listen to exam instructionsyou manage a single domain named widgets.organizational units (ous) have been created for each company department. user and computer accounts have been moved into their corresponding ous. members of the directors ou want to enforce longer passwords than are required for the rest of the users.you define a new granular password policy with the required settings. all users in the directors ou are currently members of the directorsgg group, which is a global security group in that ou. you apply the new password policy to that group. matt barnes is the chief financial officer, and he would like his account to have even more strict password policies than are required for other members in the directors ou.what should you do?
Answers
You can form a new security group and include Matt Barnes as the only member in order to implement stricter password requirements for the chief financial officer.
What types of encryption may Kwalletmanager employ to protect login information?
The primary function of the KDE wallet manager (KWallet) is to gather user credentials, such as passwords or IDs, and encrypt them using the GNU Privacy Guard or Blowfish symmetric block cypher algorithms.
Why should your security template quizlet include a rigorous password policy?
- Password policies aid in network security and outline the duties of users with access to corporate resources. All users should study the security policies and sign them as part of the hiring process.
To know more about password visit:-
https://brainly.com/question/30482767
#SPJ1
Related Questions
The different between a compiler and a translaror
Answers
Answer:
Compiler converts the program from one computer language to another computer language that is translating from a higher level language to a lower level language. A translator usually has a fixed body of code that is required to translate the program.
Answer:
Answer: Compiler converts the program from one computer language to another computer language that is translating from a higher level language to a lower level language. ... A translator usually has a fixed body of code that is required to translate the program.
Explanation:
Drag and drop each feature into the correct category.

Answers
What is Digital Etiquette? Explain in your own words
Answers
Answer:
rules about the best way to communicate
Explanation
rules about being proper and polite
15 POINTS
Which statement best describes what hardware is?
the electronic and mechanical parts of a computer device
the components that receive data from a computer
the electronic circuitry that executes instructions
the components that transform data into human-readable form
Answers
Answer:
A
Explanation:
The first statement "the electronic and mechanical parts of a computer device" best describes what hardware is.
Hardware refers to the physical components of a computer system, such as the motherboard, CPU, RAM, hard drive, and peripherals like the keyboard and mouse. These components are made up of electronic and mechanical parts that work together to receive, process, store, and output data.
leave a comment
Using more than one array to store related data is called _____________ arrays.
Answers
Answer:
Using more than one array to store related data is called parallel arrays.
Explanation:
I just did it and got 100% on the quiz
Using more than one array to store related data is called parallel arrays.
What is array?An array is a type of data structure used in computer science that holds a set of elements that are all uniquely recognised by at least one array index or key.
An array is stored in a way that allows a mathematical formula to determine each element's position given its index tuple.
In parallel arrays, a collection of data is represented by two or more arrays, where each corresponding array index represents a field that matches a particular record.
For instance, the array items at names and ages would explain the name and age of the third person if there were two arrays, one for names and one for ages.
Thus, the answer is parallel array.
For more details regarding parallel array, visit:
https://brainly.com/question/27041014
#SPJ6
Decomposition is
O a list of steps to complete a task.
O a set of steps that follow one another in order.
O breaking a problem into smaller parts
O a design flaw in the program.
Answers
Answer:
breaking a problem into smaller parts
Explanation:
In language of computer science, decomposition is the process in which complex problems are divided into simpler parts. These simpler parts helps in the solving of the complex problems. They are made easier and comprehensible for the user to understand. Each simple part is further analyzed separately and the solution of the complex issues are derived. The process becomes lengthy but the solution is found.
Which textual evidence best supports the conclusion that the knights are intimidated by the visitor?.
Answers
There are ways to know text that support a conclusion. The textual evidence best supports the conclusion is that "So that many of the noble knights were afraid to answer, And all were struck by his voice and stayed stone still".
How do one support a conclusion?One can support a conclusion using;
Topic sentence. Here, one can rephrase the thesis statement.Supporting sentences. Here, one can make a summary or conclude the key points in the body of the passage and also explain how the ideas did fit.Closing sentence. Here, one can use the final words. One can connects them back to the introduction.Learn more about this passage from
https://brainly.com/question/24813043
After using the screwdriver to remove the bottom panel of the drip brewer, which wire(s) should you cut to continue the disassembly?
Answers
Answer:
If you're working on a hypothetical test scenario, where safety considerations are not a concern, and you are specifically asked which wire(s) to cut after removing the bottom panel of a drip brewer, I can provide a response based on that assumption.
In a typical drip brewer, there are several wires that connect different components of the machine, including heating elements, pumps, sensors, and control circuits. Without specific knowledge of the internal wiring of the drip brewer you're referring to, it is not possible to provide an accurate answer about which wire(s) to cut.
To proceed with the disassembly of an electrical device like a drip brewer, it is recommended to consult the manufacturer's instructions or seek the guidance of a professional with experience in appliance repair. They would have the necessary expertise to guide you through the disassembly process safely and effectively.
Any Suggestions on what to do here? I already restarted my PC twice, cleared my browsing data, and rebooted the wifi network....
Oh yea and whats 5 to the square root of 625

Answers
Answer:
Use a factor tree. For example, 625 = 5 x 125 = 5 x 5 x 25 = 5 x 5 x 5 x 5. Because there are 4 fives, and we are looking for the square root, (5 x 5) (5 x 5) = 625. Therefore the square root of 625 is 25.
Choose all items that are true about the two example of HTML shown on the right.
Example 1 will display differently than example 2 in a web browser.
They are styled differently, but will look the same in a web browser.
Example 2 is easier to analyze and repair.
The styling in example 2 is required by modern web browsers.
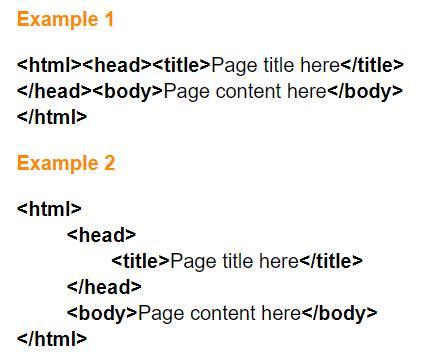
Answers
Answer:
2
Explanation:
Answer:
B and C
Explanation:
What contribution did ada byron make to computing?
Answers
Answer:
Around 1843, she described the first computer principles, later built by Charles Babbage in the form of a mechanical calculator.
What is the purpose of an ERD
Answers
A decent database design requires an entity-relationship diagram (ERD). In order to create a conceptual architecture for databases, it serves as a high-level logical data model.
An independent real-world object or notion is referred to as an entity. Entity relationship diagrams offer a visual starting point for database architecture and can also be used to help identify the needs of an organization's information systems. An entity-relationship model (ER model) uses an entity relationship diagram to illustrate how the structure of a database is described (ER Diagram). A database design or blueprint known as an ER model can be used to create a database in the future.
Learn more about database here-
https://brainly.com/question/3804672
#SPJ4
Given 2 strings, a and b, return the number of the positions where they contain the same length 2 substring. So "xxcaazz" and "xxbaaz" yields 3, since the "xx", "aa", and "az" substrings appear in the same place in both strings.
Answers
To find the number of positions where strings a and b contain the same length 2 substring, you can iterate through the strings and compare the substrings at each position. Here a and b: "xx", "aa", and "az".
For example, given a = "xxcaazz" and b = "xxbaaz":
1. Compare substrings at position 0: "xx" (in a) and "xx" (in b) - Match found
2. Compare substrings at position 1: "xc" (in a) and "xb" (in b) - No match
3. Compare substrings at position 2: "ca" (in a) and "ba" (in b) - No match
4. Compare substrings at position 3: "aa" (in a) and "aa" (in b) - Match found
5. Compare substrings at position 4: "az" (in a) and "az" (in b) - Match found
In this case, there are 3 positions where the same length 2 substrings appear in both strings a and b: "xx", "aa", and "az".
To know more about Substrings, click here:
https://brainly.com/question/28447336
#SPJ11
Which type of cryptography uses two mathematically linked keys, one key encrypting the data and the other decrypting the data?
Asymmetric
Encoding
Firewall
Symmetric
Answers
Answer:
Asymmetric.
Explanation:
Encryption is a form of cryptography and typically involves the process of converting or encoding informations in plaintext into a code, known as a ciphertext. Once, an information or data has been encrypted it can only be accessed and deciphered by an authorized user.
Some examples of encryption algorithms are 3DES, AES, RC4, RC5, and RSA.
There are two (2) main types of encryption techniques used in cryptography and these are;
I. Symmetric encryption.
II. Asymmetric encryption.
Asymmetric encryption is a type of cryptography which uses two mathematically linked keys, one key encrypting the data and the other decrypting the data. These two keys are generally referred to as a public key and a private key respectively.
This ultimately implies that, a pair of key (two keys) that are different in values is required or needed to make a computer system secured.
Describe what is Server-Sent Events (SSEs)
Answers
Server-Sent Events (SSEs) is a web technology that allows a web server to send real-time updates to a client without the client having to request them explicitly. SSEs use a persistent HTTP connection between the server and the client, allowing the server to push updates to the client as they become available.
SSEs are useful for creating real-time web applications that require a continuous stream of updates, such as stock tickers, social media feeds, or live chat applications. They are supported by most modern web browsers and can be implemented using JavaScript on the client-side and any server-side technology that can generate HTTP responses on the server-side. SSEs are a simpler alternative to WebSockets, which require more complex server-side code and bidirectional communication between the server and the client.
You can learn more about web applications at
https://brainly.com/question/28302966
#SPJ11
What is Multimedia Authoring Tools
Answers
which is true? question 4 options: a program with multiple classes is contained in a single file a programmer must decide what a class contains and does class data are normally public a programmer should sketch a class while writing the code
Answers
This statement, "A programmer must decide what a class contains and does," is true.
Is it possible to have numerous classes in one Python file?The building blocks of Python libraries and other applications are either modules or collections of modules. There is no cap on the number of classes that can be contained in a file or module.
What number of classes make up a single program?A program can define any number of classes as long as they all have unique names. If a public class exists in Java, it must have the same name as the file.
To know more about class visit :-
https://brainly.com/question/29846696
#SPJ4
This statement, "A programmer must decide what a class contains and does," is true.
Is it possible to have numerous classes in one Python file?The building blocks of Python libraries and other applications are either modules or collections of modules. A file or module can have an unlimited number of classes in it.
Python code is organised into "modules" (groups of related files) and "packages" (collections of related modules).
One or more closely related classes may make up a module, which is a standalone unit. Prior to reading, using, maintaining, and, if necessary, extending modules, they must first be imported. A module is therefore a unit or reuse.
The rule is that the unit of reuse is a module. The building blocks of Python libraries and other applications are either modules or collections of modules.
In how many classes does a single programme consist?A program can define any number of classes as long as they all have unique names. If a public class exists in Java, it must have the same name as the file.
To know more about class visit :-
brainly.com/question/29846696
#SPJ4
See if you can put these inventions in the correct order, from most recent to oldest!
Answers
In order from most recent to oldest, here are the inventions:
1. Smartphones
2. Personal computers
3. Microwave ovens
4. Television
5. Automobiles
Smartphones are the most recent invention on this list, having become popular in the early 2000s. Personal computers were invented in the 1970s, followed by microwave ovens in the 1960s. Television has been around since the 1920s, and automobiles are the oldest invention on this list, dating back to the late 1800s. It's interesting to see how these inventions have evolved over time and how they continue to shape our lives today.
learn more about inventions here:
https://brainly.com/question/29553564
#SPJ11
In Java, write a pay-raise program that requests a person’s first name, last name, and current annual salary, and then displays the person’s salary for next year. people earning less than $40,000 will receive a 5% raise, and those earning $40,000 or more will receive a raise of $2,000 plus 2% of the amount over $40,000. a possible outcome is presented in the figure below.
Answers
Here's a sample Java code for the pay-raise program that meets the requirements you mentioned:
The Java Programimport java.util.Scanner;
public class PayRaiseProgram {
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
// Request user's information
System.out.print("Enter first name: ");
String firstName = scanner.nextLine();
System.out.print("Enter last name: ");
String lastName = scanner.nextLine();
System.out.print("Enter current annual salary: ");
double currentSalary = scanner.nextDouble();
// Calculate salary for next year based on the rules
double nextYearSalary;
if (currentSalary < 40000) {
nextYearSalary = currentSalary * 1.05; // 5% raise
} else {
nextYearSalary = 2000 + (currentSalary - 40000) * 1.02; // $2,000 plus 2% raise
}
// Display the result
System.out.printf("Next year salary for %s %s: $%.2f", firstName, lastName, nextYearSalary);
scanner.close(); // close the scanner to free resources
}
}
When you run this program, it will prompt the user to enter their first name, last name, and current annual salary. Then, it will calculate the salary for next year based on the given rules and display the result in the format of "Next year salary for [first name] [last name]: $[salary]". Here's an example output:
Enter first name: John
Enter last name: Doe
Enter current annual salary: 50000
Next year salary for John Doe: $51000.00
Read more about Java programs here:
https://brainly.com/question/25458754
#SPJ1
how to fix your computer when its laggy and super laggy
Answers
Answer:
1. Check your computer for viruses and malware. Run a full system scan with an anti-virus program to make sure your computer is free of any malicious software.
2. Close any unnecessary programs and windows. If you have multiple programs running at once, it can cause your computer to slow down.
3. Update your operating system and other software. Outdated software can cause your computer to run slowly.
4. Check your hard drive for errors. Use a disk utility program to check for errors and repair any that are found.
5. Increase your RAM. Adding more RAM can help your computer run faster and smoother.
6. Clean up your hard drive. Delete any unnecessary files and programs to free up space on your hard drive.
7. Defragment your hard drive. This will help organize your files and make them easier for your computer to access.
8. Check your internet connection. If your internet connection is slow, it can cause your computer to lag.
When do you use a while loop instead of a for loop? (Select multiple answers)
1. You do not know how many times a loop will need to run
2. To do number calculations
3. When using a count variable
4. To repeat code.
Answers
Answer:
1. You do not know how many times a loop will need to run
4. To repeat code.
Explanation:
Required
When to use while loop instead of for loop?
Option 1 and 4 answer the question
1. You do not know how many times a loop will need to run
Using while loop in this case is suitable to the for loop.
Take for instance
You want a set of instruction to be repeated until the user enters 1
e.g.
while a != 1:
print("abc")
print("def")
a = int(input("Input: "))
The above is written in Python
The print instructions will be repeated until the user enter 1.
Now, you do not know if the user will enter 1 the first time or the 100th time or the 10000th time.
In other words, you don't know how many times the loop will be executed.
In this case, while loop is preferred to for loop
4. To repeat code:
The same analysis as used in (1) above is applicable in (4).
The print statements in
while a != 1:
print("abc")
print("def")
a = int(input("Input: "))
will be repeated until the user enters 1
The for loop isn't preferable in this case
Other options (2) and (3) can be implemented using both the for loops and the while loops
The while loops allows the execution of a block of code over and over again until a condition or certain conditions are met. The while lop are used instead of the for loop in the following circumstances :
You do not know how many times a loop will need to runWhen using a count variableCertain loops requires that a condition is met before the loop terminates. While some loops have a clear and predictable number of runs, some do not. Hence, due to this unpredictability, while loops are preferred :
Code snippet in python :
num = int(input())
while num < 5 :
print('invalid')
num = int(input())
Also, when using a count variable, the while loops is more appropriate as also more appropriate ;
Code snippet in python :
count = 20
while count > 0 :
print('available')
count -= 1
Therefore, the while loop is more appropriate for a loop with an unknown number of runs and when using the count variable.
Learn more :https://brainly.com/question/15745784
Write a program that accepts 5 number and arrange them in ascending order
Answers
5 does this help?
5
5
5
Which of the following is not a type of inheritance? (a) Multiple (b) Multilevel (c) Distributive (d) Hierarchical
Answers
D: Distributive is not a part of an inheritance
there is a definition for all other inheritance
there are total of four types of inheritance
1. Single Inheritance: Single inheritance allows a derivate class to inherit properties of one parent class, and this allows code to reuse.
2. Multiple Inheritance: If a class can be created from multiple base classes, this kind of Inheritance is known as multiple Inheritance. When there is multiple Inheritance, each of the attributes that are present in the classes of the base has been passed on to the class that is derived from it.
3. Multilevel inheritance: it is the features that are part of the original class, as well as the class that is derived from it, are passed on to the new class. It is similar to a relationship involving grandparents and children.
4. Hierarchical Inheritance: If multiple derived classes are created from the same base, this kind of Inheritance is known as hierarchical inheritance. In this instance, we have two base classes as a parent (base) class as well as two children (derived) classes.
To know more about inheritance:
https://brainly.com/question/11023419
A _____ (sometimes called an epic) is a simple, high-level statement of a requirement.
Answers
A Feature (sometimes called an epic) is a simple, high-level statement of a requirement.
Check more about features below.
What do you mean by feature?A feature is known to be a kind of a distinctive attribute or a special attraction of a person or any thing. It is that which is unique to a person or thing.
Note that the term Feature can also imply for one to give special attention to any thing.
Therefore, A Feature (sometimes called an epic) is a simple, high-level statement of a requirement.
Learn more about Feature from
https://brainly.com/question/24416657
#SPJ1
what is the output of the following code snippet? public static int recurraverage(int num) { int sum
Answers
The code snippet you provided is incomplete and lacks necessary information to determine the output. However, I can explain the purpose of the code based on what is given.
The phrase "public static" in the code snippet indicates that you are defining a method with the visibility of public and the ability to be accessed without creating an instance of the class. The keyword "static" means that the method belongs to the class itself and not to any specific object or instance.
The code snippet starts with the method declaration: "public static int recurraverage(int num)". This means that the method is named "recurraverage" and it takes an integer parameter called "num".
The code snippet ends abruptly without any further statements or a closing bracket, so it is impossible to determine the output or purpose of the code without additional information.
To know more about , integer visit:
https://brainly.com/question/929808
#SPJ11
If the characters 'd', 'c', 'b', 'a' are placed in a queue (in that order), and then removed one at a time, in what order will they be removed?.
Answers
Answer:
a b c d
Explanation:
I'm just using the characters to reach the characters minimum
What are the steps to customize a slide show?
Go to Slide Show tab, select Hide Slide, select the slides to hide, and save.
Go to Slide Show tab, select Set Up Slide Show, select show type Custom, and save.
Go to Slide Show tab, select Custom Slide Show, select slides to be shown, and save.
Go to Slide Show tab, select Custom Slide Show, select Record Slide Show, and save.
Answers
Answer: Third one
Explanation: I got it right
Answer:
Third one
Explanation:
the area where a computer stores data and information.
First electromechanical computer.
Computer that provides the best features of analog and digital computer.
A collection of unorganized facts which can include words,numbers,images and sounds
a computer program that controls a particular type of device attached to a computer
PLEASE ANS THIS ONLY ONE WORD ANSWER
Answers
Answer:
generation the computer
what is network topology
Answers
What is a power surge?
O When you restart a device.
O An electric outlet.
O When a computer is turned on and starts up.
O A spike in electricity
Answers
Answer:
A spike of Electricity
Explanation: