describe the difference between rights and permissions on a windows os.
Answers
Rights and permissions are two different concepts in the Windows operating system. Rights refer to the abilities and privileges granted to a user or group, while permissions refer to the access levels granted to a specific object, such as a file or folder.
In Windows, there are several built-in rights that can be assigned to users or groups, such as the right to log on locally or the right to shut down the system. These rights are often used to control access to system resources and ensure that only authorized users have the ability to perform certain tasks.
Permissions, on the other hand, are used to control access to specific files and folders. For example, a user may have the right to read a file, but not the permission to modify or delete it. Permissions can be assigned to individual users, groups, or even the "Everyone" group, which includes all users on the system.
In summary, rights control what a user or group can do on the system, while permissions control what they can access and modify. Both are important for ensuring the security and integrity of the Windows operating system and its resources.
To know more about operating system visit :
https://brainly.com/question/6689423
#SPJ11
Related Questions
imagine you plan to send 5 petabytes data from new york to san francisco. you have two choices: (1) transfer data using your 200 mbps dedicated link; (2) use ups over-night delivery. which option will deliver the data quicker?
Answers
Imagine you plan to send 5 petabytes of data from New York to San Francisco. You have two choices:
Transfer data using your 200 Mbps dedicated link; Use UPS overnight delivery.Data Transfer speed:It is a measurement of the number of bits that can be transferred from one location to another in a given time. It's calculated in bits per second, kilobits per second, megabits per second, or gigabits per second, depending on the amount of data involved.200 megabits per second (Mbps) = 0.02 gigabits per second (Gbps)The data transfer rate will be expressed in Gbps if the data transfer speed is more significant than Mbps.UPS overnight delivery:UPS overnight delivery is an alternative to network data transfer in which data is stored on disks and transferred using air or ground delivery services.
Learn more about Transfer data: https://brainly.com/question/30131275
#SPJ11
What are computer skills?
Answers
Answer:
Explanation:
like programming or hacking , or game design, maybe telecommunication controls ( think cell phone )
what was the first web browser to use public key certificates?
Answers
The first web browser to use public key certificates was Netscape Navigator.
Netscape Navigator, developed by Netscape Communications Corporation, was the pioneering web browser that introduced the use of public key certificates for secure communication over the internet. The browser implemented the Secure Sockets Layer (SSL) protocol, which utilized public key cryptography to establish secure connections between clients and servers. Public key certificates, also known as SSL certificates or X.509 certificates, played a vital role in authenticating the identity of websites and encrypting data transmission.
You can learn more about web browser at
https://brainly.com/question/22650550
#SPJ11
The "heart" of the digital camera is the __________ .
a
A/D converter
b
image/JPEG processor
c
MMS card
d
sensor
Answers
Answer:
D. Sensor without a the actual imaging sensor it wouldn't be able to capture anything.
Under unity of command, each worker is to report to only boss.
a. True
b. False
Answers
Option a is Correct. True. For each individual employee, there should be just one manager, claims Fayol. The concept of unity of command is broken if a worker receives commands from two supervisors at once.
According to the unity of command concept, a person should only report to one immediate supervisor. In order to implement this idea, project managers must create organizational structures. When orders and instructions are transmitted down, it avoids repetition and disagreement.
According to the principle of unity of command, a subordinate should only report to and take orders from one superior. By doing this, it is ensured that each employee has a single supervisor who they must answer to. It is clear who should be reported in this situation.
Learn more about unity command Visit: brainly.com/question/989567
#SPJ4
Type the correct answer in the box. Spell all words correctly.
Complete the sentence to highlight an area of application of procedural languages.
“what” is an open source operating system that programmers developed based on a procedural language.
Answers
It is to be noted that Linux is an open-source operating system that programmers developed based on a procedural language.
What are procedural languages?FORTRAN, COBOL, ALGOL, BASIC, C, and Pascal are examples of procedural languages. Non-Procedural Language: In non-procedural languages, the user specifies just "what to do" rather than "how to do." It's sometimes referred to as an applicative or functional language.
Linux was created in C, assembly languages, and other programming languages. Linux is an open-source operating system comprised of the kernel, the OS's core component, and the tools, programs, and services that come with it.
Learn more about Linux:
https://brainly.com/question/15122141
#SPJ1
What is an html skeleton? If you know what it is can you write it for me?
Answers
Answer:
HTML Skeleton. The basic HTML skeleton is the set of tags required of every HTML web page you build. The tags that make up the skeleton tell browsers what kind of file it is reading, and without the skeleton HTML files will not be rendered correctly in web browsers. There are four tags that need to be included in the skeleton.
Explanation:
What is the missing line?
import csv
_____
myReader = csv.reader(inFile)
for item in myReader:
print(item)
inFile = open("fruit.txt","r")
inFile = reader("fruit.txt","open")
inFile = reader("fruit.txt","r")
inFile = open("fruit.txt","read")
Answers
Based on the code written above, the missing line is option C: inFile = reader("fruit.txt","r")
What does line encoding mean?The code used to transmit data from a digital signal via a transmission line is called a line code. This coding method was chosen to prevent signal overlap and distortion like inter-symbol interference.
A group of instructions used to alter data such that a certain input yields a specific output is known as a program in computer coding.
Digital data is transformed into digital signals through the process of line coding. Using this method, we turn a series of bits into a digital signal. Digital data are encoded into a digital signal at the sender side, and they are reproduced at the receiver side by decoding the digital signal.
The full code is:
import CSV
inFile = open('pets.txt', 'r')
myReader =
reader(inFile)
for item in myReader
print(item)
exit()
Learn more about code from
https://brainly.com/question/23865485
#SPJ1
In 2008, PCWorld magazine named Copland to a list of the biggest project failures in IT history. Apple's Copland Operating System It's easy to forget these days just how desperate Apple Computer was during the 1990s. When Microsoft Windows 95 came out, it arrived with multitasking and dynamic memory allocation, neither of which was available in the existing Mac System 7. Copland was Apple's attempt to develop a new operating system in-house; actually begun in 1994, the new OS (Operating System) was intended to be released as System 8 in 1996. Copland's development could be the poster child for feature creep. As the project gathered momentum, a furious round of empire building began. (In business, empire-building is demonstrated when individuals or small groups attempt to gain control over key projects and initiatives to maximize job security and promotability) As the new OS came to dominate resource allocation within Apple, project managers began protecting their fiefdoms* by pushing for their products to be incorporated into System 8. New features began to be added more rapidly than they could be completed. Apple did manage to get one developers' release out in late 1996, but it was wildly unstable and did little to increase anyone's confidence in the company. Before another developer release could come out, Apple made the decision to cancel Copland and look outside for its new operating system; the outcome, of course, was the purchase of NeXT, which supplied the technology that became OS X. *Fiefdom: a territory or sphere of operation controlled by a particular person or group. Question #1: What went wrong for Apple's Copland Operating System Project? What would be the primary lesson learned for this project?
Answers
Apple's Copland Operating System project faced several challenges and ultimately failed. The primary factors that went wrong were feature creep, empire-building within the project, and the inability to deliver a stable and functional product. The primary lesson learned from this project is the importance of effective project management, including controlling feature creep, maintaining focus on core objectives, and ensuring timely delivery of stable releases.
The Copland Operating System project at Apple suffered from feature creep, which refers to the continuous addition of new features beyond the project's original scope. As the project progressed, various stakeholders pushed for their products to be incorporated into the system, leading to an increasing number of features being added at a rapid pace. This resulted in a loss of focus and the inability to complete features in a timely manner.
Furthermore, empire-building within the project contributed to its downfall. Project managers and individuals sought to gain control over key aspects of the project, creating silos and hindering collaboration. This fragmented the development process and hindered the overall progress of the project.
The primary lesson learned from the Copland project is the significance of effective project management. It is crucial to control feature creep, maintain a clear focus on core objectives, and adhere to realistic timelines. Additionally, fostering collaboration and minimizing internal power struggles is essential for successful project outcomes. These lessons highlight the importance of strategic planning, communication, and project governance to avoid costly failures and ensure the timely delivery of stable and functional products.
Learn more about Operating System here:
https://brainly.com/question/6689423
#SPJ11
What is a Boolean Expression?
A) Statements that only run when certain conditions are true
B) Something a program checks to see whether it is true before deciding to take an action
C) An expression that evaluates to true or false
Answers
In computer science, a Boolean expression is an expression used in programming languages that produces a Boolean value when evaluated. A Boolean value is either true or false.
( Lol. I’m in 7th grade doing college work, so this was fun to answer! )
What is burning in Computers and technology
Answers
So that is why people talk about "burning" songs or files to CDs. They could just say they are "writing" the data to a CD, and it would make sense, but people seem to think "burning" sounds cooler.
Answer:
Burn-in is a test in which a system or component is made to run for an extended period of time to detect problems. Burn-in may be conducted to ensure that a device or system functions properly before it leaves the manufacturing plant or may be part of a repair or maintenance routine.
Explanation:
hope this helps
Integer numData is read from input. Then, numData alphabetically sorted strings are read from input and each string is appended to a vector. In the FindMatch() function:
Assign rangeSize with the total number of vector elements from lowerIndex to upperIndex (both inclusive).
Assign midIndex with the result of dividing the sum of lowerIndex and upperIndex by 2.
Ex: If the input is:
3 how new pen then the output is:
Number of elements in the range: 3
Middle index: 1
Element at middle index: new
Here is the Current Script:
#include
#include
#include
using namespace std;
void FindMatch(vector allWords, int lowerIndex, int upperIndex) {
int midIndex;
int rangeSize;
cout << "Number of elements in the range: " << rangeSize << endl;
cout << "Middle index: " << midIndex << endl;
cout << "Element at middle index: " << allWords.at(midIndex) << endl;
}
int main() {
vector dataList;
int numData;
int i;
string item;
cin >> numData;
for (i = 0; i < numData; ++i) {
cin >> item;
dataList.push_back(item);
}
FindMatch(dataList, 0, dataList.size() - 1);
return 0;
}
Answers
The above script is one that contains errors. So, the updated script is given in the code attached.
What is the Integer numData?The FindMatch function needs the help of the allWords list to work properly. In the FindMatch function, the size of the range from lowerIndex to upperIndex is given to rangeSize.
MidIndex is when you add the lowerIndex and upperIndex together, then divide the total by 2. One can use the number in the middle of the allWords list to find a specific word in the list. I put in the instructions needed to use the necessary libraries.
Learn more about Integer numData from
https://brainly.com/question/32727684
#SPJ4

Which of these cannot be used to open a zip file?
O WinZip
O WordPad
File Viewer Plus
O Apple Archive Utility
Answers
Answer:
c
Explanation:
bc
Using a movie or documentary (fictional or real), explain what the production phase of the motion picture might look like. What events might take place? What might the different people on the production team do? Make sure to include information about all major team members as well as actors/actresses. Your response should be detailed and should integrate the information from the entire lesson.
Answers
Answer:
PRODUCER
This person is essentially the group leader and is responsible for managing the production from start to finish. The producer develops the project from the initial idea, makes sure the script is finalized, arranges the financing and manages the production team that makes the film
The director is primarily responsible for overseeing the shooting and assembly of a film. While the director might be compared to a novel's author as a film's primary visionary, he or she would not be able to make the film without the help of numerous other artists and technicians.
In fact, the notion of the director as an author is misleading because it assumes the director, like an author, does everything. A director works at the center of film production, but is inextricably linked with dozens of other people who get the job done together.
SCREENWRITER
While the dialogue in a film may seem natural to the viewer, a writer carefully crafts it; however, the screenwriter does far more than provide dialogue for the actors. He or she also shapes the sequence of events in a film to ensure that one scene transitions to the next so that the story will unfold logically and in an interesting way.
Like the producer, the screenwriter's role is generally overlooked by the movie-going public, yet is essential to the completion of any film. If there is no script, there is no movie.
PRODUCTION DESIGNER
Before one inch of film is shot, the production designer is the first artist to translate the script into visual form. He or she creates a series of storyboards that serve as the film's first draft.
A storyboard is a series of sketches on panels that shows the visual progression of the story from one scene to the next. Creating this sketch of the film on storyboards also ensures the visual continuity of the film from start to finish. Storyboards serve as the director's visual guide throughout the production and will be a template to follow during the editing process.
PRODUCTION DESIGNER
Before one inch of film is shot, the production designer is the first artist to translate the script into visual form. He or she creates a series of storyboards that serve as the film's first draft.
A storyboard is a series of sketches on panels that shows the visual progression of the story from one scene to the next. Creating this sketch of the film on storyboards also ensures the visual continuity of the film from start to finish. Storyboards serve as the director's visual guide throughout the production and will be a template to follow during the editing process.
Explanation:
9.3 code practice python
Write a program that creates a 4 x 5 list called numbers
. The elements in your list should all be random numbers between -100 and 100, inclusive. Then, print the list as a grid.
For instance, the 2 x 2 list [[1,2],[3,4]]
as a grid could be printed as:
1 2
3 4
Sample Output
-94 71 -18 -91 -78
-40 -89 42 -4 -99
-28 -79 52 -48 34
-30 -71 -23 88 59
Note: the numbers generated in your program will not match the sample output, as they will be randomly generated.
Answers
"The program first creates a list of size 4x5 and assigns randomly generated numbers to its indices. It then prints the list in a grid format on the screen. Best of luck."
import random
#Create list as 4x5 and assign random values between -100 and 100.
list = [[random.randint(-100, 100) for j in range(5)] for i in range(4)]
#Print as grid.
for i in range(len(list)):
for j in range(len(list[0])):
print(list[i][j], end=" ")
print()


UNIDAD CENTRAL DE PROCESO
Answers
Answer:
what is that give me the meaning first
Explanation:
Which type of backup ensures you capture a complete snapshot of everything that makes your computer run?.
Answers
Answer:
Answer is D / If not : A full image backup, or mirror backup
Explanation:
is an exact replica of everything on your computer's hard drive, from the operating system, boot information, apps, and hidden files to your preferences and settings. Imaging software not only captures individual files, but everything you need to get your system running again.
Thanks for asking this question. If my response helped, please mark as brainliest. Thank you!
a fraudulent financial deal has just taken place in the company where you are working as a network administrator. the data of the company will be collected in such a way that it can be presented in a court of law for the purpose of prosecution. some of the forensic data available for analysis may be damaged or destroyed if improperly handled. you have been assigned the duty to safeguard sensitive information, logged data, and other legal evidence until the first responder or incident response team can take over the collection of evidence. to prevent contamination of evidence, you have made sure that each device involved is isolated-that is, the device is disconnected from the network and secured to ensure that no one else has contact with it until the response team arrives. what is the next step that you will take in the event of such an illegal activity? group of answer choices
Answers
Document The Scene.
Creating a defensible audit trail is one of the highest priorities in the forensics process. An audit trail is a system of documentation that makes it possible for a third party to inspect evidence later and understand the flow of events.
What is fraudulent financial?Financial fraud happens when someone deprives you of your money, capital, or otherwise harms your financial health through deceptive, misleading, or other illegal practices. This can be done through a variety of methods such as identity theft or investment fraud. What Is Financial Statement Fraud? Financial statement fraud is the deliberate misrepresentation of a company's financial statements, whether through omission or exaggeration, to create a more positive impression of the company's financial position, performance and cash flow. Criminals are constantly creating new types of fraud. But some common standards include embezzlement, insurance fraud, ransomware, identity theft, financial statement fraud, bribery, mortgage fraud, tax evasion, and ponzi schemes.
To know more about fraudulent financial visit:
https://brainly.com/question/26963566
#SPJ4
Why do you need to learn about engineering and technology.
Answers
Answer:
Engineering is very closely linked to technology, and the rise of it, which is why it has played a huge part in technological advances including computers, hospital machines, the internet and more. Healthcare has also improved dramatically thanks to advancements in medical technology thanks to engineers.
Explanation:
You use the analogy that a four-dimensional array is like a shelf of books.
Which part of the analogy does 3 refer to in myData[1] [3] [2] [6]?
page
book
row in the table
shelf
Answers
Answer:
Page
Explanation:
Edge 2020
The page part of the analogy, 3 refer to in myData[1] [3] [2] [6]. The correct option is A.
What is array?An array is a collection of memory locations, or "boxes," each of which has the same name and can store a single piece of data. An array's data must all be of the same data type.
The metaphor suggests that a four-dimensional array is similar to a book shelf.
A dimension is used in addition to length, breadth, and depth to enable the use of geometrical language when discussing occurrences that depend on four parameters.
Consequently, it may be said that a four-dimensional array is comparable to a shelf of books. In my Data are page, 2 refers to the analogy's relevant section.
Thus, the correct option is A.
For more details regarding analogy, visit:
https://brainly.com/question/2403481
#SPJ5
11. Who is considered a knowledge worker? Will you have a career as a knowledge worker? Explain.
12. When would a business use mobile computing or web-based information systems in their operations? Discuss an example of a business function that could be implemented on each platform, and explain why that platform would be preferred over the other platform.
13. TPSs are usually used at the boundaries of the organization. What are boundaries in this context? Give three examples of boundaries.
Answers
A knowledge worker is an individual who works primarily with knowledge, particularly in a professional context.
11. A knowledge worker's job requires a high degree of expertise, education, and skills, as well as the ability to think critically and creatively. If you work in a field that involves research, analysis, or other knowledge-based activities, you are likely to be a knowledge worker. Many jobs require knowledge workers, including scientists, engineers, doctors, lawyers, and accountants. If you are interested in pursuing a career as a knowledge worker, you will need to develop your knowledge, skills, and expertise in your chosen field.
12. Businesses would use mobile computing or web-based information systems in their operations when they require to streamline their processes and improve their efficiency. An example of a business function that could be implemented on each platform is given below:
Mobile Computing: A business can use mobile computing to track employees' location and send notifications. This can be useful for delivery companies, food delivery, and transportation companies that require to keep track of their employees' movement and scheduling. In addition, mobile computing can be used to make sure that customer-facing businesses like restaurants and retail stores can take payments on the go.
Web-based Information Systems: Businesses that manage a large number of clients may benefit from using web-based information systems to store customer data and track orders. This can be useful for businesses that require to manage customer relationships like e-commerce stores or subscription services. In addition, web-based information systems can be used to make sure that customer-facing businesses like restaurants and retail stores can take payments on the go.
13. Boundaries in the context of TPS are the points at which the system interacts with the external environment. For example, when a transaction occurs, the boundary is where the data is entered into the system and then passed on to other systems or applications. The boundaries of an organization can be physical, such as the walls of a building or geographical boundaries. They can also be conceptual, such as the separation between different departments within a company. The three examples of boundaries are as follows: Physical Boundaries: The walls of a factory or office building are examples of physical boundaries. In addition, a shipping company might have to deal with geographical boundaries when transporting goods between countries or continents. Conceptual Boundaries: Different departments within a company might have different conceptual boundaries. For example, the sales department may have different priorities and objectives than the finance department. External Boundaries: These are the points at which the system interacts with the external environment. An example of an external boundary is when a transaction is initiated by a customer or a vendor.
To learn more about knowledge workers: https://brainly.com/question/15074746
#SPJ11
Please Help!
Assume that you have an array named items containing 100 integers, and an integer named numItems that represents the number of valid integers currently used in the array. All elements from items[numItems] to items[items.length-1] have values of 0.
The following code is designed to calculate and print the average of the valid array elements:
int sum=0, count;
for (count = 0; count < items. length; count++)
{
statement 1
}
statement 2
Which of the following substitutions for and will cause this code to correctly print the average of the valid array elements in items?
A. Statement 1:
sum += items[count];
Statement 2:
System.out.println((double)sum / count);
B. Statement 1:
sum += items[count];
Statement 2:
System.out.println((double)sum / items.length);
C. Statement 1:
sum += items[count];
Statement 2:
System.out.println((double)sum / numItems);
D. Statement 1:
sum += items[items.length-1];
Statement 2:
System.out.println(sum / 100);
E. Statement 1:
sum += items[items.length-1];
Statement 2:
System.out.println((double)sum / numItems);
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
This question is about calculating the sum and average of the elements in the given array.
The code is given below:
int sum=0, count;
for (count = 0; count < items. length; count++)
{
statement 1
}
statement 2
Then this question is asked that which of the following substitutions for and will cause this code to correctly print the average of the valid array elements in items?
So, The correct answer is A. Because the first statement counts the sum of all the given elements in the array. And, the second statement print the average (sum/count) and store result in double.
A. Statement 1:
sum += items[count];
Statement 2:
System.out.println((double)sum / count);
So that the correct and complete program is given below:
int sum=0, count;
for (count = 0; count < items. length; count++)
{
sum += items[count];
}
System.out.println((double)sum / count);
How does air gap networking seek to keep a system secure? by taking extra steps to ensure the DMZ server is fully patched to deal with the latest exploits by physically isolating it from all unsecured networks, such as the internet or a LAN by focusing on the security of the system through detection devices and incident reports
Answers
Air gap networking seeks to keep a system secure by physically isolating it from all unsecured networks, such as the internet or a LAN Thus, the correct option for this question is B.
What do you mean by the Air gap in networking?The air gap in network security may be defined as a type of measure that is utilized in order to ensure a computer network is physically isolated in order to prevent it from establishing an external connection, specifically to the Internet.
According to the context of this question, this process is used in order to ensure the security of the computer and computer network by physically isolating it from unsecured networks such as the internet or a LAN.
Therefore, the correct option for this question is B.
To learn more about Air gap networking, refer to the link:
https://brainly.com/question/14752856
#SPJ1
it produces uppercase letters but it does not affect numbers and symbols A. Tab B. Shift C. Caps lock
Answers
The function that produces uppercase letters and does not affect numbers and symbols is the Caps Lock function (C).
What is the Caps lock about?The Caps Lock function is known to be a type of function that allows you to type uppercase letters by pressing the Caps Lock key. It does not affect the input of numbers and symbols.
Therefore, based on the context of the above, one can say that the Tab key (A) is used to create spacing between text and to navigate between fields in forms. The Shift key (B) is used to produce uppercase letters and special characters, and is typically used in combination with other keys.
Learn more about Caps lock from
https://brainly.com/question/13843442
#SPJ1
Richard wants to share his handwritten class notes with Nick via email. In this scenario, which of the following can help Richard convert the notes into digital images so that he can share them via email? a. Bar coding device b. Digital printing software c. Document scanner d. Radio frequency identification tag
Answers
Answer: Document Scanner
Explanation: Cos then he can easily add the paper notes to his computer and email the client.
while t >= 1 for i 2:length(t) =
T_ppc (i) (T water T cork (i- = - 1)) (exp (cst_1*t)) + T cork (i-1);
T cork (i) (T_ppc (i) - T pet (i- = 1)) (exp (cst_2*t)) + T_pet (i-1);
T_pet (i) (T cork (i)
=
T_air) (exp (cst_3*t)) + T_air;
end
T final ppc = T_ppc (t);
disp (newline + "The temperature of the water at + num2str(t) + "seconds is:" + newline + T_final_ppc + " Kelvin" + newline + "or" + newline +num2str(T_final_ppc-273) + degrees Celsius" + newline newline);
ansl = input (prompt, 's');
switch ansl case 'Yes', 'yes'} Z = input (IntroText); continue case {'No', 'no'} break otherwise error ('Please type "Yes" or "No"')
end
end
Answers
The given code describes a temperature change model that predicts the final temperature of water based on various input parameters such as the temperatures of cork, pet, and air.
It appears that you are providing a code snippet written in MATLAB or a similar programming language. The code seems to involve a temperature calculation involving variables such as T_ppc, T_water, T_cork, T_pet, and T_air. The calculations involve exponential functions and iterative updates based on previous values.
The model uses a set of equations to calculate the temperature changes for each component.
The equations used in the model are as follows:
T_ppc(i) = (T_water – T_cork(i-1)) * (exp(cst_1 * t)) + T_cork(i-1)T_cork(i) = (T_ppc(i) – T_pet(i-1)) * (exp(cst_2 * t)) + T_pet(i-1)T_pet(i) = (T_cork(i) – T_air) * (exp(cst_3 * t)) + T_airThese equations are implemented within a for loop, where the input variables t, T_water, T_cork, T_pet, cst_1, cst_2, cst_3 are provided, and the output variable T_final_ppc represents the final temperature of the water after the temperature change.
Additionally, the code includes a prompt that allows the user to enter "Yes" or "No." Choosing "Yes" continues the execution of the code, while selecting "No" stops the code.
Overall, the code simulates and predicts the temperature changes of water based on the given inputs and equations, and offers the option to continue or terminate the execution based on user input.
Learn more about MATLAB: https://brainly.com/question/13715760
#SPJ11
Can someone help me plz
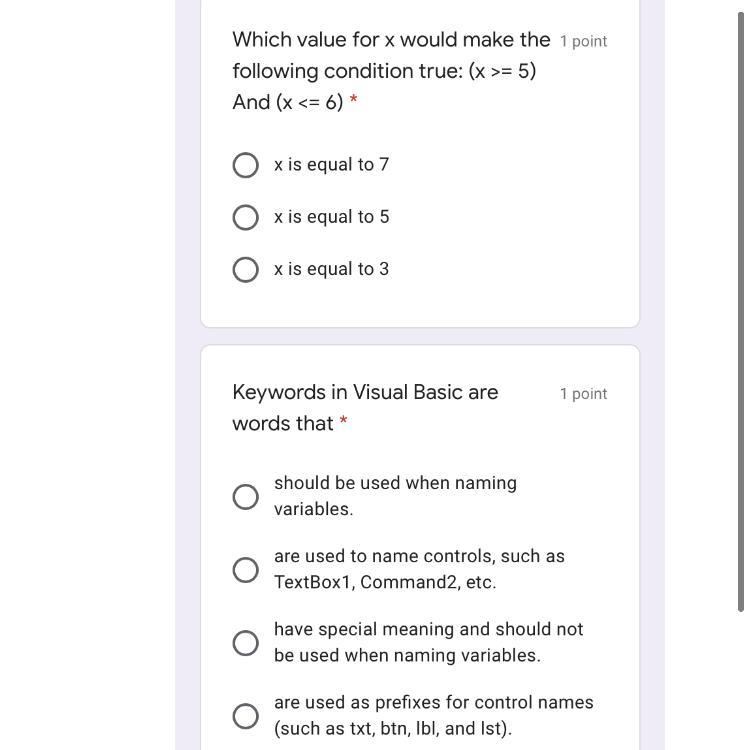
Answers
and
C = “ have special meaning and should not be used when naming variables “.
Write a JavaScript program in an HTML document to ask user to enter a class of math marks
(0 – 100) by using a while loop, then when the user enters a negative number, your program
should display the class average to one decimal place.
Answers
Here is a sample JavaScript program depicted in an HTML document that utilizes a while loop to ask the user to enter math marks and thereby compute the class average:
The ProgramThe calculateAverage() function can be triggered when the user presses "Calculate". It consists of a while loop, within which three variables - sum (total marks), count (number of marks entered) and mark (the current mark being analyzed) are set up.
The cycle continues until a negative number is inserted; it encompasses marks between 0 and 100 (inclusive). As soon as the user inserts an integer below zero, the cycle halts and the average is obtained by dividing the summation by the amount.
The class average is sent to one decimal place through the usage of the toFixed() procedure on the average variable. Lastly, the conclusive result is shown in the HTML record by setting the innerHTML of the segment "result" to a string that involves the class median.
Read more about JavaScript here:
https://brainly.com/question/16698901
#SPJ1

During Program Increment (PI) execution, the System Team is unclear about how to test some of the larger Features. What should a Release Train Engineer do?
a) Escalate the problem to senior management to get the required action
b) Allow the problem to reach a critical point knowing that a minor failure is a technique for learning
c) Direct Product Management to define the use cases for the Features
d) Encourage the System Team and Product Management to meet and collaborate on a solution
Answers
The System Team is unclear about how to test some of the larger Features. What should a Release Train Engineer do is: d) Encourage the System Team and Product Management to meet and collaborate on a solution.
During Program Increment (PI) execution, it is not uncommon for the System Team to face challenges when testing larger Features. In such a situation, a Release Train Engineer (RTE) should encourage the System Team and Product Management to meet and collaborate on a solution. This approach promotes teamwork and ensures that everyone involved is working towards a common goal of delivering high-quality Features.
The collaboration between the System Team and Product Management can help identify gaps in testing and define the use cases for the Features. This can be an iterative process that involves regular feedback and discussions to ensure that the testing strategy is effective and aligned with the business goals. So the answer is D.
Learn more about System Team: https://brainly.com/question/30456614
#SPJ11
which of the following commands is used to verify that a remote host can respond to a network connection?
Answers
The command used to verify that a remote host can respond to a network connection is called "ping". Ping is a widely used command in networking to test the connectivity between two devices on a network. When the ping command is executed, it sends an ICMP (Internet Control Message Protocol) packet to the target host and waits for a response.
If the remote host is reachable, it responds to the ping request with an ICMP echo-reply packet, indicating that it is available on the network. The ping command is a simple and effective way to verify the network connectivity between two hosts. It can also provide valuable information such as the round-trip time (RTT) and the number of packets lost during the transmission. The ping command can be executed from a command prompt on both Windows and Linux systems, making it a versatile tool for network troubleshooting.In conclusion, the ping command is an essential tool for network administrators to verify the connectivity between devices on a network. It is a simple and effective way to test the network connection and diagnose network issues. By using the ping command, administrators can quickly identify the cause of connectivity problems and take corrective actions to resolve them.
Learn more about network here
https://brainly.com/question/28342757
#SPJ11