The day-to-day relationships that develop in an organization but are not listed on an organization chart are called the firm's _____ organization. informal.
Answers
The day-to-day relationships that develop in an organization but are not listed on an organization chart are called the firm's informal organization.
The informal organization can be defined as the social structure of an organization. Informal relationships exist between people within the organization as they get to know one another and share their experiences. People who are part of an informal organization have regular interactions that are not necessarily related to the organization's official chart.
The informal organization is also referred to as the grapevine. The grapevine is a term used to describe the informal communication network that exists within a company. It is an unstructured and unofficial way for employees to exchange information, rumors, and gossip.
The grapevine spreads information rapidly, making it a valuable tool for management to understand what is happening within the company. However, the grapevine can also be a source of misinformation and rumors. To ensure that accurate information is disseminated, it is important for management to monitor the grapevine and correct any inaccuracies.
Learn more about The informal organization:https://brainly.com/question/28077010
#SPJ11
Related Questions
Which of the following statements represents the pros and cons of Internet regulations?

Answers
Answer:
Internet regulations increase net security but lead to monopolizing of services.
Explanation:
Internet regulations can be defined as standard rules or laws that restricts or control the use of the internet, as well as stating the acceptable usage of the internet in a particular location.
The pros and cons of Internet regulations is that, Internet regulations increase net security through the use of encryption and authentication proceses but lead to monopolizing of services.
A monopoly is a market structure which is typically characterized by a single-seller who sells a unique product in the market by dominance. This ultimately implies that, it is a market structure wherein the seller has no competitor because he is solely responsible for the sale of unique products without close substitutes. Any individual that deals with the sales of unique products in a monopolistic market is generally referred to as a monopolist.
For example, a public power company is an example of a monopoly because they serve as the only source of power utility provider to the general public in a society.
Answer:
Regulatory practices provide more security for the consumer but may create monopolies in the industry, reducing consumer choice.
Explanation:
edg2021
Internet regulations increase net security but could lead to monopolizing of services. Properly done, Internet regulations benefit industry, government, and consumers by providing more online security, regulating prices for services, and decreasing liability. However, some regulations could also lead to unfair service practices, slow technological advances, and possibly contribute to technology monopolies.
What is a project?
Answers
Help PLEASE ILL MARK as brainlest

Answers
Answer:
computer animation (3d)
What is omitted from a typical triathlon to create a duathlon?
Answers
A duathlon involves running, riding, and then running again, whereas a triathlon comprises swimming, cycling, and running.
A triathlon combines swimming, cycling, and running whereas a duathlon consists of running, riding, and running again. In a duathlon, the swimming leg is skipped, and competitors begin with a running leg before moving on to cycling and another running leg. This alteration to the classic triathlon format may be necessary owing to the lack of sufficient swimming facilities, or it may be done to make the competition more accessible to people who dislike swimming or would rather concentrate on running and cycling. As an alternative to triathlons, duathlons are well-liked and give competitors a demanding but doable multisport experience.
learn more about duathlon here:
https://brainly.com/question/31238755
#SPJ4
How are Windows applications made?
Answers
The windows applications are made by these steps:
Discovery, Project planning, Windows application design development planning, UX and UI design, Development and QA, Launch and Evolution.These steps are known as Organization steps in making windows applications.
Talented need to make Windows Applications are:
Business consultant, Project manager,Software architect, UX designer, UI designer, DevOps engineer, Software developer, QA specialist.The essential displays of the future Windows app are wireframed by UX designers using data from the SRS and user research, and the screens are then combined into a single interactive experience using prototype tools. The built prototype should pass rigorous usability testing because this is when UX problems that are crucial to the success of the app are easiest to fix.
After conducting usability testing and making extensive adjustments, UI designers continue to work on the prototype and replace the rough sketches with high-fidelity visuals. When finished, they give the development team access to the GUI mockups, UI elements, and interface control specifications.
To learn more about Windows applications click here:
brainly.com/question/22928852
When an application has multiple uses what is it known as?.
Answers
Answer:
an application that had multiple uses is called full featured
an error occurred while loading a higher quality version of this video
Answers
Answer:?
Explanation:?
Explain why this scenario could put an organization in jeopardy of losing some of its workforce.
Situation: The IT manager decides to add a new software application to replace an older albeit less efficient software application.
Answers
Answer:
Not educating its employees on the new software.
FILL IN THE BLANK. when creating a patch job, a "patch window" set to the __________ option, will allow the cloud agent as much time as it needs to complete the job?
Answers
When creating a patch job, a "patch window" set to the Unlimited option, will allow the cloud agent as much time as it needs to complete the job.
What is a "patch window"?During the next patch windows, instances in a specific patch group are patched. Patch windows run on a schedule defined as a crn r rate expressing and have a configurable duration intended to keep patching-related disrupting within a specified time interval.
AMS recommends creating multiple patch windows that collectively cover all of your instances, are tailored to your organization's patching routines, and use the default maintenance window as a fallback.
The RFC change type Deplyment | Patching | SSM patch windw | Create is used to create patch windows (ct-0el2j07llrxs7). All instances that are not part of a patch window are patched during the barding default maintenance window.
Learn more about patch window
https://brainly.com/question/30667370
#SPJ4
To qualify as a professional Android developer, you need to get _____
certification.
Answers
Answer:
proficiency
Explanation:
The need for a functioning computer in countries having different electrical systems is an example of a ________.
Answers
It should be noted that Technical requirements serves as a need for a functioning computer in countries having different electrical systems.
What is Technical requirements?Technical requirements can be regarded as a technical issues which is required in completing a project.
It entails aspects such as performance, reliability, and availability of functioning computer.
Learn more about Technical requirements at:
https://brainly.com/question/26550671
most mobile devices can track your location unless you turn off the so-called _____ services.
Answers
Mobile devices can track your location using built-in GPS and other technologies like Wi-Fi and Bluetooth through the so-called location services.
Location services provide valuable features, such as navigation, weather updates, and targeted advertising. However, privacy concerns arise when these services are enabled, as they can reveal your whereabouts to third parties
. To maintain your privacy, you can disable location services in your device's settings. By doing so, you prevent apps and websites from accessing your real-time location data.
Keep in mind, though, that turning off location services may limit the functionality of certain apps that rely on your location information.
Learn more about location tracking at
https://brainly.com/question/14575671
#SPJ11
Lab 1-4: testing mode: identify parts inside a laptop and an all-in-one computer
Answers
The parts that can be found inside a laptop and an all-in-one computer include the following:
Random access memory (RAM).Read only memory (ROM).Central processing unit (CPU).Motherboard BIOS chip.CMOS battery.The types of computer.Generally, there are two (2) types of computer and these include the following:
Desktop computerLaptop computerWhat is a laptop?A laptop can be defined as a small, portable type of computer that is designed and developed by embedding both a mousepad, processor, and keyboard on it. Additionally, a laptop is usually light enough to be placed on an end user's lap while he or she is working, traveling, gaming, etc.
What is an all-in-one computer?An all-in-one computer can be defined as a form of desktop computer that is designed and developed to have each of its internal hardware component within the same case as the monitor, except for peripheral components (external devices) such as a mouse and keyboard.
In Computer technology, the parts that can be found inside a laptop and an all-in-one computer include the following:
Random access memory (RAM).Read only memory (ROM).Central processing unit (CPU).Motherboard BIOS chip.CMOS battery.Read more on all-in-one computers here: brainly.com/question/4581809
#SPJ1
Match the job roles with their appropriate qualifications.
business analyst
multimedia artist
network and computer systems administrator
software quality assurance engineer
Answers
Answer:
business analyst: degree in business administration
multimedia artist : training in 2D and 3D modeling
network and computer systems administrator: master's course in management information systems
software quality assurance engineer: knowledge of the software life cycle process
Explanation:
Write a program that hardcodes a proposed password and checks that it is an acceptable password.
If the proposed password is acceptable password, the program writes a message "Password zzzzzzzzz is acceptable" and ends.
If it is not acceptable, it writes a message "Password is acceptable because it "
Where
is the password which was checked.
is one of:
"is not at least 7 characters long."
"does not contain both upper and lower case alphabetic characters."
"does not contain at least 1 digit."
is used if the PW is not acceptable, else the word not isn't printed.
"is an acceptable password."
Acceptable passwords:
are at least 7 characters long.
contain both upper and lower case alphabetic characters.
contain at least 1 digit.
The logic of this program can be quite tricky. Hint: use toUpperCase(), toLowerCase, and equals(). You will also need nested ifs.
Here some sample runs of the program; your output should look substantially the same:
C:\>java PasswordChecker
Enter your password:
snowflake
Password snowflake is not acceptable because it does not contain both upper and lower case alphabetic characters."
Enter your password:
SnowFlake
Answers
Using the knowledge in computational language in JAVA it is possible to write the code that write a program that hardcodes a proposed password and checks that it is an acceptable password.
