before the scientific revolution, to understand nature, europeans relied on text to speech
T/F
Answers
before the scientific revolution, to understand nature, europeans relied on text to speech True
Europeans did not have access to the modern scientific methods and technologies that we have today. They relied heavily on written texts and oral traditions to understand and explain the natural world. Many of these texts were based on the ideas of ancient Greek philosophers, such as Aristotle and Plato, and were interpreted through the lens of Christian theology. The dominant worldview of the time saw nature as a reflection of the divine order, and therefore the study of nature was seen as a means to understand God's plan. This reliance on text and traditional knowledge began to shift during the Scientific Revolution, as new scientific methods were developed and empirical observations were emphasized over reliance on authority and tradition.
To know more about scientific revolution visit:
brainly.com/question/30347427
#SPJ11
Related Questions
1) Man should feed ______ to a computer in order to improve the efficiency of computer vision.
pls plz help me
Answers
Answer:images
Explanation:i saw this on the quizlet for my school
Who should you not contact if you think you are the victim of identity theft or fraud?
Answers
which installation methods require booting into windows pe before windows 10 starts? (choose all that apply.)
Answers
Answer:
Distribution share installation
Image-based installation
Which of the following statements are true of software engineers? Check all of the boxes that apply. They are responsible for writing programming code. They are usually strong problem-solvers. They spend most of their work hours running experiments in a laboratory. They must hold advanced degrees in computer science.
Answers
Answer:
First two statements: yes. Last two: not so much.
But many of the better ones do have advanced degrees, but some don't.
The laboratory statement is silly; they sit behind a set of screens figuring out stuff and writing code.
It should be noted that statements are true about software engineers are;
They are responsible for writing programming code. They are usually strong problem-solvers.Software engineering can be regarded as branch of computer science which is responsible for the development as well as the building of computer softwares, these could be applications software or system software.
The engineers that carry out this process is referred to as software engineers and they are responsible for responsible for writing programming code.
We can conclude that software engineers are strong problem-solvers.
Learn more about software engineer at:https://brainly.com/question/25757629
18379013?answering=%2FhomePage%2F22 x 2 tothe power of 12
Answers
Answer:
Can you rephrase that please
What potential problems could come up if I tried to use a function without knowing what it does or how to interact with it?
Answers
Answer:
You won't get the result you are expecting. Or you may get a result, you just don't know what it represents. Or the function could do any number of other things that may effect values already stored in the instance of the class that you weren't intending. It all depends on what the function is and how dependent other things are on it.
Answer:
My friend wants to use my findSmallest() function in her program. Is this function ready to be shared in a library? Why or why not? This is the answer to the next question.
Explanation:
No, this code is not ready to be shared in a library. This is because this code has a global variable that will only allow the code to work for one case and cannot be applied to other problems my friend might have. This function also does not have a return call which will result in no answer when fed with an input.
Which button is not present in the font group Home tab?
-B
-U
-I
-D
Answers
Answer:
-i
Explanation:
is the answer of that question
Answer:
D
Explanation:
This is because B which is bold, U which is underline and I which is italic are present in the font group home tab but D isn`t
Alice just wrote a new app using Python. She tested her code and noticed some of her lines of code are out of order. Which principal of programing should Alice review?
Hand coding
Line coding
Planning & Analysis
Sequencing
Answers
Answer:
Sequencing
Explanation:
I have taken the test
Corinne would like to click on the link at the bottom of a Web page but she only sees the top portion of the page. She should _____. A.click twice on the status bar
B.use the scroll bar to scroll down to the bottom of the page
C.click on the back button
D.click on the display window and drag it up
Answers
Answer:
B
Explanation:
from 3dg3
Answer:
D.click on the display window and drag it up
Jane, an employee at your company, has just opened an online chat with you. Jane states that although she has access to the internet, she cannot access either her email or her calendar. Jane just started her job in marketing today, and she is very flustered and does not know what to do.
Jane’s manager just gave her a project to research competitive ads to help inform a new campaign. She had taken a lot of notes in a Word document, and now she cannot find that document either. She was supposed to have the project sent over to her manager by the end of the day.
Jane is very nervous that she is going to get into trouble with her manager on her first day of work. She is sharing all of this with you in the online chat box.
What do you do?
Answers
In this situation, it is important to provide Jane with guidance and support to help her address the issues she's facing. By providing guidance, reassurance, and practical solutions, I can help alleviate Jane's concerns and guide her toward resolving the technical issues she is facing on her first day of work.
Here's what you can do:
Reassure and empathize: Start by reassuring Jane that you understand her concerns and that technical difficulties can happen to anyone. Let her know that you are there to help and that you will work together to find a solution.Troubleshooting assistance: Ask Jane to provide more details about the specific issues she is experiencing with her email, calendar, and the missing Word document. Offer step-by-step troubleshooting guidance, such as checking internet connectivity, restarting her computer, or verifying email and calendar settings.IT support contact: If the issue persists or seems to be beyond your expertise, provide Jane with the contact information for the IT support team at your company. Advise her to reach out to them for further assistance, explaining that they are trained to handle technical issues efficiently.Document recovery options: Assure Jane that there are potential ways to recover her lost Word document. Suggest checking the document recovery feature in Microsoft Word, looking for temporary or autosaved versions of the file, or utilizing file recovery tools if available.Communicate with her manager: If Jane is genuinely concerned about her manager's expectations, offer to communicate with her manager on her behalf. Assure Jane that you will explain the technical difficulties she encountered and the steps she has taken to resolve them. Emphasize that her manager will appreciate her proactive communication.Follow-up and support: After providing initial guidance, follow up with Jane to check if she was able to resolve the issues or if she needs further assistance. Offer ongoing support and encourage her to reach out if she encounters any additional challenges.Remember to remain calm, supportive, and understanding throughout the interaction.
For more questions on guidance
https://brainly.com/question/839980
#SPJ8
help me pleaseeeeeeee

Answers
Answer:
I think you have to ask to your parents
when a single network server can't handle all the data processing requests, more servers can be added and joined together to create a . choose all that apply, then click done.
Answers
what are the answer choices??
----------------------------
Please summarize into 1.5 pages only
----------------------------
Virtualization
Type 2 Hypervisors
"Hosted" Approach
A hypervisor is software that creates and runs VM ins
Answers
Virtualization: It is a strategy of creating several instances of operating systems or applications that execute on a single computer or server. Virtualization employs software to reproduce physical hardware and create virtual versions of computers, servers, storage, and network devices. As a result, these virtual resources can operate independently or concurrently.
Type 2 Hypervisors: Type 2 hypervisors are hosted hypervisors that are installed on top of a pre-existing host operating system. Because of their operation, Type 2 hypervisors are often referred to as "hosted" hypervisors. Type 2 hypervisors offer a simple method of getting started with virtualization. However, Type 2 hypervisors have some limitations, like the fact that they are entirely reliant on the host operating system's performance.
"Hosted" Approach: The hosted approach entails installing a hypervisor on top of a host operating system. This hypervisor uses hardware emulation to create a completely functional computer environment on which several operating systems and applications can run concurrently. In general, the hosted approach is used for client-side virtualization. This method is easy to use and is especially useful for the creation of virtual desktops or the ability to run many operating systems on a single computer.
A hypervisor is software that creates and runs VM instances: A hypervisor, also known as a virtual machine manager, is software that creates and manages virtual machines (VMs). The hypervisor allows several VMs to execute on a single physical computer, which means that the computer's hardware can be utilized more efficiently. The hypervisor's role is to manage VM access to physical resources such as CPU, memory, and I/O devices, as well as to provide VM isolation.
Know more about virtualization, here:
https://brainly.com/question/31257788
#SPJ11
What does this mean
Don't use such phrases here, not cool! It hurts our feelings :(
Answers
how do I open this thing? it is stuck

Answers
Answer:
the little button
Explanation:
The Internet is a(n) ______
made up of wires, cables, satellites, and rules for exchanging information between computers connected to the network.
A. Physical network
B. Virtual network
C. Multimedia interface
D. Domain name
Answers
Answer:
The Internet is a(n) B. Virtual network made up of wires, cables, satellites, and rules for exchanging information between computers connected to the network.
Explanation:
2 points
1. Which characters are normally used to represent the root of the Floppy
disk drive? *
a) C1
b) A:
c) B:
d) D:
points
Answers
Answer:
B) A:
Explanation:
Was a first to invent rule applied to patents filed before March 16th, 2013?
Answers
Answer:
No read # 1
Explanation:
the three major changes in the New Law which have heightened the importance of early filing are 1) the first party to file an application on an invention is entitled to a patent that issues on the invention, regardless of who is first to invent; 2) the important date for most prior art activities and documents becomes the filing date of an application as opposed to the date of invention as under the pre-March 16, 2013 law (Current Law); and 3) the general one-year grace period that currently allows an inventor to file a patent application within one year of a public disclosure, sale or offer for sale of an invention is eliminated. These three changes are explained in more detail below.
What is the output of the following line of code? print (“I\tLove Python”)
Answers
Answer: it will print:
I (4 spaces) Love Python
Explanation: the \t adds in a tab (4spaces) in a print statement


What is the output of the sum of 1001011 and 100011 displayed in hexadecimal?
Answers
Answer:
\(1001011_2\) \(+\) \(100011_2\) \(=\) \(6E_{hex}\)
Explanation:
Required
\(1001011_2 + 100011_2 = []_{16}\)
First, carry out the addition in binary
\(1001011_2\) \(+\) \(100011_2\) \(=\) \(1101110_2\)
The step is as follows (start adding from right to left):
\(1 + 1 = 10\) --- Write 0 carry 1
\(1 + 1 + 1(carry) = 11\) ---- Write 1 carry 1
\(0 + 0 + 1(carry) = 1\) ---- Write 1
\(1 + 0 = 1\) --- Write 1
\(0 + 0 = 0\) ---- Write 0
\(0 + 0 = 0\) ---- Write 0
\(1 + 1 = 10\) --- Write 0 carry 1
No other number to add ; So, write 1 (the last carry)
So, we have:
\(1001011_2\) \(+\) \(100011_2\) \(=\) \(1101110_2\)
Next, convert \(1101110_2\) to base 10 using product rule
\(1101110_2 = 1 * 2^6 +1 * 2^5 + 0 * 2^4 + 1 * 2^3 + 1 * 2^2 + 1 * 2^1 + 0 * 2^0\)
\(1101110_2 = 64 +32 + 0 + 8 + 4 + 2 + 0\)
\(1101110_2 = 110_{10}\)
Lastly, convert \(110_{10}\) to hexadecimal using division and remainder rule
\(110/16 \to 6\ R\ 14\)
\(6/16 \to 0\ R\ 6\)
Write the remainder from bottom to top;
\(110_{10} = 6(14)_{hex}\)
In hexadecimal
\(14 \to E\)
So, we have:
\(110_{10} = 6E_{hex}\)
Hence:
\(1001011_2\) \(+\) \(100011_2\) \(=\) \(6E_{hex}\)
Which of the following is a way to keep you safe online? (select all that apply)
set up a spam folder
give out personal information to strangers
only open e-mails from people you know
keep anti-virus software up to date
Answers
Answer:
1). set up a spam folder
3).only open e-mails from people you know
4).keep anti-virus software up to date
Explanation:
IM DIFFERENT BREEED!
The options that are a way to keep you safe online are:
Set up a spam folder.Only open e-mails from people you know.Keep anti-virus software up to date.What ways can keep you safe online?When a person keep their personal information private and from online views, one can be able to keep themselves safe.
Conclusively, Note that a lot of Hackers do make use of the profile of people on social media and as such, doing the above things can help keep you safe.
Learn more about online from
https://brainly.com/question/2014724
#SPJ2
A Card class has been defined with the following data fields. Notice that the rank of a Card only includes the values from Ace - 10 (face cards have been removed):
class Card {
private int rank; // values Ace (1) to 10
private int suit; // club - 0, diamond - 1, heart - 2, spade - 3
public Card(int rank, int suit) {
this.rank = rank;
this.suit = suit;
}
}
A deck of cards has been defined with the following array:
Card[] cards = new Card[40];
Which of the following for loops will populate cards so there is a Card object of each suit and rank (e.g: an ace of clubs, and ace of diamonds, an ace of hearts, an ace of spades, a 1 of clubs, etc)?
Note: This question is best answered after completion of the programming practice activity for this section.
a
int index = 0;
for (int suit = 1; suit < = 10; suit++) {
for (int rank = 0; rank < = 3; rank++) {
cards[index] = new Card (rank, suit);
index++;
}
}
b
int index = 0;
for (int suit = 0; suit < = 4; suit++) {
for (int rank = 0; rank < = 10; rank++) {
cards[index] = new Card (rank, suit);
index++;
}
}
c
int index = 0;
for (int rank = 1; rank <= 10; rank++) {
for (int suit = 0; suit <= 3; suit++) {
cards[index] = new Card (rank, suit);
index++;
}
d
int index = 0;
for (int suit = 0; suit < = 3; suit++) {
for (int rank = 1; rank < 10; rank++) {
cards[index] = new Card (rank, suit);
index++;
}
}
Answers
Answer: b
Explanation: i did this one!!!!!!!!!!
The answer to this problem
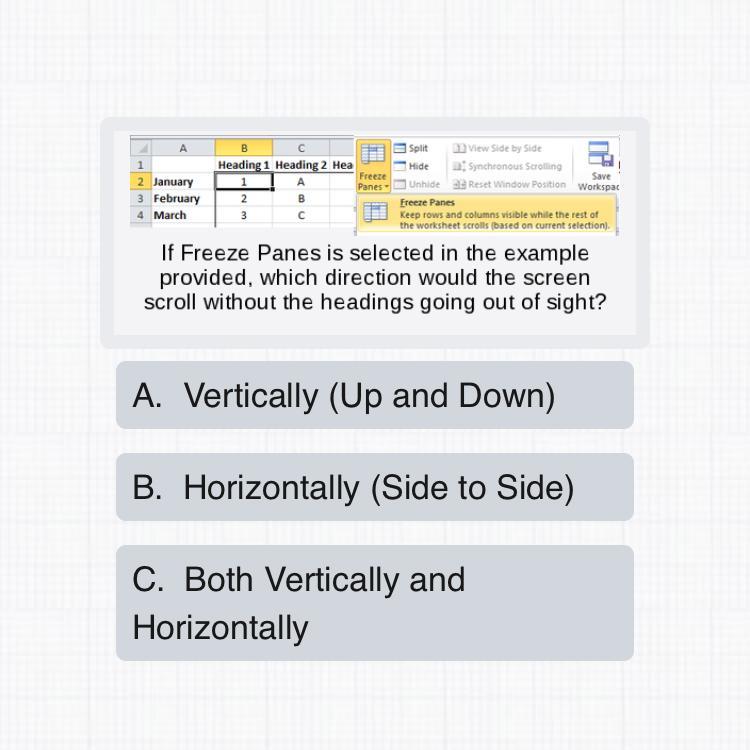
Answers
All _______ that store more than one piece of data
Answers
Answer:All data structure that store more than one piece of data
.
Explanation:
Signs and symbols can be used to communicate.
True
False
Answers
Answer:
True
Explanation:
There are two major categories of signals people send: signs and symbols. Signs are the foundation of all communication
Type the correct answer in the box. Spell all words correctly.
How can aspiring illustrators hone their skills?
Aspiring illustrators can hone their talent and skills using _____________ software.
Help asap
100 POINTS
Answers
Answer:
Aspiring illustrators can hone their talent and skills using Adobe Illustrator software.
Explanation:
By using this software we enroll graphics for out Television.Computer etc ..Earth’s axis is tilted to one side. Which phenomenon would cease to exist in the absence of this axial tilt?
Answers
The Earth rotation axis is inclined (or tilted) approximately 23.5º with respect to the plane of the orbit that it describes around the Sun.
If this inclination did not exist and the axis of the Earth were exactly perpendicular to the plane of its orbit around the Sun, day and night would always last twelve hours and every day of the year would be a perfect repetition of the previous one.
Therefore, the solstices (maximum difference in duration between day and night) or seasons would not exist.
Answer:
solstice
Explanation:
Plato correct answer!
1)Which tool can you use to find duplicates in Excel?
Select an answer:
a. Flash Fill
b. VLOOKUP
c. Conditional Formatting
d. Concatenation
2)What does Power Query use to change to what it determines is the appropriate data type?
Select an answer:
a.the headers
b. the first real row of data
c. data in the formula bar
3)Combining the definitions of three words describes a data analyst. What are the three words?
Select an answer:
a. analysis, analyze, and technology
b. data, programs, and analysis
c. analyze, data, and programs
d. data, analysis, and analyze
Answers
The tool that you can use to find duplicates in Excel is c. Conditional Formatting
b. the first real row of datac. analyze, data, and programsWhat is Conditional Formatting?Excel makes use of Conditional Formatting as a means to identify duplicate records. Users can utilize this feature to identify cells or ranges that satisfy specific criteria, like possessing repetitive values, by highlighting them.
Using conditional formatting rules makes it effortless to spot repeated values and set them apart visually from the other information. This function enables users to swiftly identify and handle identical records within their Excel worksheets, useful for activities like data examination and sanitation.
Read more about Conditional Formatting here:
https://brainly.com/question/30652094
#SPJ4
Question 21 pts How many lines should an email signature be? Group of answer choices "5 to 6" "7 to 8" "1 to 2" "3 to 4"
Answers
Answer:
"3 to 4"
Explanation:
Communication can be defined as a process which typically involves the transfer of information from one person (sender) to another (recipient), through the use of semiotics, symbols and signs that are mutually understood by both parties. One of the most widely used communication channel or medium is an e-mail (electronic mail).
An e-mail is an acronym for electronic mail and it is a software application or program designed to let users send and receive texts and multimedia messages over the internet.
An email signature can be defined as a group of texts (words) that a sender adds to the end (bottom) of his or her new outgoing email message. It is considered to be a digital business card that gained wide acceptance in the 21st century. Also, an email signature is a good etiquette in all formal conversations because it provide the recipient some level of information about the sender of an email message.
Ideally, an email signature should be three to four lines and must contain informations such as name, website address, company name, phone number, logo, catch phrase or quote, social icons, etc.
Additionally, you shouldn't place an email signature at the top or anywhere else in the email except at the bottom, immediately after the closing line.
List some of the icons present in Microsoft Windows 7 desktops.
Answers
Answer:
Common desktop icons include Computer, your personal folder, Network, the Recycle Bin, Internet Explorer, and Control Panel.
Explanation: