How to open NAT type for multiple PC's?
Answers
Opening NAT type for multiple PCs requires you to create a static IP address and forwarding ports on your router. This will allow the router to allocate a specific IP address to each device that will always be the same.
Opening NAT type for multiple PC's- To open NAT type for multiple PCs, follow the steps below:
Step 1: Get the MAC addresses of all PCs. Ensure that you have the MAC addresses of all the devices that you want to connect to the network. The MAC address is the unique address that identifies each device on the network. To find the MAC address on a PC, open the command prompt and type "ipconfig/all"
Step 2: Reserve an IP address for each device. Once you have the MAC addresses, you can reserve an IP address for each device. This ensures that each device will always have the same IP address. You can do this by logging into your router and creating a static IP address.
Step 3: Port forwarding. Once you have created static IP addresses, you will need to forward the ports for each device. This involves opening the required ports for each device on your router. This can be done by accessing your router settings and forwarding the required ports. To do this, you will need to know which ports to forward for each device. You can find this information online, or by contacting the manufacturer of your devices.
To learn more about "open NAT", visit: https://brainly.com/question/31143418
#SPJ11
Related Questions
Assign avg_owls with the average owls per zoo. Print avg_owls as an integer. Sample output for inputs: 124 Average owls per zoo: 2 1 avg_owls - 0.0 1 test passed All test 3 num_owls_zooA int(input) 4 num_owls_zooB = int(input) 5 num_owls_zooC - int(input) 6 7 num_owls_zooA - 1 8 num_owls_zooB 2 9 num_owls_zooC = 4 10 num_zoos - 3 11 12 avg_owls -(num_owls_zooA num_owls_zooB+num_owls_200C)/num_zoos 13 14 print('Average owls per zoo:', int(avg_owls) Run ✓ Testing with inputs: 124 Your output Average owls per zoo: 2 X Testing with inputs: 3 44 Output differs. See highlights below. Your output Average owls per zoo: 2 Expected output Average owls per zoo: 3
Answers
To calculate the average, each zoo's number of owls must be added together and then divided by the total number of zoos. The output should be the average owls per zoo, as an integer.
The avg_owls variable is useda to store the average number of owls per zoo. This value is calculated by taking the total number of owls in each zoo and dividing that by the total number of zoos. The result is then rounded down to the nearest integer. Oncea the average is calculated, it is printed as an integer. It is important to check that the inputs are correct when calculating the average, as any incorrect inputs would result in an incorrect output. If the output does not match the expected output, the inputs should be checked and corrected as needed. Once the inputs are correct the average will be calculated correctly and the expected output will be printed.
Learn more about output here-
https://brainly.com/question/14227929
#SPJ4
What are the best editing apps?
Answers
Answer:
Snapseed, Lightroom, Adobe Photoshop, Prisma, Bazaart, Photofox, VSCO and PicsArt.
Explanation:
Snapseed, Lightroom, Adobe Photoshop, Prisma, Bazaart, Photofox, VSCO and PicsArt are the best editing apps. Some of the apps are present as free while some of them are not available without paying money for it. These are the top best editing apps so you can use it anyone of it. Snapseed is free on iOS and Android whereas Lightroom needs $5 per month for full access. Adobe Photoshop is also free on iOS and Android.
Answer:
After effects or alight motion on mobile are pretty good
Explanation:
Python String Functions: Create a new Python Program called StringPractice. Prompt the user to input their name, then complete the following:
Length
• Print: “The length of your name is: [insert length here]”
Equals
• Test to see if the user typed in your name. If so, print an appropriate message
Really appreciate the help.
Answers
#Swap this value by your name. Mine is Hamza :)
my_name = "Hamza"
#Get input from user.
inp = input("What's your name?: ")
#Print the length of his/her name.
print("The length of your name is",len(inp),"characters.")
#Check if the input matches with my name?
#Using lower() method due to the case insensitive. Much important!!
if(inp.lower()==my_name.lower()):
print("My name is",my_name,"too! Nice to meet you then.")
Question 1 1.67/2pts In the Internet Protocol, the IPv4 addresses are 32-bit long expressed in dotted decimal notation in 4 octets (each octet is 8 bits); example: 128.34.55.21. IPv6 addresses are 128-bit long expressed as 8 8-byte-pairs to make a 128 bit address; example: 2001:0db8:0000:0042:0000:8a2e:0370:ffff. Based on this information, mark the following address as IPV4, IPV6, or INVALID. 119.67.44.86 94.49.190.138 258.151.50.253 e0f8:af58:eee6:52b d938:2da7:b596:6d34:3970:6789:
Answers
The classification of the addresses is as follows:
1. 119.67.44.86 - IPV4
2. 94.49.190.138 - IPV4
3. 258.151.50.253 - INVALID
4. e0f8:af58:eee6:52b - INVALID
5. d938:2da7:b596:6d34:3970:6789 - INVALID
Based on the given information, we can determine the types of the following addresses:
1. 119.67.44.86: This address consists of four octets separated by dots, so it follows the IPv4 format.
Hence, it is an IPv4 address.
2. 94.49.190.138: Similar to the previous address, this address also has four octets separated by dots.
Therefore, it is an IPv4 address.
3. 258.151.50.253: In this address, the first octet "258" exceeds the valid range (0-255) for IPv4 addresses.
Therefore, this address is invalid.
4. e0f8:af58:eee6:52b: This address consists of five 8-byte pairs, separated by colons. Since IPv6 addresses should have eight 8-byte pairs, this address is incomplete and does not follow the correct IPv6 format. Hence, it is invalid.
5. d938:2da7:b596:6d34:3970:6789: This address has six 8-byte pairs separated by colons, which does not match the correct IPv6 format. Therefore, it is invalid.
Learn more about IP address here:
https://brainly.com/question/31171474
#SPJ4
Sebastian is the hr department's trainer. He is developing various materials to teach the fundamentals of using a virtual private network (vpn) to a variety of audiences, from the president and vice presidents of the corporation to newly hired mid-level managers and entry-level employees. After implementing his training program some weeks ago, he began getting calls from the it help desk stating that users are contacting them with troubleshooting issues for their vpn sessions. The help desk technicians do not know how to respond. What is the most likely problem?
Answers
First, attempt to block the firewall from communicating with the VPN, then restart.
Below is a list of the most likely issues.
The difficulty connecting to a virtual private network might be caused by a firewall issue.
Initially attempt to halt the firewall's contact with the VPN, then resume.
If the tunnel connection is established incorrectly, troubleshooting problems may also result. The server's VPN connection has to be verified, and any superfluous features should be turned off. It's also possible that the VPN's crash is what's causing the troubleshooting difficulty. You should try to remove any unused software from your computer. You need update the antivirus. Along with updating the server software, clients should also receive updates. Reinstate the VPN, if possible. Additionally, there is a possibility of incorrect port connection.
Learn more about VPN here:
https://brainly.com/question/29432190
#SPJ4
Give at lesat 3 examples of how is NLG (Natural Language Generation) beneficial and unbeneficial (pls support your points)
Answers
NLG (Natural Language Generation) is beneficial isuch as automating content creation, personalizing user experiences, and generating insights from data but have limitations including potential biases in generated content and difficulties in capturing nuanced human language.
How is NLG beneficial and unbeneficial?NLG offers numerous benefits including the ability to automate the generation of content across different domains, such as news articles, product descriptions, and weather reports. This helps save time and resources by eliminating the need for manual content creation.
NLG systems may have limitations. One concern is the potential for biased content generation as the models are trained on existing data that may contain biases. This can lead to the generation of discriminatory or misleading content.
Read more about Natural Language
brainly.com/question/14222695
#SPJ1
NLG is beneficial in generating content quickly and accurately, maintaining consistency, and providing a personalized user experience
NLG, or Natural Language Generation, is the method of generating natural language text using computer algorithms. It is a subfield of artificial intelligence that focuses on creating human-like texts, thereby making it easier for humans to interact with machines. Natural Language Generation is beneficial in many ways, but it also has its limitations. In this response, we will discuss the benefits and drawbacks of NLG in detail. Benefits of Natural Language Generation (NLG):
1. Efficient content creation: NLG algorithms can generate content faster than human writers, making it easier for businesses and publishers to create large amounts of content in less time. This is particularly beneficial for news and sports articles, where quick updates are required.
2. Consistent quality and tone: NLG can ensure that the content is written in a consistent tone and style, maintaining the brand's voice and values. In contrast, human writers can experience mood changes, which may influence the quality of their writing.
3. Personalization: NLG algorithms can create personalized messages and content, providing a better user experience for customers and clients. It can also be used for chatbots to provide human-like interactions with customers, improving customer satisfaction.
Unbeneficial of Natural Language Generation (NLG):1. Limited creativity: NLG algorithms can generate text based on the data it is fed. However, it lacks creativity and may fail to produce the same level of creativity as human writers. NLG cannot replace human writers' creativity, which is required in fields such as literature and poetry.
2. Dependence on data quality: NLG requires high-quality data to generate effective texts. Low-quality data may result in incorrect information and errors in the generated text.
3. Lack of empathy: NLG algorithms lack human empathy and understanding of social and emotional contexts. This may cause problems in situations that require a high level of emotional intelligence, such as counseling, medical diagnosis, and human resources. Therefore, NLG is beneficial in generating content quickly and accurately, maintaining consistency, and providing a personalized user experience. However, it has its limitations and cannot replace human creativity, empathy, and emotional intelligence.
For more questions on articles
https://brainly.com/question/25276233
#SPJ8
Worms and Trojans are typically harmless because the originator of such attacks are usually known to the recipient, and as such, are not intended to cause much harm.
(A) True
(B) False
Answers
Answer:
False
Explanation:
Viruses, worms and trojans are all malicious programs that can damage your computer. Also i got an A soo...
For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
For all hypertext links in the document, set the font-color to ivory and set the text-decoration to none.
(CSS)
Answers
Using the knowledge in computational language in html it is possible to write a code that For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
Writting the code:<!doctype html>
<html lang="en">
<head>
<!--
<meta charset="utf-8">
<title>Coding Challenge 2-2</title>
</head>
<body>
<header>
<h1>Sports Talk</h1>
</header>
<nav>
<h1>Top Ten Sports Websites</h1>
<ul>
</ul>
</nav>
<article>
<h1>Jenkins on Ice</h1>
<p>Retired NBA star Dennis Jenkins announced today that he has signed
a contract with Long Sleep to have his body frozen before death, to
be revived only when medical science has discovered a cure to the
aging process.</p>
always-entertaining Jenkins, 'I just want to return once they can give
me back my eternal youth.' [sic] Perhaps Jenkins is also hoping medical
science can cure his free-throw shooting - 47% and falling during his
last year in the league.</p>
<p>A reader tells us that Jenkins may not be aware that part of the
least-valuable asset.</p>
</article>
</body>
</html>
See more about html at brainly.com/question/15093505
#SPJ1


The party with 15. The party with the short position 7. An interest rate is 158 with semiannual compounding compoundin 14.46% (B) 15.008 6) 15.0\%\% D) 13.98% F) 12.67%
Answers
In this scenario, there is a party with a long position of 15 and another party with a short position of 7. The interest rate is 15.008% with semiannual compounding.
In this situation, one party holds a long position of 15, indicating they have entered into an agreement to buy a certain asset or financial instrument. On the other hand, there is another party with a short position of 7, which means they have agreed to sell the same asset or financial instrument.
The interest rate mentioned is 15.008%, and it is compounded semiannually. This means that the interest is calculated and added to the principal amount twice a year. The compounding period is important because it affects the total interest earned over time.
To calculate the final answer, more information is needed. The context of the question suggests that the answer should relate to the interest rate, so we can assume it asks for the interest rate earned on the positions. However, the options provided (B, 15.008; 6, 15.0%; D, 13.98%; F, 12.67%) do not clearly align with the information given. Therefore, without additional details, it is not possible to generate a specific answer from the options provided.
Learn more about position here:
https://brainly.com/question/31813302
#SPJ11
Darian is preparing for a presentation about the poor condition of the locker rooms at school. Match each of the key components of a presentation to a detail of Darian's presentation. audience to persuade the school board to improve locker-room condition purpose Darian's school board locker-room condition topic a electronic slideshow method can anyone
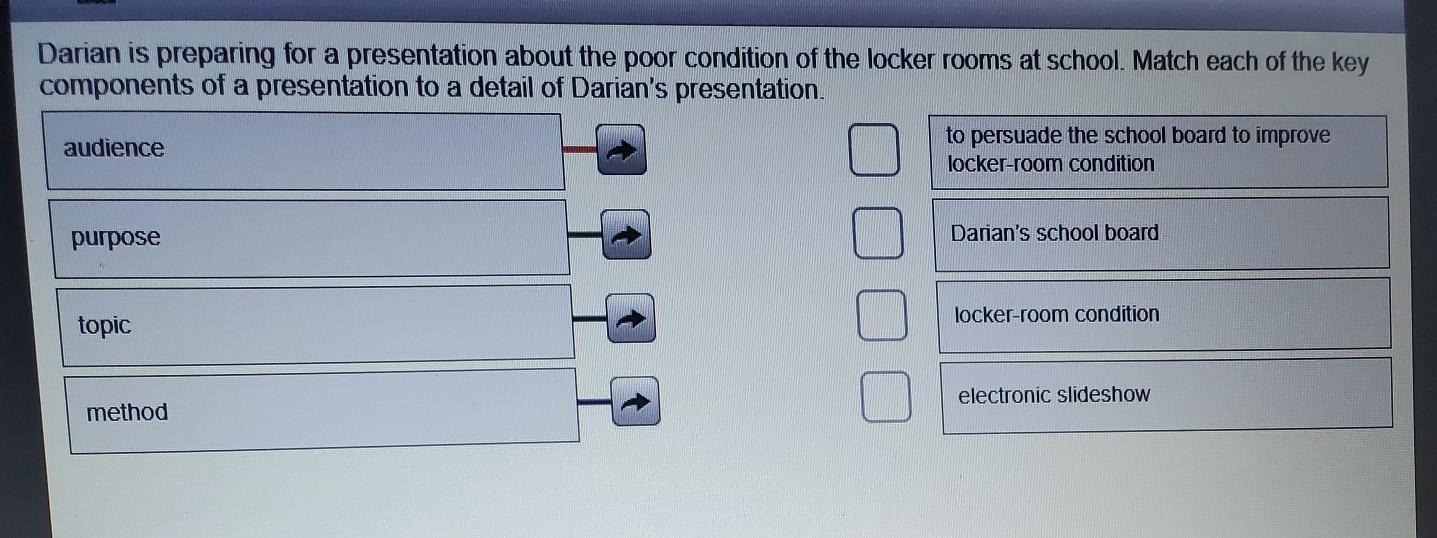
Answers
Answer:
Purpose - To paurswade the board to change the conditions of the locker room
Topic - Locker room condition
Method - Electronic Slideshow
Audience - School Board
1-5 Safety measures in the use of kitchen tools and equipment.
Answers
Answer:
Safety measures are as follows;
Explanation:
Hold the delicate instruments cautiously to use them.Require appropriate use of the equipment in the kitchen.Users should remove these defective instruments or discard of them.During and before use, check that perhaps the resources that will be used are indeed safe.In a cold and dry spot, all equipment must be kept.When someone presses SEND on a cellular phone, the phone attempts to set up a call by transmitting a "set-up" message to a nearby base station. The phone waits for a response and if none arrives with 0.5 second, it tried again. If it doesn't get a response after n=6 tries, the phone stops transmitting messages and generates a busy signal. (a) Draw a tree diagram that describes the call set up procedure. (b) If all transmissions are independent and the probability is "p" that a set-up message will get through, what is the PMF of " K ", the number of messages transmitted in a call attempt? (c) What is the probability that the phone will generate a busy signal ? (d) As manager of a cellular phone system, you want the probability of a busy signal to be less than 0.02. If p=0.9, what is the minimum value of n necessary to achieve this goal ? 4. When a conventional paging system transmits a message, the probability that the page will be received by the pager it is sent to, is p. To be confident that a message is received at least once, a system transmits the message n times. (a) Assuming all transmissions are independent, what is the PMF of K, the number of times the pager receives the same message ? (b) Assume p=0.8, what is the minimum value of n that produces a 0.95 probability of receiving the message at least once?
Answers
The call set-up procedure and message transmission in a cellular phone system can be analyzed using probability concepts and tree diagrams.
How can we analyze the call set-up procedure and message transmission using probability concepts and tree diagrams?To describe the call set-up procedure, we can create a tree diagram. The initial branch represents the first attempt, and subsequent branches represent subsequent attempts up to n=6 tries. Each branch has two outcomes: success (transmission received) or failure (no response). The tree diagram depicts the possible sequences of success and failure leading to either a call set-up or a busy signal.
Assuming independent transmissions with probability p, the PMF (Probability Mass Function) of K, the number of messages transmitted in a call attempt, follows a geometric distribution. The PMF of K is given by P(K=k) = (1-p)^(k-1) * p, where k ranges from 1 to n.
The probability that the phone generates a busy signal is the complement of the probability of successful call set-up. So, it can be calculated as P(busy signal) = (1 - p)^n.
To achieve a busy signal probability of less than 0.02 (or 0.02), we set the inequality (1 - p)^n ≤ 0.02. Substituting p=0.9, we can solve for the minimum value of n required to satisfy the inequality.
The PMF of K, the number of times the pager receives the same message, also follows a geometric distribution with independent transmissions. The PMF of K is given by P(K=k) = (1-p)^(k-1) * p, where k ranges from 1 to n.
Assuming p=0.8, we can determine the minimum value of n that produces a 0.95 probability of receiving the message at least once by solving the inequality (1 - p)^n ≤ 1 - 0.95.
Learn more about probability
brainly.com/question/31828911
#SPJ11
Which of the following is true about ethical issues in graphic design?
A. Ethical issues force designers to create unbiased designs.
B. Unethical behavior rarely occurs in the graphic design industry.
C. Closely imitating the work of another designer is considered unethical.
D. Understanding ethical issues reduce the amount of design work that is plagiarized.
Answers
Answer: The Answer Is B
Explanation:
I Did It On Edge
It should be B) Unethical behavior rarely occurs in the graphic design industry, i got it right on Edge
Also im sorry im a month late
which formula should be entered to calculate the total budget?

Answers
Answer:
SUM(A$1:A$3),
Explanation:
A formula is an expression telling the computer what mathematical operation to perform upon a specific value. When referring to computer software, formulas are most often used in spreadsheet programs, such as Microsoft Excel. Using formulas in spreadsheets can allow you to quickly make calculations and get totals of multiple cells, rows, or columns in a spreadsheet.
In the picture below is an example of a Microsoft Excel formula =SUM(A$1:A$3), which adds the total of cells A1, A2, and A3. In this formula, SUM is the function of the formula.
Formula in Microsoft Excel
Tip
Press the shortcut key Shift+F3 to open the Excel Formula or Insert Function window.
Note
A formula is not be seen unless the cell is selected.

3.
The process of displaying the information from the table is called
a. Query
Form
b. Report
. d Wizard
00
Answers
Explanation:
the process of displaying the information from the table is called query
hey friend your answer is here I hope it will be helpful you please mark as brainiest answer thank youWhen looking to send email to your contacts you need to collect what _______ to help build the trust you need to create lasting relationships with your contacts.
Answers
When looking to send email to your contacts, you need to collect their email addresses to help build the trust you need to create lasting relationships with them.
In order to do this, you can ask them directly for their email address or you can use a sign-up form on your website or social media profiles. It is important to always ask for permission before adding someone to your email list and to respect their preferences for how often they would like to receive emails from you. Additionally, it is important to include an easy way for people to unsubscribe from your email list if they no longer wish to receive emails from you.
Learn more about collecting email address here https://brainly.com/question/30092844
#SPJ4
Jason is working on a Microsoft Excel worksheet and he wants to create a Print Preview shortcut. His teacher asks him to access the Customization option to create the new shortcut. Which two tabs should Jason select to place the Print Preview shortcut on the worksheet toolbar?
A.
New Tab (Custom) and New Group (Custom)
B.
New File Tab (Custom) and New Tab (Custom)
C.
New Custom Group and New Command
D.
New Custom Tab and New Command

Answers
Answer:
it's definitely B I asked my brother
what are some examples of what can be changed through options available in the front dialog box
Answers
The font dialog box controls all the attributes for font family. This dialog box is present in the Context menu of all the applications. The font family characters like italicizing and bolding of fonts can be controlled by this. Thus, correct option is A.
What is Font dialog box?A Context menu appears by right-clicking on selected characters. Font dialog box is present in this context menu. The Font dialog box is available on the Windows applications. This lets the user choose attributes for a font, such as font style, point size, effects (underline, Bolding, italicizing, strikeout, and text color), and a script (or character set). Ctrl + D key is a shortcut key for font tab.
The dialog box displays all the information related to text in the file, and asks a user for input. This font dialog box is used for editing the font in the file. Therefore, A is the correct option.
Learn more about dialog box here:
https://brainly.com/question/13845767
#SPJ1
Your question is incomplete, probably the complete question/missing part is:
what are some examples of what can be changed through options available in the front dialog box?
A. font family italicizing bolding
B. pasting drop shadow
C. cutting character spacing
D. special symbols
Jill is interested in a career as a paramedic. She is trained to use medical equipment, she remains calm under pressure, and she has good bedside manner. Which career pathway would best fit Jill's interests and skills?
Answers
Answer:
Emergency and Fire management services
Explanation:
Paramedics are trained to respond to emergency situations faced by the public. These could include, fire incidents, accidents, or other emergency situations. Paramedics are trained to be calm under pressure, to use medical equipment, as well as to have good bedside manners as their jobs might require taking care of victims of various incidents at the spot of crisis, or in ambulances before they arrive the hospitals.
So, Jill is likely interested in a career in Emergency and Fire Management Services because she would require these skills to succeed in this field.
Answer:
Emergency and Fire management services
Explanation:
Which file attribute identifies the file as having been modified since the last backup?.
Answers
Archive file identifies the file as having been modified since the last backup.
Archive file understanding
The meaning of the word Archive in the Online Computer Dictionary is used to make a copy of a backup file with the aim of protecting the original copy from damage.
How to Archive Files Into 1 File
If you want to send a large number of files, you can make the file into 1 archive file format with .zip, .tar, or .rar format first. This method is also quite easy and fast.
• First, make sure your computer has programs such as winzip, winrar. This program is needed to archive files.
• Second, you can select the file you want to archive, then right-click on the file. The example below shows 2 files to be archived
• The third step, you can directly select Add to “folder name.rar” to directly create archive files automatically. If you want to do some settings, it can be done by selecting the Add to archive option.
The Add to archive option allows you to choose the save format of the file, divide or create the archive into several parts (part 1, part 2, etc.), to create a password. With the password, before the file can be extracted, it is necessary to enter the password first.
In addition to files, you can also archive folders directly along with the contents of the files in it. Keep in mind, how fast the process of archiving this file will depend on how many or large files to be archived.
Learn more about archive files at https://brainly.com/question/15355917.
#SPJ4
Need answer ASAP I’ll mark brainliest if correct
How can you create a class without any methods, yet call a method from that class?
The class can___ methods from another class
Answers
hope that helps if you have any questions let me know and if you could mark this as brainliest i would really appreciate it!
Which of the following statements about variables or values are true? Check all that apply.
Variables store values.
Variables store permanent data.
Values are the result of functions.
Variables in code are useful only on a single occasion.
Answers
Answer:
A and C
Explanation:
Variables store values as well as values are the result of functions. The correct options are A and D.
What are variables?A variable in programming is a value that can change based on external factors or data that has been supplied to the program.
A program typically consists of data that it uses while running and instructions that tell the machine what to execute.
A variable is a place where values are kept. In order to use a variable, we must first declare it in order to inform the program that it exists and then assign it in order to inform the computer of the value we are placing in the variable.
Values are both stored in variables and the output of functions. Variables can have a wide range of values, which is why they are called variables.
Thus, A and D are the correct options.
For more details regarding variables, visit:
https://brainly.com/question/17344045
#SPJ2
virtual conections with science and technology. Explain , what are being revealed and what are being concealed
Answers
Some people believe that there is a spiritual connection between science and technology. They believe that science is a way of understanding the natural world, and that technology is a way of using that knowledge to improve the human condition. Others believe that science and technology are two separate disciplines, and that there is no spiritual connection between them.
What is technology?
Technology is the use of knowledge in a specific, repeatable manner to achieve useful aims. The outcome of such an effort may also be referred to as technology. Technology is widely used in daily life, as well as in the fields of science, industry, communication, and transportation. Society has changed as a result of numerous technological advances. The earliest known technology is indeed the stone tool, which was employed in the prehistoric past. This was followed by the use of fire, which helped fuel the Ice Age development of language and the expansion of the human brain. The Bronze Age wheel's development paved the way for longer journeys and the development of more sophisticated devices.
To learn more about technology
https://brainly.com/question/25110079
#SPJ13
a_______helps us to see the relationship between different parts of data
Answers
Answer:
Data label........
..
Pictures in the _____ gallery give the appearance of a physical object, such as water drops or sand, that can give your presentation a unique look.
Answers
Answer:peanut
Explanation:
Write a Python program that performs as a Tuffy Titan Contact List which contains a list of contacts that can be modified or deleted
Answers
The program allows the user to add, modify, and delete contacts from the Tuffy Titan Contact List. To create a Tuffy Titan Contact List using Python, you can use a dictionary to store the contact information.
You can then create functions to add, modify, and delete contacts from the dictionary. Here is an example program:
```python
# Create an empty dictionary to store the contacts
contacts = {}
# Function to add a contact
def add_contact(name, phone_number, email):
contacts[name] = {'phone_number': phone_number, 'email': email}
# Function to modify a contact
def modify_contact(name, phone_number, email):
if name in contacts:
contacts[name]['phone_number'] = phone_number
contacts[name]['email'] = email
else:
print('Contact not found.')
# Function to delete a contact
def delete_contact(name):
if name in contacts:
del contacts[name]
else:
print('Contact not found.')
# Function to display all contacts
def display_contacts():
for name, info in contacts.items():
print('Name:', name)
print('Phone Number:', info['phone_number'])
print('Email:', info['email'])
print()
# Main program
while True:
print('Tuffy Titan Contact List')
print('1. Add Contact')
print('2. Modify Contact')
print('3. Delete Contact')
print('4. Display Contacts')
print('5. Exit')
choice = input('Enter your choice: ')
if choice == '1':
name = input('Enter name: ')
phone_number = input('Enter phone number: ')
email = input('Enter email: ')
add_contact(name, phone_number, email)
elif choice == '2':
name = input('Enter name: ')
phone_number = input('Enter phone number: ')
email = input('Enter email: ')
modify_contact(name, phone_number, email)
elif choice == '3':
name = input('Enter name: ')
delete_contact(name)
elif choice == '4':
display_contacts()
elif choice == '5':
break
else:
print('Invalid choice.')
```
This program allows the user to add, modify, and delete contacts from the Tuffy Titan Contact List. The contacts are stored in a dictionary, with the name as the key and a dictionary containing the phone number and email as the value. The program also includes a function to display all contacts in the list.
Learn more about Python program:
brainly.com/question/26497128
#SPJ11
a computer chip uses 1.0 x 105 electrons to store the charge associated with a single bit of information in a square cell within the chip that measures 1.0 x 10-6 m on each side. what is the current density associated with each cell if the computer writes 100 million bits per second, one after the other?
Answers
The current density is 1.0 x 1022 A/m². Computer chips are a crucial component of electronic devices, including computers, smartphones, and other digital devices.
A computer chip is a small piece of semiconductor material, typically made of silicon, that contains integrated circuits. These circuits are used to perform various tasks, such as data processing, storage, and communication. They are responsible for executing instructions and performing operations, making it possible for these devices to function.
To calculate the current density, we need to know the charge and the time required to store each bit of information. We also need to know the area of the cell.
The charge associated with each bit is 1.0 x 105 electrons, so the total charge per second for writing 100 million bits is:
1.0 x 105 electrons x 100 million bits/second = 1.0 x 1010 electrons/second
The area of each cell is 1.0 x 10-6 m x 1.0 x 10-6 m = 1.0 x 10-12 m².
So, the current density is given by:
Current density = Charge per second / Area = (1.0 x 1010 electrons/second) / (1.0 x 10-12 m²) = 1.0 x 1022 A/m².
Learn more about computer chip: https://brainly.com/question/23261568
#SPJ4
Kindles use E-ink technology to display text and images. This technology works by charged pigment spheres migrating across a capsule, bound by electrodes in each pixel. For more information, visit the E-ink website and look at the two-pigment ink system example. When 'flipping pages', the response time of Kindles is discernible. Calculate a) this response time given the assumptions below and b) how does your answer change if the Kindle is facing down instead of up? What does this tell you about the magnitude of the electrostatic force compared to gravitational force acting on the little pigment spheres? - the Kindle is horizontal to ground, facing up so forces act in only one coordinate - steadystate - creeping flow / Stokes regime - D
P
=1.0μm - electrodes are 0.1 mm apart - uniform field across the capsule with V=50 V - fluid in the capsule has viscosity 0.02cP - fluid specific gravity << pigment specific gravity - assume le charge on each pigment sphere - assume pigment sphere specific gravity =1.0
Answers
a) The response time of the kindle is 8.85 seconds when it's horizontal to ground and facing up.
b) The response time of the kindle is not going to change if the Kindle is facing down instead of up as the magnitude of the electrostatic force is much greater than the gravitational force acting on the little pigment spheres.
P=1.0μm,
electrodes=0.1mm,
V=50V,
fluid viscosity=0.02cP,
charges on each pigment sphere and pigment specific gravity=1.0.
Using the creeping flow/Stokes regime for a spherical body (the pigment sphere) of diameter P and density ρP, the settling velocity, v can be calculated by the equation,v= 2/9 (ρP- ρF) g P² / η
Where, ρF= density of the fluid
η=viscosity of the fluid
g=gravitational acceleration=9.81m/s²=9810mm/s².
Using these values,v = 2/9 (ρP-ρF) (9810mm/s²) P² / η
Again, the settling velocity is equal to the distance (P) over the response time (t), so that response time, t = P/v.
Substituting the values,v = 2/9 (1.0g/mL-0.002g/mL) (9810mm/s²) (1x10^-6m)² / (0.02 x 10^-3 Pa s)= 1.13 x 10^-4 mm/s.
Using v, the response time, t is :- t = P/v = (1 x 10^-6 m) / (1.13 x 10^-4 mm/s) = 8.85 s.
The response time of the kindle is 8.85 seconds when kindle is horizontal to ground and facing up.
Learn about the differences between the electrostatic and gravitational forces here : https://brainly.com/question/16345866
#SPJ11
the requested page cannot be accessed because the related configuration data for the page is invalid.
Answers
The statement "the requested page cannot be accessed because the related configuration data for the page is invalid" is definitely true.
What is Data configuration?Data configuration may be defined as the spontaneous description of the structure of two or more datasets together with the relationship between the data sets.
It means that all data and expressions of data that are transmitted, received, or stored within or created by the solution that enable Devices, computers, and Smartcards to function correctly as part of the Solution or that enable applications to be loaded onto Smartcards including system security keys.
Therefore, the statement "the requested page cannot be accessed because the related configuration data for the page is invalid" is definitely true.
To learn more about Data configuration, refer to the link;
https://brainly.com/question/2946751
#SPJ1
How do I fix my session has timed out?
Answers
You might attempt the following generic troubleshooting steps: Reload the page and then clear your browser's cache. 3. Verify the internet connection 4. Verify the session settings. 5. Speak with support.
What is a browser, exactly?An application programme known as a browser offers a way to see and engage with all of the content on the World Global Internet. Web pages, movies, and photos are included in this.
What functions do browsers perform?Anything on the internet is accessible with a web browser. It pulls data from other websites and shows it on your computer or mobile device. The Hyper Text Protocol, which outlines how text, pictures, and video are communicated on the web, is used to send the information.
To know more about browser visit:
https://brainly.com/question/28504444
#SPJ4