Can you predict the UDP length, given the echo command? If so, how?
echo -n "This is a longer message" | nc -u -w1 10.0.8.10 5060
udp length of this is 32
Answers
Yes, the UDP length can be predicted given the echo command. In this case, the UDP length is 32.
When the echo command is used, it sends an Internet Control Message Protocol (ICMP) request packet to a specified destination. The response to this request is an ICMP reply packet that includes the requested data. The reply packet is sent back to the originating source with a User Datagram Protocol (UDP) header that includes the length of the data in the packet.
Therefore, if the UDP length of the echo command is known, then the length of the data in the response packet can be predicted. In this case, since the UDP length of the echo command is 32, the length of the data in the response packet can be predicted to be 32 as well.
The Web Control Message Convention (ICMP) is a convention that gadgets inside an organization use to discuss issues with information transmission. According to this definition of ICMP, one of the primary purposes of the protocol is to ascertain whether or not data reaches its destination on time.
Know more about User Datagram Protocol, here:
https://brainly.com/question/31113976
#SPJ11
Related Questions
relational data warehouses use the star schema design technique to handle multidimensional data.
Answers
Relational data warehouses make use of star schema design technique to handle multidimensional data. Star schema has a central table, which is surrounded by a series of denormalized dimension tables.
The central table is also known as the fact table, and it contains all of the numeric data that is related to the transaction, such as sales data, purchase information, and inventory details. The surrounding dimension tables are the place where information about the facts is stored. The data in a star schema is normalized, but not to the extent that it is in a fully normalized data model.
In conclusion, the star schema is an excellent solution for managing and handling multidimensional data in a relational data warehouse. It is user-friendly and easy to navigate and makes it simple to analyze vast amounts of data.
To know more about design visit:
https://brainly.com/question/17147499
#SPJ11
A solid understanding of __________ is the foundation of verbal communication
Answers
Answer:
A solid understanding of spoken and written language is the foundation of verbal communication
Answer: Spoken and written language
Explanation:
List a future Internet and a future network technology that interests you. Explain what it is and how it works. Comment on another's post. You must post before you can see other's posts. Internet tech
Answers
Data is transmitted via light
You could have streetlights transmit data to cars.
Since you just need the light to be on or off, you can transmit binary bits.
The rate at which lights can flicker is so fast, that the human eye can’t perceive it!
However LiFi technology is an idea that gained popularity I think about four or five years ago. It might be a bit before it becomes a new breakthrough technology!
You cannot have an invalid entry in the foreign key column; at the same time, you cannot delete a vendor row as long as a product row references that vendor. this is known as:____.
Answers
You cannot have an invalid entry in the foreign key column; at the same time, you cannot delete a vendor row as long as a product row references that vendor. this is known as: referential integrity.
What is the referential integrity?
This is the term that is used to refer to the dependency on a primary key. This is the type of dependency that occurs based on the fact that the foreign key is much more dependent on the primary key.
This terminology is known to be associated with the relationship that is in existent within the given tables. Each of the tables that are of interest have a primary key. These appear based on the given relationships with the other keys in the table.
Read more on referential integrity here: https://brainly.com/question/17128955
#SPJ1
hy does payments constitute such a large fraction of the FinTech industry? (b) Many FinTech firms have succeeded by providing financial services with superior user interfaces than the software provided by incumbents. Why has this strategy worked so well? (c) What factors would you consider when determining whether an area of FinTech is likely to tend towards uncompetitive market structures, such as monopoly or oligopoly?
Answers
(a) lengthy and complex processes for making payments (b) legacy systems and complex interfaces (c) regulatory requirements and substantial initial investment, can limit competition
(a) Payments constitute a significant portion of the FinTech industry due to several factors. First, traditional banking systems often involve lengthy and complex processes for making payments, leading to inefficiencies and higher costs. FinTech firms leverage technology and innovative solutions to streamline payment processes, providing faster, more secure, and convenient payment options to individuals and businesses. Additionally, the rise of e-commerce and digital transactions has increased the demand for digital payment solutions, creating a fertile ground for FinTech companies to cater to this growing market. The ability to offer competitive pricing, improved accessibility, and enhanced user experience has further fueled the growth of FinTech payment solutions.
(b) FinTech firms have succeeded by providing financial services with superior user interfaces compared to incumbents for several reasons. Firstly, traditional financial institutions often have legacy systems and complex interfaces that can be challenging for users to navigate. FinTech companies capitalize on this opportunity by designing user-friendly interfaces that are intuitive, visually appealing, and provide a seamless user experience. By prioritizing simplicity, convenience, and accessibility, FinTech firms attract and retain customers who value efficiency and ease of use. Moreover, FinTech companies leverage technological advancements such as mobile applications and digital platforms, allowing users to access financial services anytime, anywhere, further enhancing the user experience.
(c) Several factors contribute to the likelihood of an area of FinTech tending towards uncompetitive market structures such as monopoly or oligopoly. Firstly, high barriers to entry, including regulatory requirements and substantial initial investment, can limit competition, allowing a few dominant players to establish market control. Additionally, network effects play a significant role, where the value of a FinTech service increases as more users adopt it, creating a competitive advantage for early entrants and making it challenging for new players to gain traction. Moreover, data access and control can also contribute to market concentration, as companies with vast amounts of user data can leverage it to improve their services and create barriers for potential competitors. Lastly, the presence of strong brand recognition and customer loyalty towards established FinTech firms can further solidify their market position, making it difficult for new entrants to gain market share.
To learn more about technology click here: brainly.com/question/9171028
#SPJ11
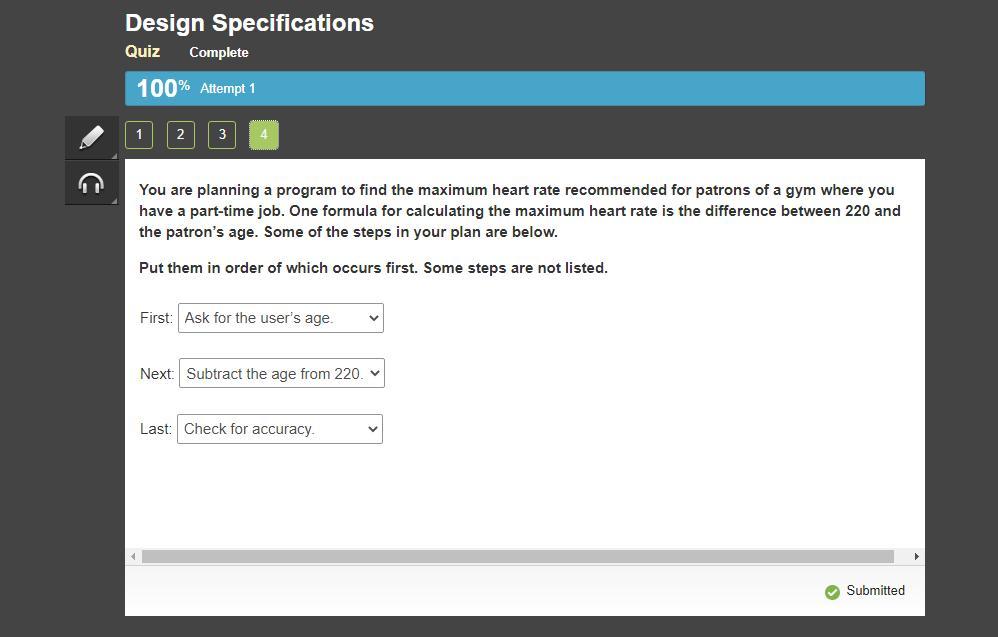
You are planning a program to find the maximum heart rate recommended for patrons of a gym where you have a part-time job. One formula for calculating the maximum heart rate is the difference between 220 and the patron’s age. Some of the steps in your plan are below.
Put them in order of which occurs first. Some steps are not listed.
Answers
Answer:
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Explanation:
The programs will be as follows
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Answer:
got 100 on the quiz
Explanation:
Defin major domains of AI??
koii h
Answers
Answer:
\(\sf\fbox\red{Answer:-}\)
The different domains of AI are Formal tasks, Mundane Tasks, and Expert Tasks.
\(\small\fbox{\blue{\underline{mαrk \; mє \; вrαínlíєѕt \; plєαѕє ♥}}}\)
marc is an investigator who discovers a piece of visible data. what did marc likely then see? group of answer choices any data stored in sectors or clusters a file dragged to the windows recycle bin a file being swapped in visible ram a string of sms text messages
Answers
Based on the given options, if Marc is an investigator who discovers a piece of visible data, he likely saw a file being swapped in visible RAM.
How can this process be explained?This refers to the process where data from the computer's memory is temporarily stored on the hard drive.
The other options, such as data stored in sectors or clusters, a file dragged to the Windows recycle bin, and a string of SMS text messages, do not necessarily indicate visible data that Marc would come across in his investigation.
Thus, the correct answer is a file being swapped in visible ram
Read more about file managers here:
https://brainly.com/question/13189758
#SPJ4
Match each type of short- and long-term investment to its attribute. long-term bonds stocks US Treasury bonds mature after 12 months and may be issued by corporations or government entities arrowRight a type of loan to the US government that has minimal risk arrowRight can be held for years, typically for future growth potential arrowRight
Answers
Hope this Helps :)
Corporate or governmental bodies may issue bonds that have a 12-month maturity — enduring bonds, a low-risk loan to the US government is provided via US Treasury Bonds, can be held for years, usually for possible future growth — stocks.
What is a low-risk loan?No security is needed from the borrowers to obtain these loans. Additionally, the loan money may be utilized for any private purpose, including debt relief, house improvements, car purchases, trips, and weddings.
A loan that is considered to carry a larger risk of defaulting than other, more conventional loans is called a high-risk loan. One or more reasons may be to blame for the higher default risk when evaluating a loan request.
The loans that are most likely to be accepted for include payday loans, auto title loans, loans from pawn shops, and personal installment loans. These are all short-term emergency cash assistance options for those with bad credit.
Thus, Corporate or governmental bodies may issue bonds.
For more information about low-risk loan, click here:
https://brainly.com/question/16930597
#SPJ2
Jennifer has been hired as a temporary employee at a local college. She is given a username and password to access certain parts of the college's intranet.
What type of network is Jennifer using?
Answers
Answer:
Extranet!
Explanation:
According to the Dictionary, an Extranet is an intranet that can be partially accessed by authorized outside users, enabling businesses to exchange information over the internet securely! I also got it correct in a test i did :]
Hope this helps :]
1. Print welcome message, ask the user for their name and use it when printing the scoreboard and narrating the game.
Ask the user to pick rock, paper, scissors.
2. Ask the user how many points they want to play to ( first to score that many points wins, so if they pick 5, first to score 5 points, not "best of 5" than they lose.
3. Computer choice will be random.
4. Show both user and computer throws in a neat/creative way.
5. Check to see who has won the round and award points.
6. Print a "scoreboard" each round that shows each player score, and how many points they're playing too.
7. At the end of the game, print the final score and who won the game, and some goodbye/ thanks message.
Answers
import random
name = input("Welcome! What's your name? ")
computer_choices = (["rock", "paper", "scissors"])
rounds = int(input("How many points do you want to play to, {}? ".format(name)))
user_total = 0
comp_total = 0
while user_total < rounds and comp_total < rounds:
user_choice = input("rock, paper, or scissors? ")
computer = random.choice(computer_choices)
if user_choice == computer:
print("It's a draw! You both threw {}".format(user_choice))
elif user_choice == "rock" and computer == "scissors":
user_total += 1
print("You threw rock and the computer threw scissors! You won!")
print("{}: {} point(s) out of {} point(s)".format(name, user_total, rounds))
print("Computer: {} point(s) out of {} point(s)".format(comp_total, rounds))
elif user_choice == "paper" and computer == "rock":
user_total += 1
print("You threw paper and the computer threw rock! You won!")
print("{}: {} point(s) out of {} point(s)".format(name, user_total, rounds))
print("Computer: {} point(s) out of {} point(s)".format(comp_total, rounds))
elif user_choice == "scissors" and computer == "paper":
user_total += 1
print("You threw scissors and the computer threw paper! You won!")
print("{}: {} point(s) out of {}".format(name, user_total, rounds))
print("Computer: {} point(s) out of {} point(s)".format(comp_total, rounds))
else:
comp_total += 1
print("You threw {} and the computer threw {}! You lost!".format(user_choice, computer))
print("{}: {} point(s) out of {}".format(name, user_total, rounds))
print("Computer: {} point(s) out of {} point(s)".format(comp_total, rounds))
print("The final scores are:")
print("{}: {} points".format(name, user_total))
print("Computer: {} points".format(comp_total))
if user_total > comp_total:
print("You won! Thanks for playing!")
else:
print("The Computer won! Thanks for playing")
I've tried to come up with something similar to what you wanted. If you have anymore question, I'll do my best to answer them.
Wi-Fi is mainly used by both home and public networks to access the Internet. True True False
Answers
Answer:
True
Explanation:
I belive it's true becuase for example if you dont pay you eletrical bill your eltice goes out and so does your wifi and when your wifi goes out you can't use the internet
How to design remote access policy using the appropriate access controls for systems,applications, and data access
Answers
Answer:
All remote access users connect to the network and maintain all security standards on the device including
Valid and virus protection
Malware protection
Maintain the OS
Explanation:
The remote access policy applies to employees and other affiliates who owned devices to remotely access the Network CCC. The remote policy access connection is used to perform the work activities on the behalf of CCC. Remote access system, application and can be accessed with the internal CCC network. Example of application are as follow:
Internal Academic System
Internal websites
Documents files on internal file
Local colleges resources
Servers
Remote access will be managed by System Data Center and use security measures based on requirements.
Remote access is provided as an extension of the normal work environment.
Review the CCC information technology for protecting information via the remote method.
The employee will use remote procedures. Employees disclose the passwords and if the business is conducted from home.
All remote access includes a "time-out" system. In accordance with CCC and will time out the specified period of inactivity.
The access users accept the access and connection to networks and monitored to record dates, time. Identify accounts and have been compromised by external parties.
The remote access user may be listed in the remote access application.
You have imported a library with the birthMonth() function. Based on the API, how many strings are inputed to calculate the birth month?
// calculate birth month based on the day of the month, day of the week, and the birth year
// dayMonth {number} - a day of a month from 1 to 31
// dayWeek {string} - the name of the day of the week
// year {number} - the birth year
// return {string} - the month you were born
BirthdayLibrary.birthMonth(dayMonth, dayWeek, year);
A. 1
B. 4
C. 0
D. 3
Answers
The function in question requires three arguments: dayMonth, dayWeek, and year. The number of strings entered to compute the birth month is three. Therefore, the correct option is D. 3.
To determine the birth month, the birthMonth() function receives the day of the month, day of the week, and birth year. It will then output the month in which the individual was born. Since there are three inputs, the correct answer is D. 3.
The API specifies the function's syntax and what is expected as inputs and outputs. When dealing with functions from other libraries, it is essential to read and understand their syntax and API documentation to use them correctly.
To know more about API visit:
https://brainly.com/question/29442781
#SPJ11
which one of the following is an input to the mrp system? a) shop-floor schedules b) financial reports c) master production schedule d) purchasing orders
Answers
An MRP (Materials Requirement Planning) system is a software-based system that is used to plan and manage the production processes of a manufacturing company.
To achieve this goal, the MRP system relies on a set of inputs that include data on sales forecasts, inventory levels, production schedules, and lead times. Based on these inputs, the MRP system generates a master production schedule (MPS) that outlines the production requirements for each product and the timing of the production runs.
Out of the options given, the input that is used to generate the MPS is the master production schedule (C). The MPS provides the MRP system with information on the production requirements for each product, including the quantity to be produced, the timing of the production runs, and any special requirements for the production process.
To know more about software visit:-
https://brainly.com/question/985406
#SPJ11
Carlos had 194 seeds and 11 flower pots he put the same number of seeds in each flower pot which is the best estimate for the number of seeds in each flower pot
Answers
Answer: in solution.
Explanation:
It is basically 194 divided by 11 since we are evenly grouping 194 seeds into 11 pots. This gives 17.636363…
This means that the best estimate is around that number.
How many things can a computer compare at one time?
Answers
Answer: billion of items at one time
Explanation: The computer is very capable of comparing items bulk at one time
A data analyst reviews a database of wisconsin car sales to find the last car models sold in milwaukee in 2019. how can they sort and filter the data to return the last five cars sold at the top of their list? select all that apply.
Answers
The analyst can exclude Milwaukee sales in 2019 and filter them by date in descending order.
What duties can metadata be used for by data analysts?Big Data can be meaningfully interpreted by analysts using metadata. The ability to identify, discover, and associate data across an enterprise ultimately increases the value of an organization's data resources. Many types of Big Data are unusable or impossible to manage without metadata.
What can data analysts achieve thanks to data transformation?Changes to the format, values, or structure of data are referred to as data transformations. To put it plainly, data analysts use data transformation techniques to transform raw data into a form that is much simpler to interpret and analyze.
To know more about enterprise visit:-
brainly.com/question/18551533
#SPJ4
All pointers are the same size and that size is dependent on the architecture of the processor. true. Why does the datatype of the pointer matter?
Answers
False. The size of pointers is not always the same and can vary depending on the architecture and programming language. However, the size of a pointer is typically dependent on the architecture of the processor.
The datatype of a pointer is important because it determines the type of data that the pointer can point to and the operations that can be performed on it. The datatype provides information about the size and interpretation of the data stored at the memory location pointed to by the pointer. It allows the compiler to perform proper type checking and ensure that operations performed on the pointer and the data it points to are valid and consistent.
For example, if a pointer is declared as an integer pointer (int*), it can point to memory locations that store integer values. Attempting to dereference the pointer and access data of a different datatype may lead to unexpected behavior or errors. Therefore, the datatype of a pointer is essential for proper memory access and type safety in programming.
To know more about pointer, click here: brainly.com/question/30460618
#SPJ11
What is the purpose of a Post Mortem Review?
To check the code for spelling
To prove the algorithm is correct
To understand how the code can be improved
To check the code for formatting
Answers
Answer:
A post-mortem meeting is held at the end of a project. The goal is to look at the project from start to finish to determine what went right and what can be improved. By the end of the meeting, you should have identified best practices and opportunities for improvement going forward.
Explanation: NONE
Answer:
A post-mortem meeting is held at the end of a project.
Explanation:
what pillar allows you to build a specialized version of a general class, but violates encapsulation principles
Answers
The pillar which allows you to build a specialized version of a general class but violates encapsulation principle is inheritance. In inheritance pillar you can create a general class or specifically a parent class and acquire another object method and properties.
Inheritance in Object Oriented Programming (OOP)Four pillars of Object Oriented Programming are abstraction, encapsulation, inheritance, and polymorphism. In inheritance an object can acquire another general object characteristics. It's like a child who inherited the parent's characteristics. What's the benefit of this pillar? Of course, reusability of the object, so you don't have to repeat a block code over and over again. This makes the code clean, simple and effective.
Learn more about programming language https://brainly.com/question/16397886#SPJ4
Electronic mail is a
A) Transmissions of letter, message and memos over a communication network
B) Distribution of all information
C) Both a and b
D) None of the above
Answers
Answer:
A) Transmission of letter, message and memos over a communication network
Explanation:
Communication can be defined as a process which typically involves the transfer of information from one person (sender) to another (recipient), through the use of semiotics, symbols and signs that are mutually understood by both parties. One of the most widely used communication channel or medium is e-mail (electronic mail).
An e-mail is an acronym for electronic mail and it is a software application or program designed to let users send texts and multimedia messages over the internet.
Hence, electronic mail is a transmission of letter, message and memos over a communication network. Some examples of the commonly used electronic mails platform are Yahoo, G-mail, etc.
T/F low-road transfer occurs most often with novel skills.
Answers
True, low-road transfer occurs most often with novel skills. This type of transfer involves the automatic application of well-practiced skills to new, similar situations without conscious thought, making it more common with novel skills.
True, low-road transfer occurs most often with novel skills. This means that when learning a completely new skill, our brains rely more on basic sensory and motor information and less on higher-level cognitive processes. This type of transfer occurs when the underlying neural pathways and structures are similar between the learned and new skill. However, it's important to note that the amount of content loaded in the original skill can also affect transfer. The more complex and varied the original skill, the more likely it is that high-road transfer (involving higher-level cognitive processes) will occur.Low road transfer occurs when the initial learning task and the transfer task are sufficiently similar in context and conditions so there is a high level of automaticity. High road transfer requires being able to identify mindful abstractions and connections from the initial learning task and the transfer task.
learn more about low-road here:
https://brainly.com/question/6792613
#SPJ11
While configuring a Windows 10 workstation for a new high priority project, you decide to mirror the operating system disk drive for redundancy. Which type of RAID (Redundant Array of Independent Disks) will you be configuring in Windows disk management
Answers
RAID1 type of RAID will be configuring in Windows disk management.
What do RAID 1 0 and 0 +1 mean?Despite the similarities between RAID 1+0 and RAID 0+1, the numbers' reversed order implies that the two RAID levels are layered in the opposite direction. In RAID 1+0, two drives are mirrored together before being combined into a striped set. Two stripe sets are created and then mirror using RAID 0+1.
RAID 1 has how many drives?With two drives, RAID 1 is most frequently used. Drive failure fault tolerance is provided by the replicated data on the disks. While write performance is reduced to that of a single drive, read performance is boosted. Without data loss, a single drive failure is possible.
To know more about RAID visit
brainly.com/question/14669307
#SPJ4
Professionals in the information technology career cluster have basic to advanced knowledge of computers, proficiency in using productivity software, and .
Answers
Answer:
The answer is "Internet skills ".
Explanation:
Internet skills are needed to process and analyze which others generate or download. Online communication abilities should be used to construct, recognize, and exchange info on the Web.
Creating these capabilities would enable you to feel more positive while using new technology and complete things so quickly that's why the above choice is correct.
What type of software permits a user to record video of what is occurring on the computer along with typed and cursor actions in order to create a lesson
Answers
The type of software which permits a user to record video of what is occurring on the computer along with typed and cursor actions in order to create a lesson is called screencast.
What is screencast?The screencast is the software which used to record the video of the screen of a computer. These types of software are build for the following purpose.
Uses to record, what a one sees on his computer.Such type of software are used to create the lesson as the facility of audio narration is provided in it.This software is helpful for the student who prefer self study.Many education organizations create learning with different screencast software.Thus, the type of software which permits a user to record video of what is occurring on the computer along with typed and cursor actions in order to create a lesson is called screencast.
Learn more about the screencast here;
https://brainly.com/question/15878080
#SPJ1
platforms that enable users to create a profile, specify which users they can connect with, and connect with other users are known as
Answers
Platforms that enable users to create a profile, specify which users they can connect with, and connect with other users are known as
social networking sites.
What is a social networking site?A social networking site is sometimes referred to as social network and it can be defined as a collection of Internet software applications and websites (platforms) which are designed and developed in order to avail end users with similar interests, an ability to connect, add, share, and discuss different information, as well as enhance remote connection, collaboration and debates (discussions) between community members over the Internet.
Additionally, some examples of a social networking site include the following:
Twi-tterFace-bookTi-kT-okInst-agr-amHangoutYou-tubeIn this context, we can reasonably infer and logically deduce that social networking sites can help connect users such as employees to other employees with similar professional interests.
Read more on social networks here: brainly.com/question/28072110
#SPJ1
Complete Question:
Platforms that enable users to create a profile, specify which users they can connect with, and connect with other users are known as
____________ _____________ sites.
anyone have good websites to cure boredom
Answers
Answer:
cool math if its not blocked
Explanation:
areas in which there has been significant technological advancement (electricity, transportation, communication, etc.)?
Answers
Answer:
transportation,communication,health care and agriculture
Explanation:
transportation through the provision of vehicles
comminication through the use of mobile
phones and laptops
health care through the use of machines and incubators
agriculture through the use of tractors and fertilizers
A problem with virtual networks is that data transmitting through them cannot be encrypted and therefore is not secure.
a. True
b. False
Answers
The given statement is False, "virtual networks don't have the drawback of making data transmission across them insecure because it is unable to encrypt it."
What is Virtual Networking?
Multiple PCs, virtual machines (VMs), virtual servers, or other devices can communicate with one another over various office and data center locations thanks to virtual networking. Virtual networking expands these capabilities by using software administration to connect computers and servers over the Internet, as opposed to physical networking, which connects computers using cabling and other hardware. It makes use of virtualized variations of conventional network tools like switches and network adapters to provide easier network configuration changes and more effective routing.
With the help of virtual networking, devices can operate in numerous locations with the same capabilities as a regular physical network. This enables data centers to spread across various physical locations and gives network administrators new, more effective options, such as the ability to quickly modify the network as needs change without having to replace or purchase additional hardware, greater flexibility in provisioning the network to specific needs and applications, and the capability to move workloads across the network infrastructure without compromising service, security, and availability.
To learn more about virtual network visit:
https://brainly.com/question/29492966
#SPJ4