Writting the code:
class InvalidPasswordException extends Exception {
int passwordConditionViolated = 0;
public InvalidPasswordException(int conditionViolated)
{
super("Invalid Password: ");
passwordConditionViolated = conditionViolated;
}
public String printMessage()
{
switch (passwordConditionViolated) {
case 1:
return ("Password length should be"
+ " between 8 to 15 characters");
case 2:
return ("Password should not"
+ " contain any space");
case 3:
return ("Password should contain"
+ " at least one digit(0-9)");
case 4:
return ("Password should contain at "
+ "least one special character");
case 5:
return ("Password should contain at"
+ " least one uppercase letter(A-Z)");
case 6:
return ("Password should contain at"
+ " least one lowercase letter(a-z)");
}
return ("");
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

An example of a technological innovation that increased the country’s natural resource base is.
Answers
The oil drill is an illustration of a technological advancement that enhanced the nation's natural resource base.
What does the term "technology innovation" mean?A new or enhanced product or procedure with considerably better technological features is referred to as a technological innovation. New products (product innovations) or processes (process innovations) that have been commercialized constitute technologically implemented product innovations.An expanded definition of innovation is technological innovation. Although innovation is a fairly well-defined notion, many people—especially those in the academic and corporate worlds—understand it to mean different things. Technological breakthroughs including wind turbines, photovoltaic cells, concentrated solar power, geothermal energy, ocean wave power, and many other recent innovations are included in the innovations. Innovation in technology benefits society. By bringing new, better products and services to the populace, it raises productivity and raises the level of living for everyone. Innovation's advantages sometimes take time to manifest. They frequently affect the entire population in a wide sense.To learn more about technological innovation, refer to:
https://brainly.com/question/19969274
#SPJ4
Which of the following is something that an Information Technology (IT) professional would do?
Collect and utilize data
Create and improve software
Manage grades and enrollments
Build and repair computers
Answers
Answer:
Probably the last one, build and repair computers.
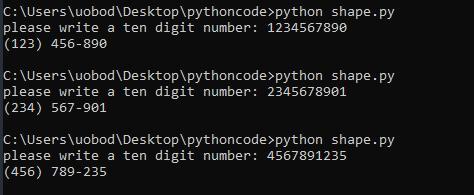
Write a program that takes a 10-digit phone number and adds a hyphen in the correct location. Using an input field for the user to enter the information. Also, use a string for instructions on how to enter the phone in the input field.
Answers
The python program will request for a ten digit number from the user and formulate a real phone number from it.
How to write a python program to form a real phone number?The program is written in python.
Therefore,
x = input("please write a ten digit number: ")
if len(x) == 10:
a = f"({x[0:3]})"
b = x[3:6]
c = x[7:]
print(a + " " + b + "-" + c)
Code explanation:The variable x is used to store the user's input.If the length of x is equals to 10, then we get the first three terms in bracket, the second three terms and the last 4 terms.Finally, we use delimiters to join the variables as required and print it out.learn more on python here: brainly.com/question/13462052
#SPJ1


In the cases of int, byte, long, short (In Java) Can you give the heirachy in ascending order?
Answers
Answer:
Byte Short Int Long
Explanation:
Byte's 8 bit, short's 16, int's 32, and long's 65.
3.2.3 What major al able to do? 3.2.4 What major advantage would Printer X have for Tembi who want documents printed? 3.3 If Tembi decides not to purchase new computers, but to replace her printers, what software will she need to install to ensure that the new printers work with her existing computers? 3.4 Tembi thinks she needs a new printer in her office because her present laser printer prints pages with faded edges. You don't think the printer is broken. Explain to her what the problem could be and how she could probably fix it. 4. If Tembi buys new computers, they will need to be linked to the network at the DVD shop. 4.1 What important component will the new computers need to have to be able to link to the existing network? 4.2 List three reasons that the computers need to be linked to the network for the business to operate optimally. 5. Tembi has seen an advertisement for notebook computers that seem very affordable. Name two reasons why notebooks would not be suitable for use in the DVD store. 6. Convergence of technology means that the customers would like to be able to view which movies are available for hire using their smartphones. 6.1 Explain the term convergence of technology. 6.2 Provide another example of technology convergence that's obvious today. 6.3 Name two ways in which a smartphone differs from a normal cellphone. 3 (1) (2) (1) (3) (2) (1) (1) (2) Total: (25)
Answers
Answer:
she or he will use handouts
How would PCORI methods be used for predictive analysis?
Applying to previous trials or other research data to produce personalized results
Answers
PCORI (Patient-Centered Outcomes Research Institute) methods can be used for predictive analysis by leveraging patient-centered data from previous trials or other research studies to generate personalized predictions for individual patients.
This can be achieved through the use of machine learning algorithms that analyze a variety of patient data such as demographics, clinical history, genetic information, and other relevant factors to predict patient outcomes. By incorporating patient preferences and values into the analysis, PCORI methods can help to produce personalized treatment plans that are tailored to each patient's unique needs and circumstances. This approach can improve the effectiveness of medical interventions and lead to better health outcomes for patients.
Find out more about PCORI (Patient-Centered Outcomes Research Institute)
brainly.com/question/31116844
#SPJ4
In which of the following do the bits work opposite of how bits in a subnet work?
Answers
In a subnet mask, the bits indicate the network portion and the host portion of an IP address. However, in a wildcard mask, the bits indicate which parts of the address should be ignored. Therefore, the bits in a wildcard mask work opposite of how bits in a subnet mask work.
In a subnet mask, the bits are used to divide the IP address into network and host portions. The network portion identifies the network to which the device belongs, while the host portion identifies the specific device on that network. The subnet mask is used by network devices to determine which part of an IP address corresponds to the network portion and which part corresponds to the host portion.
For example, if the subnet mask is 255.255.255.0, the first three octets (or 24 bits) of an IP address are used for the network portion, and the last octet (or 8 bits) is used for the host portion. This means that all devices on the same network will have the same first three octets, but different last octets. In contrast, a wildcard mask is used in access control lists (ACLs) to indicate which parts of an IP address should be ignored when matching traffic. Instead of indicating the network and host portions of an IP address, the bits in a wildcard mask indicate which parts of the address should be ignored.
To know more about IP address visit :
https://brainly.com/question/31026862
#SPJ11
1. Separate valid and invalid variables:
1. CSL
1. Age
2. Mark-sheet
3. Tel $
4. CLS
5. Simple Interest
6. SEE
1.545Newton
2. Stop5for
1. Give
2 $shopping
3. United
Answers
Firstly we explain the variable and the declaration rule for the variable and further separating the valid and invalid variables.
Whenever a user is given a question, variables are data values that can vary. for example age, CSL, etc.It may alter and during the execution of the program.It's a storage space for memories.It has a name that corresponds to the location.Data is stored in the memory location.The rule for variable declaration:
The names of your variables should be based on the phrases used in the subject area, and they should reflect the variable's function.By removing spaces between the words, you can make variable names. Each word in the name should be capitalized, including prepositions and pronouns that are one letter long.An underscore should never be used to start a variable name.Single-character variable names should be avoided. For loop counters, only short variable names are permitted.After the state that equals the "true" value, name variables that describe binary states ("true" or "false").The valid variable is:
CSL, Age,CLS,SEE,Stop5for,Give, $shopping, and United.
The invalid variable is:
Mark-sheet, Tel $, Simple Interest, and 545Newton.
Learn more:
brainly.com/question/2684763
The admission booth at the show requires each person to enter their age. Then the following program executes (See image.): When age = 16, what action would the program execute?
A. print “16”
B. print “Student price is $8.”
C. print “14”
D. print “Student price is $14.”

Answers
the data represented by numeric whole-number values, either positive or negative, that do not have decimal points
A. Boolean
B. string
C. Float
D. integer
What is another name for repetition in programming?
A. duplication
B. replication
C. redundancy
D. iteration
All of the following are types of errors in a computer program EXCEPT
A. syntax
B. parameter
C. semantic
D. logic
17.
What is one way that programmers insert explanatory statements in their code?
A. for loops
B. compiling code
C. use comments
D. create variables
18.
Why is readable code important? Choose all that apply.
A. It is more fun to write.
B. It makes the purpose and flow of a program easier to understand and follow.
C. Anyone needing to work with the code in the future will have an easier time.
D. It will save time when it is time to update the program. (MAYBE D AS WELL) if u are allowed to select more than 2
19.
All of the following are true about debugging except
A. debugging is not a necessary process
B. it is a process of identifying and eliminating errors in a software program
C. it is essential to produce high-quality programs
D. eliminating bugs is an important part of the program development cycle
20.
The type of conditional statement that tests if a condition is true or false
A. if
B. not
C. or
D. and
24.
Which best describes a computer bug?
A. a piece of computer hardware that is out of date or has a newer version
B. a piece of computer software containing defects that prevent a program from running properly
C. a piece of computer hardware that is being used improperly
D. a piece of computer software that is out of date or has a newer version
25.
Which set of variables will make code easier to understand?
A. a, b, c
B. sum, price, count
C. xii, xix, xxi
D. x, y, z
23.
An argument is different from a parameter in that an argument
A. refers to a piece of data to be supplied.
B. is a placeholder for a constant value.
C. is the data passed into a parameter.
D. is always variable.
Answer:
B. print "Student price $8."
Explanation:
B
Which of the following tiny computer apps is designed to be useful but could cause more harm than good?
BIOS
Macro
OS
Sys file
Answers
The following tiny computer app that is designed to be useful but could cause more harm than good is Sys file
What is a Sys file?This refers to the system file that is in operating systems and contains settings and variables that can make changes to the operating system.
Hence, we can see that if a user decides to tamper with the sys file on their operating system- either Microsoft DOS or Windows Operating Systems, this can lead to irreparable damages.
Read more about sys file here:
https://brainly.com/question/14364696
#SPJ1
A class can contain many methods, and each method can be called many of times Group of answer choices True False
Answers
Answer:
True, a class can contain many methods, and each method can be called an infinite amount of times.
Which aspect of a certificate makes it a reliable and useful mechanism for proving the identity of a person, system, or service on the internet
Answers
The aspect of a certificate that makes it a reliable and useful mechanism for proving the identity of a person, system, or service on the internet is the digital signature.
A digital signature is a mathematical scheme used to verify the authenticity and integrity of a message, document, or software. It is generated using a private key that is owned only by the entity being authenticated and can be verified using a public key that is widely available.
When a certificate is issued, it includes a digital signature from the certificate authority (CA) that issued it. This signature ensures that the certificate has not been tampered with and that it is still valid. When a user receives a certificate, they can verify the digital signature to ensure that the certificate was issued by a trusted CA and has not been modified since it was issued.
By relying on digital signatures, certificates provide a secure and reliable way to prove the identity of a person, system, or service on the internet. This is important for a wide range of applications, including secure web browsing, online banking, and e-commerce. Certificates are also used in other contexts, such as secure email and document signing, where the authenticity and integrity of the message or document are critical.
Learn more about mechanism here:
https://brainly.com/question/31655553
#SPJ11
Prompt
What is a column?
Answers
Answer:
A column is a vertical group of values within a table. It contains values from a single field in multiple rows. ...
A column is a vertical group of values within a table. It contains values from a single field in multiple rows.
Why prompt is used?Since we can choose only one of the prompts, let's work with prompt A. We can answer it in the following manner edgar Allan Poe believed that a good short story must have a single, unifying effect. He did apply that concept to his own short stories. Let's briefly analyze "The Fall of the House of Usher."
In the story, every element contributes to the story's effect: the setting, the characters, the dialogue, the word choice and the mood, among others. From the beginning, the narrator describes an "oppressive" weather. He proceeds to let us know that his friend Usher looks sick and strange. The house where Usher lives is also quite eerie. And to top it all, Usher's sister, who was buried alive, has returned for revenge.
Poe believed a good short story should possess a single, unifying effect, and that everything in the story should contribute to that effect. He achieves that in his short stories, where every element (characters, setting, imagery, word choice, etc.) contributes to the feeling of tension, anxiety, even horror.
Therefore, A column is a vertical group of values within a table. It contains values from a single field in multiple rows.
Learn more about element on:
https://brainly.com/question/14347616
#SPJ2
a hierarchical hyperlink structure resembles conventional paper documents in that the reader begins on the first page and clicks the next button to move to the next page in a serial fashion. question 21 options: true false
Answers
The statement is true, because, a hierarchical hyperlink structure resembles conventional paper documents in that the reader begins on the first page and clicks the Next button to move to the next page in a serial fashion.
This allows readers to navigate through the website in a logical and organized manner.
The hierarchical structure provides an intuitive way to navigate through a website, and it is especially important for larger websites with many pages and a lot of content. This structure also helps websites to be more organized and makes it easier for users to find the content they are looking for. Additionally, it makes the website easier to maintain, as the structure can be modified in a few simple steps.
Learn more about hierarchical structure:
https://brainly.com/question/16475842
#SPJ4
Need the answer rn!!!!

Answers
Answer:
what language is this? english or no
Explanation: