Describe how the hash value produced by E3 compares to the values produced by FTK imager for the tow Outlook files and the value produced by Encase imager
Answers
Hash values are generally supposed to be distinctive and consistent, so if two different imaging tools construct an identical hash value for a file, it is likely that the file is an exact or identical copy that has not been changed.
What do you mean by Hash value?A hash value may be defined as a numeric value of a fixed length that uniquely identifies data. This value represents large amounts of data as much smaller numeric values, so they are typically used with digital signatures.
It is not feasible and practicable to deduce if the hash values are constructed by EnCase Imager and FTK Imager for the INFO2 file, Dc1.txt, and Outlook files that are exactly the same or different as the comparison depending on numerous factors.
The factors may include the algorithm used for hashing, the configuration settings of the imaging tools, and the integrity of the source data. In the case of E3, it is not clear what is meant by "E3 for the INFO2 file" or "E3 for Dc1.txt" without additional context.
Therefore, hash values are generally supposed to be distinctive and consistent, so if two different imaging tools construct an identical hash value for a file.
To learn more about Hash value, refer to the link:
https://brainly.com/question/29215636
#SPJ1
Related Questions
You need to replace every occurrence of "barn" with "shed." Which is the fastest method?
a) Use Replace to find and replace each occurrence.
b) Scroll through the document to locate each word, delete "barn," and type "shed."
c) Use Find to locate each occurrence, delete "barn," and type "shed."
d) Delete the entire text and retype the document.
Answers
The fastest method to replace every occurrence of "barn" with "shed" in a text document is to a)use the Find and Replace function.
The steps are mentioned below:
1. Open the text document in which you want to make the replacements.
2. Press "Ctrl+F" (Windows) or "Cmd+F" (Mac) on your keyboard to open the Find function.
3. In the Find box, type "barn" as the word you want to search for in the document.
4. Look for a button or option called "Replace" or "Find and Replace." Click on it to open the Replace function.
5. In the Replace box, type "shed" as the word you want to replace "barn" with.
6. Depending on your text editor, there may be an option to replace one occurrence at a time or replace all occurrences. To save time, choose the "Replace All" option.
By following these steps, you'll quickly replace every instance of "barn" with "shed" in your document. This method is much faster and more efficient than deleting the entire text and retyping it, ensuring you maintain accuracy and save time.
For more questions on document
https://brainly.com/question/1504260
#SPJ8
LAB: Step counter
A pedometer treats walking 1 step as walking 2.5 feet. Define a function named feet_to_steps that takes a float as a parameter, representing the number of feet walked, and returns an integer that represents the number of steps walked. Then, write a main program that reads the number of feet walked as an input, calls function feet_to_steps() with the input as an argument, and outputs the number of steps.
Use floating-point arithmetic to perform the conversion.
Ex: If the input is:
150.5
the output is:
60
The program must define and call the following function:
def feet_to_steps (user_feet)
Answers
Statistics are often calculated with varying amounts of input data. Write a program that takes any number of non-negative integers as input, and outpu
Answers
Answer:
Explanation:
The following program is written in Java and is a function that asks the user for an input and keeps doing so until a negative value is entered, in which case it calculates the average and max values and prints it to the screen.
public static void average () {
int num;
int sum = 0;
Scanner in = new Scanner(System.in);
System.out.println("Enter Number");
num = in.nextInt();
int count = 0;
int max = 0;
while(num >= 0)
{
sum+=num;
System.out.println("Enter Number");
num = in.nextInt();
count++;
if(num>=max){
max = num;
}
}
System.out.println(sum/count);
System.out.println(max);
}
Answer:hi
Explanation:
Name two ways to store data
Answers
Answer:
Hard drives and solid-state drives
Explanation:
What additional uses of technology can u see in the workplace
Answers
Answer:
Here are some additional uses of technology in the workplace:
Virtual reality (VR) and augmented reality (AR) can be used for training, simulation, and collaboration. For example, VR can be used to train employees on how to operate machinery or to simulate a customer service interaction. AR can be used to provide employees with real-time information or to collaborate with colleagues on a project.Artificial intelligence (AI) can be used for a variety of tasks, such as customer service, data analysis, and fraud detection. For example, AI can be used to answer customer questions, identify trends in data, or detect fraudulent activity.Machine learning can be used to improve the accuracy of predictions and decisions. For example, machine learning can be used to predict customer churn, optimize marketing campaigns, or improve product recommendations.Blockchain can be used to create secure and transparent records of transactions. For example, blockchain can be used to track the provenance of goods, to manage supply chains, or to record financial transactions.The Internet of Things (IoT) can be used to connect devices and collect data. For example, IoT can be used to monitor equipment, track assets, or collect data about customer behavior.These are just a few of the many ways that technology can be used in the workplace. As technology continues to evolve, we can expect to see even more innovative and creative uses of technology in the workplace.
A pitch can help convey important information in pre-production for it to receive the green light into production. True or false
Answers
Alyson would like to see a list of all of the applications installed on her computer. What is the easiest way for her to do this in the Microsoft Windows OS
Answers
Complete Question:
Alyson would like to see a list of all of the applications installed
on her computer. What is the easiest way for her to do this in the Microsoft Windows OS?
Group of answer choices.
A. Left-click "All Programs" at the bottom of the Start Menu.
B. Left-click on the desktop.
C. Enter "All programs" in the search bar for Windows Explorer.
D. It is not possible to see such a list.
Answer:
A. Left-click "All Programs" at the bottom of the Start Menu
Explanation:
A software can be defined as a computer program which comprises of sets of sequential instructions and data used for the performance of specific tasks on a computer system.
In order to see a list of all installed software applications or programs, Alyson should left-click "All Programs" at the bottom of the Start Menu.
In the older versions of Windows Operating System (OS) such as Windows 7, Vista, and XP manufactured by Microsoft corporation, there is a list of the most frequently used software applications or programs by an end user. This list of software programs are titled "All Programs" and it is located at the left-side within the Start Menu folder or at the bottom left corner of the Start Menu button.
Additionally, in recent Windows Operating System (OS) such as Windows 10 and 8, the "All Programs" is now All Apps.
What does a variable code block do?
Question 1 options:
stores a single piece of information
stores many pieces of information
repeats a process a set number of times
completes a set algorithm when a condition is met
Answers
A variable code block is used to store many pieces of information.The correct answer is option B.
It allows you to group related lines of code together and assign a variable name to them. This makes it easier to organize and access the information when needed. Additionally, by using variables, you can change the stored information dynamically throughout the code block, providing flexibility and adaptability in your program.
A variable code block is not a standard programming term, and there is no widely recognized concept or definition associated with it. However, based on the phrase you provided, it seems you may be referring to a data structure or container that can hold multiple values or pieces of information.
In programming, there are various data structures that can fulfill this purpose, such as arrays, lists, dictionaries, or objects, depending on the programming language being used. These data structures allow you to store and access multiple values or pieces of information within a single entity.
For more such questions block,Click on
https://brainly.com/question/9238983
#SPJ8
Define a function ScaleGrade that takes two parameters: • points: an integer, passed by value, for the student's score. • grade: a char, passed by reference, for the student's letter grade. ScaleGrade() changes grade to C if the points are greater than or equal to 67 and less than 80, and grade is not C. Otherwise, grade is not changed. The function returns true if grade has changed, and returns false otherwise. Ex: If the input is 67 D, then the output is: Grade is C after curving. 2 using namespace std; 3 4 int main() { 5 int studentTotal; 6 char studentGrade; 7 bool isChanged; 8 9 cin >> student Total; 10 cin >> studentGrade; 11 12 isChanged = ScaleGrade (studentTotal, studentGrade); 13 14 if (isChanged) { 15 cout << "Grade is " << studentGrade << " after curving." endl; 16 } 17 else { 18 cout << "Grade " << studentGrade << " is not changed." << endl; 19 } 20 1 2 3
Answers
bool ScaleGrade(int points, char& grade) {
if (points >= 67 && points < 80 && grade != 'C') {
grade = 'C';
return true;
}
return false;
}
The function takes an integer points and a character grade by reference, which means that any changes made to grade inside the function will be reflected in the calling code. The function returns a boolean value indicating whether the grade was changed or not.
The function checks if points are between 67 (inclusive) and 80 (exclusive), and if grade is not already 'C'. If both conditions are true, then the function sets grade to 'C' and returns true. Otherwise, it returns false.
Here is an example usage of the function in the provided main function:
int main() {
int studentTotal;
char studentGrade;
bool isChanged;
cin >> studentTotal;
cin >> studentGrade;
isChanged = ScaleGrade(studentTotal, studentGrade);
if (isChanged) {
cout << "Grade is " << studentGrade << " after curving." << endl;
}
else {
cout << "Grade " << studentGrade << " is not changed." << endl;
}
return 0;
}
The main function reads the input values for studentTotal and studentGrade, calls the ScaleGrade function, and prints a message depending on whether the grade was changed or not.
Which function calls would provide the most helpful test of this function? Remember: With tests, you are attempting to figure out all the possible ways the function could be broken.
function findMin(num1, num2){
if(num1 < num2){
return num1;
} else {
return num2;
}
}
A. findMin(-1, 0)
findMin(2,4)
findMin(5,10)
B. findMin(5,3)
findMin(7,2)
findMin(5,1)
C. findMin(1,1)
findMin(-2,2)
findMin(0,3)
D. findMin(-1,1)
findMin(1,-1)
findMin(1,1)
Answers
Answer:
D
Explanation:
Based on the information given, the correct option will be:
D. findMin(-1,1)findMin(1,-1)
findMin(1,1)
It should be noted that based on the information given, the correct option is D because it contains a duplicate set of numbers.
In this case, "1,1", would be vital in breaking the algorithm and require a bug fix from the developer. This then makes it the most helpful.
In conclusion, the correct option is D.
Learn more coding on:
https://brainly.com/question/22654163
____allow(s) visually impaired users to access magnified content on the screen in relation to other parts of the screen.
Head pointers
Screen magnifiers
Tracking devices
Zoom features
Answers
Answer: screen magnifiers
Explanation: got it right on edgen
Create two parallel arrays that represent a standard deck of 52 playing cards. One array is numeric and holds the values 1 through 13 (representing Ace, 2 through 10, Jack, Queen, and King). The other array is a string array that holds suits (Clubs, Diamonds, Hearts, and Spades).
Create the arrays so that all 52 cards are represented. Then, create a War card game that randomly selects two cards (one for the
player and one for the computer) and declares a winner or a tie based on the numeric value of the two cards. The game should last for 26 rounds and use a full deck with no repeated cards. For this game, assume that the lowest card is the Ace.
Display the values of the player’s and computer’s cards, compare their values, and determine the winner. When all the cards in the deck are exhausted, display a count of the number of times the player wins, the number of times the computer
wins, and the number of ties.
hints:
1) Start by creating an array of all 52 playing cards.
2) Select a random number for the deck position of the player’s first card and assign the card at that array position to the player.
3) Move every higher-positioned card in the deck “down” one to fill in the gap. In other words, if the player’s first random number is 49, select the card at position 49 (both the numeric value and the string), move the card that was in position 50 to position 49, and move the card that was in position 51 to position 50. Only 51 cards remain in the deck after the player’s first card is dealt, so the available-card array is smaller by one. In the same way, randomly select a card for the computer and “remove” the card from the deck.
Answers
Using the knowledge in computational language in python it is possible to write a code that Create the arrays so that all 52 cards are represented.
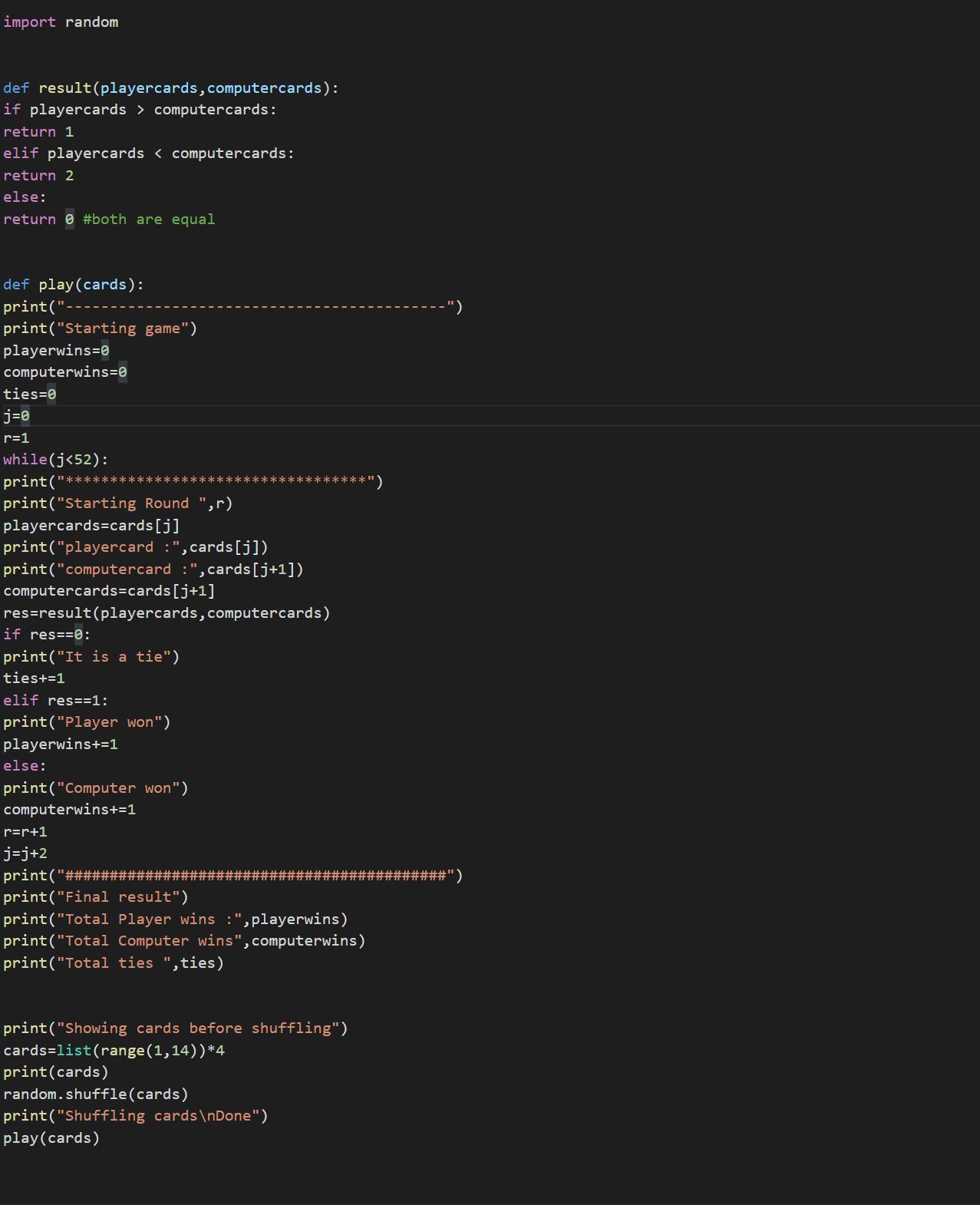
Writting the code:import random
def result(playercards,computercards):
if playercards > computercards:
return 1
elif playercards < computercards:
return 2
else:
return 0 #both are equal
def play(cards):
print("-------------------------------------------")
print("Starting game")
playerwins=0
computerwins=0
ties=0
j=0
r=1
while(j<52):
print("**********************************")
print("Starting Round ",r)
playercards=cards[j]
print("playercard :",cards[j])
print("computercard :",cards[j+1])
computercards=cards[j+1]
res=result(playercards,computercards)
if res==0:
print("It is a tie")
ties+=1
elif res==1:
print("Player won")
playerwins+=1
else:
print("Computer won")
computerwins+=1
r=r+1
j=j+2
print("###########################################")
print("Final result")
print("Total Player wins :",playerwins)
print("Total Computer wins",computerwins)
print("Total ties ",ties)
print("Showing cards before shuffling")
cards=list(range(1,14))*4
print(cards)
random.shuffle(cards)
print("Shuffling cards\nDone")
play(cards)
See more about python at brainly.com/question/12975450
#SPJ1
Ranjan have received an email saying that he won a free gift project to climb the gift voucher Ranjana give some personal details suggest Bank account number Bank name exact graph which type of security threat is indicated in the mail? should he answer the mail?
Answers
Research statistics related to your use of the Internet. Compare your usage with the general statistics.
Explain the insight and knowledge gained from digitally processed data by developing graphic (table, diagram, chart) to communicate your information.
Add informational notes to your graphic so that they describe the computations shown in your visualization with accurate and precise language or notations, as well as explain the results of your research within its correct context.
The statistics and research you analyzed are not accomplished in isolation. The Internet allows for information and data to be shared and analyzed by individuals at different locations.
Write an essay to explain the research behind the graphic you develop. In that essay, explain how individuals collaborated when processing information to gain insight and knowledge.
Answers
By providing it with a visual context via maps or graphs, data visualization helps us understand what the information means.
What is a map?The term map is having been described as they have a scale in It's as we call the longitude and latitude as well as we see there are different types of things are being different things are also in it as we see there are different things are being there in it as we see the oceans are there the roads and in it.
In the US, 84% of adults between the ages of 18 and 29, 81% between the ages of 30-49, 73% between the ages of 60 and 64, and 45% between the ages of 65 and above use social media regularly. On average, users use social media for two hours and 25 minutes each day.
Therefore, In a visual context maps or graphs, and data visualization helps us understand what the information means.
Learn more about the map here:
https://brainly.com/question/1565784
#SPJ1
The most reliable way to store important files without having to worry about backups or media failure is ____________.
A) cloud storage
B) on a USB flash drive
C) on a hard disk drive
D) on an optical disc
Answers
The ideal approach to save data for a longer time is cloud storage. Data security and storage reliability are two advantages of cloud storage that can't be matched. In addition, end-to-end encryption ensures the safety of all transmitted data.
Write a program to read a list of nonnegative integers and to display the largest integer, the smallest integer, and the average of all the integers. The user indicates the end of the input by entering a negative sentinel value that is not used in finding the largest, smallest, and average values. The average should be a value of type double so that it is computed with a fractional part. Input Notes: The input is simply a sequence of positive integers, separated by white space and terminated by -1.
Answers
Answer:
The program in Python is as follows:
mynum = []
num = int(input("Enter a number: "))
total = 0
while num >= 0:
mynum.append(num)
total+=num
num = int(input("Enter a number: "))
print("Smallest: ",min(mynum))
print("Largest: ",max(mynum))
print("Average: ",total/len(mynum))
Explanation:
This creates an empty list
mynum = []
This prompts the user for input
num = int(input("Enter a number: "))
This initializes total to 0
total = 0
The following is repeated until a negative number is inputted
while num >= 0:
This appends the inputted number into the list
mynum.append(num)
This calculates the sum of all the numbers inputted
total+=num
This prompts the user for another input
num = int(input("Enter a number: "))
This calculates and prints the smallest
print("Smallest: ",min(mynum))
This calculates and prints the largest
print("Largest: ",max(mynum))
This calculates and prints the average
print("Average: ",total/len(mynum))
2. Write the pseudocode to print all multiples of 5 between 10 and 25 (including both
10 and 25)
Answers
Answer:
Read code below
Explanation:
n = 10
while n is <= 25{
print(n)
n +=5
}
This while loop will print all multiples of 5 between 10 and 25 by starting with 10 as n, printing n, then incrementing n by 5 until n is greater than 25.
Assume a 2^20 byte memory:
a) What are the lowest and highest addresses if memory is byte-addressable?
b) What are the lowest and highest addresses if memory is word-addressable, assuming a 16-bit word?
c) What are the lowest and highest addresses if memory is word-addressable, assuming a 32-bit word?
Answers
a) Lowest address: 0, Highest address: (2^20) - 1. b) Lowest address: 0, Highest address: ((2^20) / 2) - 1. c) Lowest address: 0, Highest address: ((2^20) / 4) - 1.
a) If memory is byte-addressable, the lowest address would be 0 and the highest address would be (2^20) - 1.
This is because each byte in the memory requires a unique address, and since there are 2^20 bytes in total, the highest address would be one less than the total number of bytes.
b) If memory is word-addressable with a 16-bit word, each word would consist of 2 bytes.
Therefore, the lowest address would be 0 (representing the first word), and the highest address would be ((2^20) / 2) - 1.
This is because the total number of words is equal to the total number of bytes divided by 2.
Subtracting 1 gives us the highest address, as the addresses are zero-based.
c) If memory is word-addressable with a 32-bit word, each word would consist of 4 bytes.
In this case, the lowest address would still be 0 (representing the first word), and the highest address would be ((2^20) / 4) - 1.
Similar to the previous case, the total number of words is equal to the total number of bytes divided by 4.
Subtracting 1 gives us the highest address.
For more questions on address
https://brainly.com/question/30273425
#SPJ8
TCP is more dependable protocol than UDP because TCP is
Answers
Explanation:
because TCP creates a secure communication line to ensure the reliable transmission of all data.
Why were low quality video so often use when Internet connection we’re poorer than they are today
Answers
Answer:
The answer is C. "High-quality videos took too long to transfer" in Fundamentals of Digital Media.
A device receives a Transmission Control Protocol (TCP) packet. The device understands where the actual data payload begins. Which portion of the TCP header provides this information?
Answers
Answer:
The data offset field (4 bits) tells you how many 32-bits words there are in the header.
Eunice Lee likes technology and video games, so she is thinking of pursuing a career as a video game designer. Research the requirements of a video game designer. What kinds of interests, skills, and courses do you need? What is a typical career path for someone in the video game field
Answers
In order to be a video game designer, one must have:
Creativity.A love of video games.Storytelling talent.Broad understanding of game trends.Strong analytical abilities.Outstanding programming abilities.Capability to collaborate as part of a team.How can a typical career path for someone in the video game field be described?A popular job path is to begin as a game artist before progressing to lead artist and finally creative director. This is an excellent profession for anybody wishing to develop their creative muscles, and no two projects are ever the same.
A bachelor's degree in art and design, multimedia design, or a similar discipline is required for the majority of video game designers. Some colleges provide a degree in video game design. Software engineering, 2D and 3D animation, computer languages, and computer design are common courses.
Learn more about Video Game Designer:
https://brainly.com/question/14788186
#SPJ1
Write a program in RISC-V RARS to convert a string to an integer. Implement functions like atoi, strtol, and sprintf if needed. Assume all integers are greater than 0, so there are no negative or plus signs added.
Example: "25" is converted to the integer 25
Answers
Answer:
Here's an example RISC-V RARS program that converts a string to an integer:# load the string into a register
la x10, string
# initialize variables
li x11, 0 # result
li x12, 10 # base
li x13, '0' # offset for converting from ASCII to integer
# loop over each character in the string
loop:
lbu x14, 0(x10) # load the next character
addi x10, x10, 1 # move to the next character
beq x14, zero, done # if we've reached the end of the string, exit the loop
# convert the character from ASCII to integer and add it to the result
sub x14, x14, x13 # convert from ASCII to integer
mul x11, x11, x12 # multiply the result by the base
add x11, x11, x14 # add the converted character
j loop
done:
# x11 now contains the integer value of the string
# do something with it here
In this program, we first load the string into register x10. We then initialize three other registers: x11 will hold the result, x12 is the base (in this case, 10), and x13 is the offset we'll use to convert from ASCII to integer (since the character '0' has an ASCII value of 48).
We then start a loop that will iterate over each character in the string. We load the next character using the lbu instruction, and then add 1 to x10 to move to the next character. If we've reached the end of the string (indicated by a null terminator), we exit the loop.
For each character in the string, we first convert it from ASCII to integer by subtracting x13 (the offset for '0'). We then multiply the result by the base and add the converted character. This is the same process used in atoi and strtol.
Once we've processed all the characters in the string, we exit the loop and the integer value is stored in x11. We can then do something with the integer value, such as store it in memory or use it in a computation.
Explanation:
Which of the following statements is true of a pie chart?
a) It uses vertical bars sized relative to the values in the data series.
b) It uses horizontal bars sized relative to the values in the data series.
c) It uses horizontal bars sized relative to the values in the data series.
d) It connects data values with lines.
Answers
Answer:
d
Explanation:
Fill in the blank: To keep your content calendar agile, it shouldn’t extend more than ___________.
two weeks
one month
three months
six month
Answers
To keep your content calendar agile, it shouldn’t extend more than three months.
Thus, A written schedule for when and where content will be published is known as a content calendar.
Maintaining a well-organized content marketing strategy is crucial since it protects you from last-minute crisis scenarios and enables you to consistently generate new material and calender agile.
As a result, after the additional three months, it was unable to maintain your content calendar's agility.
Thus, To keep your content calendar agile, it shouldn’t extend more than three months.
Learn more about Calendar, refer to the link:
https://brainly.com/question/4657906
#SPJ1
The Bradshaw family has $200,000 of total assets and $140,000 of liabilities. What is their net worth?
Answers
Answer:
$340,000 is there net worth
Explanation:
$200,000+ $140,000 = $340,000
Question 3 3.1 Describe the TWO main elements of a CPU 3.2 Describe the fetch/execute cycle 3.3 Convert the binary number 00000011 to a decimal
Answers
Answer:
Here are the answers to the questions:
3.1 The two main elements of a CPU are:
The Control Unit (CU): The CU controls and coordinates the operations of the CPU. It is responsible for interpreting instructions and sequencing them for execution.
The Arithmetic Logic Unit (ALU): The ALU executes arithmetic and logical operations like addition, subtraction, AND, OR, etc. It contains registers that hold operands and results.
3.2 The fetch/execute cycle refers to the cycle of events where the CPU fetches instructions from memory, decodes them, and then executes them. The steps in the cycle are:
Fetch: The next instruction is fetched from memory.
Decode: The instruction is decoded to determine what it is asking the CPU to do.
Execute: The CPU executes the instruction. This could involve accessing data, performing calculations, storing results, etc.
Go back to Fetch: The cycle continues as the next instruction is fetched.
3.3 The binary number 00000011 is equal to the decimal number 3.
Binary: 00000011
Decimal: 1 + 2 = 3
So the conversion of the binary number 00000011 to decimal is 3.
Explanation:
Which of the following actions is NON-DESTRUCTIVE? CHOOSE TWO.
Everything in the Layer > Adjustments menu
The Clone Stamp tool
Converting to Grayscale
Changing the Opacity of a layer
Everything in the Adjustments panel
Answers
The following actions are non-destructive:
Everything in the Layer > Adjustments menu.
These adjustments can be made to a single layer without affecting the underlying layers. This means that you can edit the adjustments or remove them entirely without altering the original image data.
Changing the Opacity of a layer
When you change the opacity of a layer, it simply reduces the visibility of that layer but the original image data is still retained.
The Clone Stamp tool, which is used to copy pixels from one area of an image to another, can be destructive because it overwrites the original pixels.
Converting to Grayscale also discards the color information, which is considered a destructive action.
Everything in the Adjustments panel is not a valid option because it includes both destructive and non-destructive adjustments.
New trends, tools, and languages emerge in the field of web technology every day. Discuss the advantages of these trends, tools, and languages for a web designer or developer.
Answers
For a web designer or developer, the advantages of tools and languages are that they make it easier for them to deal with a variety of web technologies.
What is web technology?Online development tools are renowned for helping programmers work with a variety of web technologies, including HTML, CSS, JavaScript, and other types that are employed by the web browser.
HTML is considered to be the most fundamental coding language, and developers can style their code to meet specific requirements.
As a result, the benefits of tools and languages for web designers or developers are that they enable them to deal with a variety of web technologies.
To learn more about web technology, refer to the link:
https://brainly.com/question/28285530
#SPJ1
I really need help the correct answers ASAP!!! with CSC 104 Network Fundamentals
The Questions:
17. What is a Variable Length Subnet Mask (VLSM), and how is it created?
18. What are some of the different reasons to use VLANs?
Answers
Answer:
17. A Variable Length Subnet Mask (VLSM) is a technique used to allocate IP addresses to subnets of different sizes. It allows for more efficient use of IP address space by creating subnets with different sizes, rather than using a fixed subnet mask. VLSM is created by dividing the network into smaller subnets with different subnet masks, depending on the number of hosts required in each subnet.
18. There are several reasons to use VLANs, including:
Security: VLANs can be used to isolate traffic and prevent unauthorized access to sensitive data.
Performance: VLANs can be used to segment traffic and reduce network congestion, improving performance
Management: VLANs can simplify network management by grouping devices with similar functions or requirements
Flexibility: VLANs can be used to easily move devices between physical locations without changing their IP addresses
Explanation: