someone really old or young you could be dating.
Which tools do meteorologists use to collect data about the weather?
satellites
weather fronts
maps and charts
isolines
Answers
A satellite is a tool that the meteorologists use to track the weather and environmental conditions on Earth.
What is a satellite?Satellites are devices that trace orbits around our planet and are used for weather monitoring.
Uses of satellites in weatherThey are constantly used to monitor weather, clouds, approaching storms, and brewing hurricanes.They capture the movement of clouds and their behavior, and serve to collect all possible information about the environment and the conditions of the Earth's atmosphere that can affect large areas of the Earth's surface.Therefore, we can conclude that a satellite collects and transmits meteorological information.
Learn more about uses of satellites in weather here: https://brainly.com/question/7115770
Answer:
A
Explanation:
You are researching the Holocaust for a school paper and have located several Web sites for information.In three to five sentences, describe the method you would use to determine whether each Web site is a suitable source of information for your paper.
Answers
I suggest the following methods to determine whether a website is a suitable source of information for a school paper on the Holocaust:
The MethodCheck the credibility of the website by examining the author's qualifications, credentials, and institutional affiliation.
Evaluate the accuracy of the information by comparing it with other reliable sources on the same topic.
Check the currency of the information by looking at the date of publication or last update. Avoid using outdated information.
Analyze the objectivity of the website by checking for any bias or slant towards a particular perspective or ideology.
Lastly, check the website's domain name and extension to verify its origin, as some domains may have questionable reputations.
Read more about sources here:
https://brainly.com/question/25578076
#SPJ1
A single line text input control with an initial value as +971
Answers
Answer:
What's about this initial value equal to 971
Explanation:
\(\sqrt{2}\)

for Jenny's personal computer?
id videos. Which operating
system would be appropriate Jenny's needs to buy a computer to create word documents, make presentations, listen to music, and watch movies and videos.
OA. UNIX
O B. Linux
O C. Microsoft Windows
O D. MS-DOS
Answers
Answer: C
Explanation: Microsoft Windows would be the most viable option here because UNIX and Linux are used for server-side applications, and MS-DOS is an old operating system which is not supported anymore. There is also the Microsoft 365 suite on Microsoft Windows, which can allow Jenny to make presentations using powerpoint, and edit videos.
5.7 AP-Style MC Practice edhessive
In Fantasy Football, participants compete against one another by choosing certain players from different NFL teams that they think will do the best on any particular week. Top Fantasy Football players spend hours every day looking at huge databases of statistics related to the players and the teams often using spreadsheets and software tools to gain new insights and choose the best players. This process could be considered an example of which of the following?
(DATA MINING)
Students are using data collected from a non-profit organization to try to convince the school board that their school should be in session year-round with several week-long breaks as opposed to the usual 9 months on and 3 months off. Information that was collected by this organization was as follows.
The location of the school (city and country)
The number of students at the school
Whether it was year-round or had the normal 3-month summer break
Scores on standardized tests (AP, SAT, ACT, etc)
The student handbook of rules and regulations
Results from a survey from teachers and students about happiness level and motivation level
They decided to make an infographic in order to try to easily display the data they had analyzed. Which of the following would be the best information to put on their infographic to try to convince the school board to change the schedule?
Select two answers.
(Association rules showing links between motivation and happiness levels and the type of schooling students were receiving.)
(A regression analysis of standardized tests scores comparing the two different types of schooling.)
Which of the following terms describes the conversion of data, formatted for human use, to a format that can be more easily used by automated computer processes?
(Screen Scraping
Answers
Answer:
1. Data Mining
2. A regression analysis of standardized tests scores comparing the two different types of schooling. || Association rules showing links between motivation and happiness levels and the type of schooling students were receiving.
3. Screen Scraping
Explanation:
1. The data analyze big data sets to gain insight, which a person can't do, so it is data mining.
2. A regression analysis shows the mathematical relationship between two variables. Association rule mining finds features of data points which determine the results of other features.
3. Screen scraping generally refers to process recordings.
Richard wants to share his handwritten class notes with Nick via email. In this scenario, which of the following can help Richard convert the notes into digital images so that he can share them via email? a. Bar coding device b. Digital printing software c. Document scanner d. Radio frequency identification tag
Answers
Answer: Document Scanner
Explanation: Cos then he can easily add the paper notes to his computer and email the client.