primary memory, which holds program instructions and data, is not associated with the central processing unit (cpu). T/F
Answers
False: Primary memory is associated with the central processing unit (CPU).
Primary memory, also known as main memory or RAM (Random Access Memory), is directly connected to the CPU. It holds program instructions and data that the CPU needs to access and manipulate during its operations.
The CPU interacts with the primary memory to fetch instructions, store data, and perform calculations. When a program is executed, its instructions are loaded from secondary storage (like a hard drive) into the primary memory to be processed by the CPU. The CPU retrieves instructions and data from the primary memory, performs operations on them, and stores the results back into the primary memory.
Know more about Primary memory here:
https://brainly.com/question/31533701
#SPJ11
Related Questions
how many seconds are spent if we have n disks?
Answers
The largest number of disks that can be solved within 10 seconds using the Tower of Hanoi formula T(n) = 2^n - 1 is 7 disks.
Using the formula T(n) = 2^n - 1 to calculate the number of seconds required to solve the Tower of Hanoi puzzle with increasing numbers of disks, we can find that the largest number of disks that can be solved within 10 seconds is 7 disks.
To see why, we can calculate T(n) for each n starting from 1 and increasing until T(n) is greater than 10. We get:
T(1) = 1T(2) = 3T(3) = 7T(4) = 15T(5) = 31T(6) = 63T(7) = 127Since T(7) is the first T(n) value that is greater than 10, we know that the largest number of disks that can be solved within 10 seconds is 7 disks.
Q: What is the largest number of disks that can be solved within 10 seconds to implement the solution to the Tower of Hanoi problem?
Learn more about disks: https://brainly.com/question/28493309
#SPJ11
One of the advantages of communicating using social media is that you can use it to
a create a fake website
b promote and share your ideas
c push someone to do something he or she doesn't want to do
dshare your personal information
Answers
Answer:
b is correct because you can promote your ides others
True or False? You should never move an injured person.
True
False
Answers
Answer:
true
Explanation:
Project stem 4.1 code practice
Python!!
Write a program that asks the user to enter a city name, and then prints Oh! CITY is a cool spot. Your program should repeat these steps until the user inputs Nope.
Sample Run
Please enter a city name: (Nope to end) San Antonio
Oh! San Antonio is a cool spot.
Please enter a city name: (Nope to end) Los Angeles
Oh! Los Angeles is a cool spot.
Please enter a city name: (Nope to end) Portland
Oh! Portland is a cool spot.
Please enter a city name: (Nope to end) Miami
Oh! Miami is a cool spot.
Please enter a city name: (Nope to end) Nope
Answers
A program that the user to enter a city name, and then prints Oh! CITY is a cool spot as follows:
City_name = input("Please enter a name or type Nope to terminate the program: ")
while( user_name != "Nope" ):
print("Oh! CITY is a cool spot" , City name)
City name = input("Please enter a name or type Nope to terminate the program: ")
What is a Computer Program?A computer program may be defined as a series or set of instructions in a programming language that are utilized by the computer to execute successfully.
The variable "City_name" is used to store the input of the user. He might input his name or "NOPE" to terminate. Then we used a while loop to check if the user input NOPE. Then, we print Oh! CITY is a cool spot for "users input".
Therefore, a program that the user to enter a city name, and then prints Oh! CITY is a cool spot is well-described above.
To learn more about Computer programs, refer to the link:
brainly.com/question/1538272
#SPJ1
2. INFERENCE (a) The tabular version of Bayes theorem: You are listening to the statistics podcasts of two groups. Let us call them group Cool og group Clever. i. Prior: Let prior probabilities be proportional to the number of podcasts each group has made. Cool made 7 podcasts, Clever made 4. What are the respective prior probabilities? ii. In both groups they draw lots to decide which group member should do the podcast intro. Cool consists of 4 boys and 2 girls, whereas Clever has 2 boys and 4 girls. The podcast you are listening to is introduced by a girl. Update the probabilities for which of the groups you are currently listening to. iii. Group Cool does a toast to statistics within 5 minutes after the intro, on 70% of their podcasts. Group Clever doesn't toast. What is the probability that they will be toasting to statistics within the first 5 minutes of the podcast you are currently listening to? Digits in your answer Unless otherwise specified, give your answers with 4 digits. This means xyzw, xy.zw, x.yzw, 0.xyzw, 0.0xyzw, 0.00xyzw, etc. You will not get a point deduction for using more digits than indicated. If w=0, zw=00, or yzw = 000, then the zeroes may be dropped, ex: 0.1040 is 0.104, and 9.000 is 9. Use all available digits without rounding for intermediate calculations. Diagrams Diagrams may be drawn both by hand and by suitable software. What matters is that the diagram is clear and unambiguous. R/MatLab/Wolfram: Feel free to utilize these software packages. The end product shall nonetheless be neat and tidy and not a printout of program code. Intermediate values must also be made visible. Code + final answer is not sufficient. Colours Use of colours is permitted if the colours are visible on the finished product, and is recommended if it clarifies the contents.
Answers
(i) Prior probabilities: The respective prior probabilities can be calculated by dividing the number of podcasts made by each group by the total number of podcasts made.
(ii) Updating probabilities based on the gender of the podcast intro: Since the podcast intro is done by a girl, we need to calculate the conditional probabilities of the group given that the intro is done by a girl.
(iii) Probability of toasting to statistics within the first 5 minutes: Since Group Cool toasts on 70% of their podcasts and Group Clever doesn't toast, we can directly use the conditional probabilities.
Group Cool: 7 podcasts
Group Clever: 4 podcasts
Total podcasts: 7 + 4 = 11
Prior probability of Group Cool: 7/11 ≈ 0.6364 (rounded to four decimal places)
Prior probability of Group Clever: 4/11 ≈ 0.3636 (rounded to four decimal places)
(ii) Updating probabilities based on the gender of the podcast intro: Since the podcast intro is done by a girl, we need to calculate the conditional probabilities of the group given that the intro is done by a girl.
Group Cool: 4 girls out of 6 members
Group Clever: 4 girls out of 6 members
Conditional probability of Group Cool given a girl intro: P(Group Cool | Girl intro) = (4/6) * 0.6364 ≈ 0.4242 (rounded to four decimal places)
Conditional probability of Group Clever given a girl intro: P(Group Clever | Girl intro) = (4/6) * 0.3636 ≈ 0.2424 (rounded to four decimal places)
(iii) Probability of toasting to statistics within the first 5 minutes: Since Group Cool toasts on 70% of their podcasts and Group Clever doesn't toast, we can directly use the conditional probabilities.
Probability of toasting within the first 5 minutes given Group Cool: P(Toasting | Group Cool) = 0.70
Probability of toasting within the first 5 minutes given Group Clever: P(Toasting | Group Clever) = 0
The overall probability of toasting within the first 5 minutes of the podcast you are currently listening to can be calculated using the updated probabilities from step (ii):
P(Toasting) = P(Toasting | Group Cool) * P(Group Cool | Girl intro) + P(Toasting | Group Clever) * P(Group Clever | Girl intro)
= 0.70 * 0.4242 + 0 * 0.2424
≈ 0.2969 (rounded to four decimal places)
The prior probabilities of Group Cool and Group Clever were calculated based on the number of podcasts each group made. Then, the probabilities were updated based on the gender of the podcast intro. Finally, the probability of toasting to statistics within the first 5 minutes of the current podcast was estimated using the conditional probabilities.
To know more about Prior Probabilities, visit
https://brainly.com/question/29381779
#SPJ11
Mikayla wants to create a slide with a photograph of a car and the car horn sounding when a user clicks on the car. Which feature should she use, and why?
Answers
Since Mikayla wants to create a slide with a photograph of a car and the car horn sounding when a user clicks on the car. The feature should she use is c. She should use the Action feature because it allows a user to place an image map with a hotspot on the car.
What is the feature about?The Action functionality found in software designed for creating slides commonly permits its users to generate dynamic components like hyperlinks or hotspots on images or objects included in a slide.
Mikayla aims to design an interactive presentation slide that activates a car horn sound effect upon clicking on the vehicle. To attain this functionality, she could incorporate an image map on the car and create a hotspot using the Action feature.
Learn more about feature from
https://brainly.com/question/10439235
#SPJ1
See full text below
Mikayla wants to create a slide with a photograph of a car and the car horn sounding when a user clicks on the car. Which
feature should she use, and why?
a. She should use the Action feature because it allows a user to embed a hyperlink for an Internet video on the car.
b. She should use the Video from Website feature because it allows a user to embed a hyperlink for an Internet video on the car.
c. She should use the Action feature because it allows a user to place an image map with a hotspot on the car.
d. She should use the Video from Website feature because it allows a user to place an image map with a hotspot on the car.
a packet analyzer is a program that can enable a hacker to do all of the following except ________.
Answers
A packet analyzer is a computer network that has the ability to intercept and log traffic that flows through the network of a computer. A packet analyzer is a program that can enable a hacker to do all of the following except;
D) Launch a denial of service (DoS) attack on your computerSince it is able to read and capture the raw data moving through a network, hackers can use a packet analyzer to decode the details in a user's debit card.
Identity theft can be executed and passwords can be captured using this program.
However, the computer's network cannot be shut down with this program. Therefore, option D is right.
Options:
A) Use your debit card information to purchase items illegally
B) Assume your identity
C) Steal your logons and passwords for various accounts
D) Launch a denial of service (DoS) attack on your computer
Learn more here:
https://brainly.com/question/14390016
You have to insert the author's name at the bottom of all the pages of an article
prepared in the word processor. Which of the following tools is the most suitable
for this?
a) Footer
b) Merge Cells
c) Insert Rows
d) Header
Answers
Answer:
Footer
Explanation:
how does the x-ray involve with science, technology, math, and engineering
Answers
Answer:
hope it helps
Explanation:
engineering: to show flaws that cannot be detected by bare eye
technology: to automatically control the density or thickness of layers of substance
science: to generate images of tissue and structure inside the body
i need help here it is To earn 100% on this sample work, you should attend an In and Out with me to answer questions about hardware, software, cyber security, input, etc.
This is either 100% or 0%. As a reminder, In and Out is M-Th at 11:30am. what can i put
Answers
Hardware: refers to the physical components of a computer system, including the central processing unit (CPU), memory, storage devices (such as hard drives or solid-state drives), input/output devices (such as monitors, keyboards, and mice), and other components.
What is Software?This refers to the programs, applications, and other instructions that tell a computer system what to do.
This includes everything from operating systems (such as Windows, macOS, or Linux) to productivity tools (such as Micrft Office or Ggle Docs) to video games and other entertainment software.
Cyber security: refers to the practice of protecting computer systems and networks from unauthorized access, theft, and damage. This can include measures such as firewalls, antivirus software, encryption, and other security protocols.
P.S: I believe your question is about finding out more about hardware, software, cyber security, input and other related information, maybe for an interview
Read more about cybersecurity here:
https://brainly.com/question/28004913
#SPJ1
PLEASE HELP! ITS A COMPUTER MCQ
The character that is displayed at the end of the code for continuation.
a. :
b. ;
c. .
d. ,
Answers
Answer:
b. ;
Explanation:
PLEASE MARK ME AS BRAINLIEST
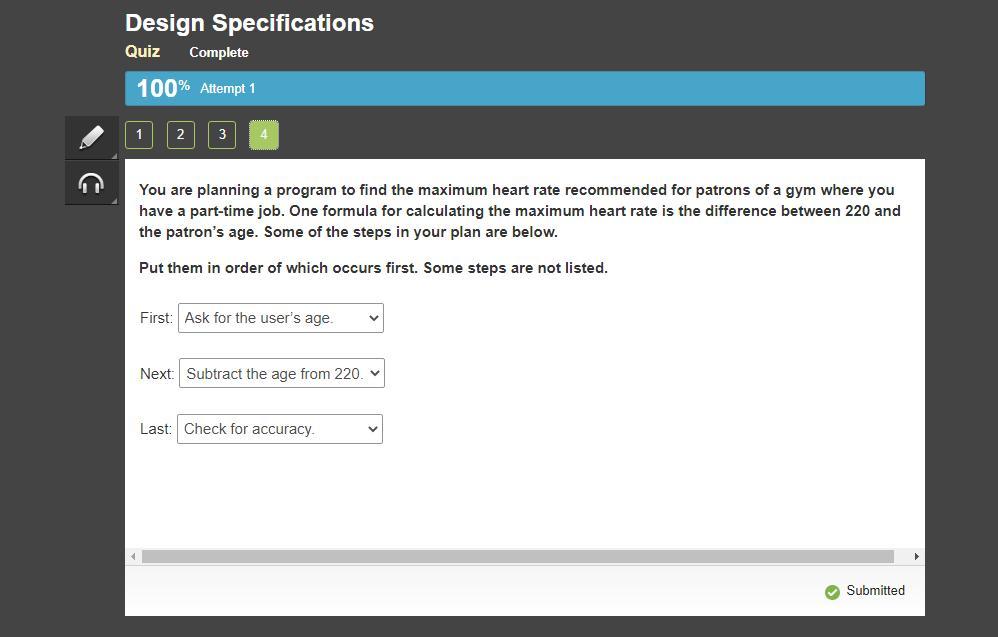
You are planning a program to find the maximum heart rate recommended for patrons of a gym where you have a part-time job. One formula for calculating the maximum heart rate is the difference between 220 and the patron’s age. Some of the steps in your plan are below.
Put them in order of which occurs first. Some steps are not listed.
Answers
Answer:
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Explanation:
The programs will be as follows
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Answer:
got 100 on the quiz
Explanation:
Who is the smartest avenger??? :)
Answers
Answer:
Iron Man
Explanation:
Answer:
Tony Stark, he figured out time travel, built fighting suits, figured out how to defeat Thanos, the list goes on
Explanation:
what pc models have a speed of at least 3.00?
Answers
It is not possible to provide an accurate answer to this question without more information, since the speed of a PC depends on many factors, such as the processor, RAM, hard drive and graphics card. Also, it's not common to use speed as the only measure of PC performance, as there are many other factors that can affect its performance.
However, it is possible to identify some PC models that have high speed and good performance.
For example, some of the most popular brands today are Apple, Dell, HP, Lenovo, and Asus, each offering different models with different hardware specifications and speeds. In addition, it is important to note that the speed of a PC is not the only factor that determines its performance, since the processing power, the amount of memory and the type of storage are also important.
In conclusion, it is not possible to provide an accurate answer on which PC models have a speed of at least 3.00 without more information. It is important to note that speed is not the only factor that determines the performance of a PC, and that the choice of a suitable PC model depends on the individual needs of each user.
Lear More About Pc Models
https://brainly.com/question/22946942
#SPJ11
State the meaning of (1) plaintext (in) encryption (iii) decryption
Answers
(1) Plain text is a term that refers to text that has not been encrypted or coded. Plain text is plain, simple, and straightforward. It can be interpreted and read by anybody.
Plaintext is the data that is going to be encoded, while ciphertext is the data that has already been encoded (encrypted).Encryption is the process of converting plain text into a coded language (ciphertext) so that it can only be read by authorized people. In cryptography, encryption is the procedure of encoding information so that it becomes unreadable to anybody except the intended recipient.
(iii) Decryption is the process of converting encrypted or coded information (ciphertext) back into readable text (plaintext). In cryptography, decryption is the process of converting ciphertext into plaintext, which is the original message or data. When an encrypted message is received, it must be decrypted in order to be read by the receiver.
To know more about coded visit:
https://brainly.com/question/31228987
#SPJ11
Which can occur in a physical change?
The mass can increase.
The particles can arrange in different ways.
The mass can decrease.
The atoms can bond to different atoms.
Answers
Answer:
particles can arrange in different ways.
Explanation:
Where does Reiner take eren after they have a fight?
Answers
Answer:
So Reiner And Bertoldt wanted to take Eren and Ymir to Marley, a nation on the other side of the ocean so they can be devoured and there power can be given to a warrior canidate.
Answer:
what season tho?
Explanation:
Reiner took eren to the Forest
one security component that doubles as a network component
Answers
Answer:
is the sentence above the question?
Answer:
It is to enter the site and then it will protect you in terms of form and appearance, and so on as required
Select the correct answer.
Which use of conditional statements help create programs that are more robust?
A output validation
B. printing
C. input validation
D block structure
Answers
Answer:
c
Explanation:
when importing a text file, why is it important to move through each step of the text import wizard? power bi
Answers
A data management tool called Data Import Wizard is included in Salesforce's Setup menu.
How do I use text import wizard?the Data tab > Get & Transform Data > Get Data > Legacy Wizards > From Text when it has been enabled (Legacy). The Text Import Wizard will then launch once you double-click the text file you wish to import in the Import Text File dialog box.You may import data from a Microsoft Excel spreadsheet to a worksheet grid with the help of the Import Wizard. Choose the spreadsheet you wish to import in the wizard, then either use the default template or create your own template. You can store the templates you make for later use.To learn more about Data Wizard refer,
https://brainly.com/question/29305580
#SPJ4
This is a multi-step question. Be careful! You only get two wrong clicks. Each time you make a wrong click, you'll see a red 'X' on the screen.
Agatha needs to find out which month has the highest attendance of visitors to the museum. The spreadsheet shows the monthly attendance for the museum for the last ten years. Agatha has selected the right cells, but she is stuck. Help her find the average of monthly museum visitors for the last ten years. Now, turn that cell red so that the data stands out
Answers
To help Agatha find the average of monthly museum visitors for the last ten years, you should calculate the average using the selected cells and then turn that cell red to make it stand out.
To calculate the average of monthly museum visitors, you need to use the selected cells that contain the attendance data for the last ten years.
These cells likely form a range or a column. You can sum up the values in the selected cells and then divide the sum by the number of months to find the average.
Once you have calculated the average, you can format the corresponding cell by turning it red to highlight it and make the data stand out.
This will help Agatha easily identify the average attendance for the museum over the given period.
Learn more about data here: brainly.com/question/29117029
#SPJ11
Which of the following describes all illustrations created by freehand?
extension lines
sketches
leader lines
dimensions
Answers
1. Edra started to create named ranges in the worksheet and has asked you to complete the work. Create a defined name for the range B6:E6 using Walkup as the range name. 2. Create names from the range AZ:E9 using the values shown in the left column. 3. Apply the defined names 01 Salec 09 Salos na CERRADA = 70 0 Paste Font Alignment Number Format as Table Cell Styles Cells Editing Analyze
Answers
To create a defined name for the range B6:E6 using Walkup as the range name, follow these steps:Select the range B6:E6.Click on the "Formulas" tab in the ribbon menu.
Click on the "Define Name" button in the "Defined Names" group.In the "New Name" dialog box, type "Walkup" in the "Name" field.Ensure that the "Refers to" field shows the correct range B6:E6.Click "OK" to create the defined name "Walkup" for the range B6:E6.To create names from the range AZ:E9 using the values shown in the left column, follow these steps:Select the range AZ:E9.Click on the "Formulas" tab in the ribbon menu.Click on the "Create from Selection" button in the "Defined Names" group.In the "Create Names" dialog box, select the "Left column" option.Ensure that the "Top row" option is deselected.Click "OK" to create the defined names based on the values in the left column.To apply the defined names, follow these steps:Select the range of cells you want to apply the defined names to.Click on the "Home" tab in the ribbon menu.Click on the "Find & Select" button in the "Editing" group.Click on the "Replace" option.In the "Find what" field, type the cell value you want to replace, such as "01".In the "Replace with" field, type the defined name you want to apply, such as "Salec".Click "Replace All" to apply the defined name to all matching cells.Repeat steps 5-7 for each defined name you want to apply.
To learn more about Walkup click the link below:
brainly.com/question/27982849
#SPJ1
These are used to section the hair to make application of the color easier.
Answers
Answer:
Sectioning Clips
Explanation:
These are used to make segments or sections in the hair so that applying the color will be easier
which keyboard shortcut undoes an action made to a selection?
Answers
To undo an action, press Ctrl + Z. To redo an undone action, press Ctrl + Y.
What is the significance of Undo Ctrl Z?It is most likely based on the key location of other widely used keyboard commands (cut, copy, paste). It's most likely all about positioning on a QWERTY keyboard. Probably based on the key position of other regularly used keyboard commands (cut, copy, paste). It's most likely all about positioning on a QWERTY keyboard.
The keyboard shortcut for the Find command is "Control+F" (or "Command+F" on a Mac). When you're in a document or a web browser, click Ctrl + F to bring up a search box in the upper right corner of the screen.
To learn more about Ctrl Z to refer:
https://brainly.com/question/30293440
#SPJ4
Can anyone please help me on these two questions it would really help xxx

Answers
Answer: No one can interpret or hack it.
Explanation:
Because there is nothing to hack.
take it from someone who hack their teachers laptop as a dare. It was so easy.
A(n) _____ is a computerized system by which subscribers are able to communicate to all other subscribers by sending a transmission to one address
Answers
Answer: Listerv
Explanation:
Which image format is most commonly used for logos, typography, fonts and illustrations?.
Answers
Vector format is the most commonly used for logos, typography, fonts and illustrations.
Brief response on image formats
Vector format is used for logos, typography, fonts and illustrations because of two advantages with respect to other formats:
Images are not pixel-based, but based on vector formulas. No resolution is lost when image is resized.Thus, vector format is the most commonly used for logos, typography, fonts and illustrations. \(\blacksquare\)
To learn more on images, we kindly invite to check this verified question: https://brainly.com/question/25029470
Sure, here's an essay outline that you can use to write your essay on repairing a damaged relationship and regaining trust: daep 5'rs
I. Introduction
- Briefly explain the importance of respect, responsibility, and trust in relationships
- Explain the purpose of the essay: to outline a plan for repairing a damaged relationship and regaining trust
II. Identify the damaged relationship
- Explain the situation that damaged the relationship and the impact it had on both parties
- Acknowledge any mistakes made and take responsibility for them
III. Identify the areas that need repair
- Discuss the specific areas of the relationship that need repair
- Identify any areas where you may need to change your behavior or mindset in order to repair the relationship
IV. Develop a plan for repairing the relationship
- Discuss specific actions you can take to repair the relationship
- Set goals and a timeline for these actions
- Identify any resources or support you may need to accomplish these goals
V. Discuss strategies for regaining trust
- Acknowledge the impact of the damage on the trust in the relationship
- Discuss specific actions you can take to rebuild trust
- Set goals and a timeline for these actions
VI. Discuss strategies for reintegration
- Explain how you will work to reintegrate yourself back into the relationship
- Identify any potential challenges or obstacles and how you plan to overcome them
VII. Conclusion
- Summarize your plan for repairing the relationship and regaining trust
- Emphasize the importance of taking responsibility and being proactive in repairing damaged relationships
Remember to be honest and sincere in your essay, and to take ownership of any mistakes or actions that contributed to the damaged relationship. Good luck with your essay and the process of repairing your relationship!
Answers
The essay on repairing a damaged relationship and regaining trust is given below.
What is the essay captioned above?Repairing a ruptured bond takes courage and commitment; it calls for adopting an effective approach that seeks mutual resolution toward building trust between two parties.
Acknowledging accountability for one's actions plays a pivotal role in restoring any damaged bond while noting its effect on another individual involved in the broken relationship building process through goal-setting underlines this process more profoundly.
Maintaining transparency when communicating whilst being considerate towards fulfilling commitments influences rebuilding lost faith within such partnerships positively.
With dedication guided by patient open-mindedness towards listening actively during conversation exchanges greatly impacts repairing such bonds.
Learn more about Essays:
https://brainly.com/question/20441249
#SPJ1
HELPPPPPPPPPPP
Multiple choice
One question
