To define a mail server for the domain, a(n) ____ entry must be made in the DNS database file for forward resolution
Answers
To define a mail server for the domain, a(n) "MX" entry must be made in the DNS database file for forward resolution. an "MX" entry is required in the DNS database file.
Open the DNS database file for the domain that you want to define a mail server for. Locate the section for forward resolution, which is usually indicated by a "forward" or "A" record. Add a new line to the file and enter the "MX" entry, followed by the desired priority value and the hostname of the mail server.
The priority value determines the order in which mail servers are tried when sending emails. Save the changes to the DNS database file. Restart the DNS server or reload the DNS configuration to apply the changes.
To know more about DNS database visit:
https://brainly.com/question/33561648
#SPJ11
Related Questions
Select the correct answers.
Which are the benefits of leveraging web technologies?
processing of large amounts of data
more manpower
better marketing and customer service
increased production costs
difficulty in handling customer complaints

Answers
Answer:
Explanation:
Select the correct answers.
Which are the benefits of leveraging web technologies?
1) Processing of large amounts of data
2) Better marketing and customer service
what term does don norman use to describe the model that explains the operation of the system in context so that it weaves together all of the essential components, providing a framework, a context, and reasons for understanding?
Answers
The term that Don Norman used to describe the model was conceptual model
For better understanding let us explain what conceptual model means
Conceptual model is simply known as a diagram of a given (proposed) causal linkages that is amidst a set of concepts or ideas. It is usually linked to a specific public health issues.This models are said to be different from other theories because they are not concerned with global behavior, but with specific types of behavior in the right or main contexts. Due to its component being woven together as one, it is very easy to understand what aspect you want.From the above, we can therefore say that conceptual model acts as linkages and due to its component being woven together as one, it is very easy to understand what aspect you want.
Learn more about Conceptual model from
https://brainly.com/question/17504631
The Glasses class represents a pair of eyeglasses. One of its instance variables is a Prescription object called script. The Prescription object has instance variables that stores the prescription for the left and right eye.
Which of the following constructors for the Glasses class correctly sets the script instance variable correctly? Assume any method calls are valid.
public Glasses(Prescription thePrescription){ script = new Prescription(thePrescription.getLeft(),thePrescription.getRight());}
Answers
Using the knowledge in computational language in python it is possible to write a code that class represents a pair of eyeglasses. One of its instance variables is a Prescription object called script.
Writting the code:oOfPrescriptions = 0
TotalCost = 0
def _init_(self, person, mcpNo, drug, refill, doctor, dCost, units):
self.pName = person
self.mcp = mcpNo
self.drugName = drug
self.noOfRefillsLeft = refill
self.dName = doctor
self.dUnitCost = dCost
self.noOfUnits = units
Prescription.NoOfPrescriptions += 1;
Prescription.TotalCost += self.computeCost()
def getPersonName(self):
return self.pName
def getNoOfRefillsLeft(self):
return self.noOfRefillsLeft
def refillThePrescription(self):
if self.noOfRefillsLeft < 1:
print("Sorry, there are no refills left.\n")
else:
self.noOfRefillsLeft -= 1
print("Refills left: %d\n" %self.noOfRefillsLeft)
def computeCost(self):
DISP_FEE = 0.15 * self.dUnitCost * self.noOfUnits
cost = self.dUnitCost * self.noOfUnits + DISP_FEE
return cost
def _str_(self):
return "Person's Name: " + self.pName + '\nMCP#: ' + self.mcp + "\nDoctor's Name: " + self.dName + "\nDrug: " + self.drugName + "\nRefills Left: %d"%self.noOfRefillsLeft + "\nTotal Bill: $%.2f\n"%(float(int(self.computeCost()*100))/100)
def main():
p1 = Prescription("Rolly Poll", "123 456 789", "Drug1", 3, "Dr. Peter", 2.5, 21)
p2 = Prescription("Henny Penny", "234 567 890", "Drug2", 1, "Dr. Pick", 1.95, 30)
print(p1)
print(p2)
p2.refillThePrescription()
p2.refillThePrescription()
print(p2)
print("Person's Name:", p1.getPersonName())
print("Number of refills left: %d"%p1.getNoOfRefillsLeft())
print()
print("Total number of prescription objects: %d"%p2.NoOfPrescriptions)
rint("Total Cost of all Prescripton Objects: $%.2f\n"%p2.TotalCost)
main()
See more about python at brainly.com/question/18502436
#SPJ1

Summarize these two up-and-coming leadership positions in digital media: digital media supervisor and chief digital officer (CDO). What does each job entail? What is one way they are different? What is one way they are similar? Which one sounds more appealing to you, and why?
Answers
Answer:
The big differences in the CIO and the Chief Digital Officer is this responsibility for turning IT into a value creator, being a business to the extent of actually having a P&L, which is something that the CIO typically doesn’t have in most organizations.
And so we also see the CDO as something that is really leading digital business from the front in a way that most CIOs aren’t. Most CIOs are not trying to think of new markets, new channels, new business models that the organisation should be getting and making that a top priority. And that’s pretty much all the Chief Digital Officer thinks about is how to take existing assets, existing information, existing knowledge and making a business out of that creating products and services and entering new markets.
I think that the CIO, however, is used to operating much larger operations, so I think what remains to be seen we’re not seeing Chief Digital Officers have as much operational experience, or even necessarily seem to require it. Although I think the really successful digital businesses will be able to scale up their organizations really well, they’re going to have Chief Digital Officers that are good at that, we’re not seeing operational jobs as job number one, quite the same way as we’re seeing it in traditional CIOs.
In terms of really any other big differences, we see that Chief Digital Officers are very multidisciplinary, so they have a lot of different experiences, and there’re very comfortable in talking with marketing and sales in their language. They’re very good at talking to the product teams in their language and operations in their language, and executives and so on. And not to the same degree that we see the CIOs that don’t really talk the language of business, and they talk the language of the IT department but that tends to be it.
Explanation:
Digital Media Supervisor ( CIO )
Chief Digital Officer ( CDO )
A bubble starts by comparing the first item in the list to all the remaining items, and swaps where the first item is ____ a later item.
greater than
less than
equal to
Answers
Answer:
greater than
i think
A bubble starts by comparing the first item in the list to all the remaining items, and swaps where the first item is greater than a later item. Thus, option A is correct.
What happens in a binary sort?Such a binary sort, in which we keep comparing the pairs of items, swapping them if they are not in order, until the smallest item bubble to the top of the list, therefore creating a sorted list which is known as bubble sort.
A Binary search tree (BST) is a type of data structure used in computer science that consists of nodes arranged in a hierarchical structure. Each node in a BST contains a value, and the left child node contains a value that is smaller than its parent, while the right child node contains a value that is larger than its parent.
This makes BSTs ordered, as the elements are arranged in a specific order. They are also sometimes called sorted binary trees, as the values are sorted in a specific order. BSTs are commonly used in computer algorithms, as they allow for efficient searching, insertion, and deletion of elements.
Thus, option A is correct.
Learn more about algorithms on:
https://brainly.com/question/22984934
#SPJ3
given a 4096b sector, 3,000rpm, 4 ms average seek time, 700mb/s transfer rate, and 0.2ms controller overhead, find the average read time in ms for one sector. round result to 1 decimal place.
Answers
The average read time for one sector is approximately 19.9 ms, rounded to 1 decimal place.
First, let's calculate the transfer time. We have a transfer rate of 700mb/s, which means we can transfer 700,000,000 bits in one second. To transfer 4096 bytes (or 32,768 bits), it would take:
32,768 bits / 700,000,000 bits per second = 0.0000468 seconds
We need to convert this to milliseconds, so we multiply by 1000:
0.0000468 seconds * 1000 = 0.0468 ms
Next, let's calculate the seek time. We have an average seek time of 4ms, which means it takes on average 4ms for the disk to locate the sector we want to read.
Finally, we need to take into account the controller overhead, which is 0.2ms.
Adding all these times together, we get:
0.0468 ms (transfer time) + 4 ms (seek time) + 0.2 ms (controller overhead) = 4.2468 ms
Rounding this to one decimal place, we get an average read time of 4.2 ms for one sector.
To find the average read time for one sector, we need to consider the seek time, rotational latency, transfer time, and controller overhead.
1. Seek Time: Given as 4 ms.
2. Rotational Latency: Since the disk is spinning at 3,000 RPM, the time for a full rotation is (60 seconds/3,000) = 0.02 seconds or 20 ms. The average rotational latency is half of this value, which is 10 ms.
3. Transfer Time: With a transfer rate of 700 MB/s, we can find the time to transfer 4096 bytes (4 KB) by first converting the transfer rate to KB/ms: (700 * 1000) KB/s / 1000 = 0.7 KB/ms. Then, Transfer Time = (4 KB / 0.7 KB/ms) ≈ 5.7 ms.
4. Controller Overhead: Given as 0.2 ms. Now, sum up all these times to find the average read time for one sector:
Average Read Time = Seek Time + Rotational Latency + Transfer Time + Controller Overhead
= 4 ms + 10 ms + 5.7 ms + 0.2 ms ≈ 19.9 ms
To know more about transfer time visit :-
https://brainly.com/question/15443202
#SPJ11
Read the sentence. Piles of discarded trash litter the cobblestones of the quaint brick alley. Which image best shows a visualization of this sentence? A cobblestone alley with garbage on the ground. A cobblestone alley with several garbage cans. A cobblestone alley with weeds growing in the cracks. A clean cobblestone alley.
Answers
Answer:
C
Explanation:
JUST DID IT
Answer:
c
Explanation:
How large does a telsa coil need to be to transmit wireless electricity
Answers
The size of the largest operational Tesla Coil is measured to be 38ft or 12 meters. It transmits about 138kw of electricity.
What is a Tesla Coil?Nikola Tesla invented the Tesla coil, an electrical resonant transformer circuit, in 1891. It is used to generate high-voltage, low-current, high-frequency alternating current.
During his efforts to construct a "wireless" lighting system with gas discharge light bulbs that would shine in an oscillating electric field generated by a high voltage, high-frequency power source, Tesla devised the Tesla coil.
Tesla coils provide various health risks owing to high voltage radio frequency emission, including skin burns and nervous system and heart damage.
Learn more about Tesla Coil:
https://brainly.com/question/7295601
#SPJ1
Which of the following is a key benefit of studying theoretical perspectives on management?.
Answers
Theoretical perspectives provide knowledge of management approaches that help students to understand the evolution of management thoughts and practices. Moreover, studying theoretical perspectives enables students to develop their analytical thinking, gain problem-solving skills and learn how to apply theoretical concepts in the practical management environment.
The key benefit of studying theoretical perspectives on management is that it helps the students understand how management practices and thoughts evolved over time. Studying theoretical perspectives allows students to develop critical and analytical thinking skills, which they can apply in practical management settings. Additionally, it enables students to learn about different management approaches and gain leadership skills. It also helps them to identify the potential issues that may arise in an organization and design appropriate strategies to mitigate them. Studying theoretical perspectives can also provide students with a comprehensive understanding of the different management theories, enabling them to integrate these theories into practice.
Studying theoretical perspectives on management is a critical aspect of gaining knowledge and developing problem-solving skills in management. It helps students to understand the evolution of management thoughts and practices and provides them with a solid foundation to analyze and solve problems in a practical management setting.
To know more about leadership visit:
https://brainly.com/question/28487636
#SPJ11
john needs to identify public key systems that generate different, random public keys for each session and, even if a key gets stolen, should not reveal more than one message. which public key system should john suggest?
Answers
A public key system which John should suggest is perfect forward secrecy.
What is an encryption?An encryption can be defined as a form of cryptography and it typically involves the process of converting or encoding information in plain text into a code, known as a ciphertext. Generally speaking, an information or data that has been encrypted it can only be accessed and deciphered by an authorized user.
In Computer programming, some examples of encryption algorithms include the following:
3DESAESRC4RC5RSAWhat is perfect forward secrecy?Perfect forward secrecy (PFS) is also referred to as forward secrecy (FS) and it can be defined as an encryption system that is designed and developed to frequently and automatically change the public keys which were used to encrypt and decrypt information.
In this context, we can reasonably infer and logically deduce that a public key system which John should suggest is perfect forward secrecy.
Read more on encryption here: https://brainly.com/question/9979590
#SPJ1
What type of activity describes the act of placing an ad in the yellow pages of a telephone book? 1. Client appreciation activity 2. Booking activity 3. Marketing activity 4. Sales activity
Answers
The type of activity that describes the act of placing an ad in the yellow pages of a telephone book is a marketing activity.
Marketing activities are designed to promote a product or service to potential customers with the goal of generating sales. By placing an ad in the yellow pages, a business is increasing its visibility and making it easier for potential customers to find them when searching for a particular product or service. This type of marketing activity is particularly useful for businesses that rely on local customers, such as plumbers, electricians, and restaurants. While placing an ad in the yellow pages is not the only marketing activity a business should engage in, it can be an effective way to reach a large audience without breaking the bank. By creating a clear and compelling ad, businesses can increase the likelihood that potential customers will choose them over their competitors, resulting in increased sales and revenue.
Learn more about Marketing here:
https://brainly.com/question/17328633
#SPJ11
What is a threshold?
Answers
Answer:
2 definitions for threshold:
(1) The point at which a signal (voltage, current, etc.) is perceived as valid.
(2) (Threshold) The code name for Windows 10.
1, It is a level of which someone must exceed in order to reach/achieve something.
2, It is a location or property.
Tracy always starts facing which direction?
Answers
Answer:
tracy starts facing east
Explanation:
The time Yanni runs to catch Tracy is 20 minutes.
We are given that;
Speed of tracy= 1mile in 10min
Now,
We need to find the distance that Tracy and Yanni have traveled when they meet.
Let x be the time (in minutes) that Yanni runs, then Tracy runs for x + 20 minutes.
Since their speeds are given in miles per minute, we can write the following equations:
Distance traveled by Tracy = 1/10 * (x + 20)
Distance traveled by Yanni = 1/5 * x
They meet when their distances are equal, so we can set the equations equal and solve for x:
1/10 * (x + 20) = 1/5 * x
Multiply both sides by 10 to clear the fractions: x + 20 = 2x
Subtract x from both sides: 20 = x
Therefore, by algebra the answer will be 20 minutes.
More about the Algebra link is given below.
brainly.com/question/953809
#SPJ6
The complete question is;
Tracy is running a trail in Hanna park she can run 1 mile in 10 minutes Yanni is running the same trail as Tracy Johnny can run a mile in five minutes but starts running 20 minutes after Tracy started on the trail if they started the trail from the same point how long will it take Yanni to catch Tracy
What is the process called when programmers look for and fix errors in code? Analysis Debug Document Error check
Answers
Answer:
debug status
Explanation:
Write a code in python that guesses a hardcoded answer and keeps on asking the user until the user gets the answer correct. The cmputer should be telling the user if the number they are guessing is too low or too high.
Answers
import random
#You can change the range.
answer = random.randint(1,1000)
counter = 0
while(True):
guess = int(input("Make a guess: "))
message = "Too high!" if guess>answer else "Too low!" if guess<answer else "You won!"
print(message)
if(message=="You won!"):
print("It took",counter,"times.")
break
else:
counter+=1

What is the result when you run the following program?
print(2 + 7)
print("3+1")
9
Ost
3+1
an error statement
O
2 +7
4
9
O A
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
If you run the following program,
print(2 + 7)
print("3+1")
then, you can get the following result respectively against each print statement.
9
3+1
because when you print 2+7 without quotation, it will add the integer digit and print the result of adding 2 and 7.
And, when you run ("3+1") in the double quotation, the program will treat it as a string because of the enclosed double quotation (" ");
Explain three applications of computers and information systems in the daily life of a college student.
Answers
Answer:
Drawing tools, spreadsheets, Audio, Video lectures, and PowerPoint presentations, etc.
Computer and information system helps a college student in storing and maintaining data, making their projects and research paper, also to search for information.
What is a computer?A computer is an electronic device that performs a variety of tasks. This uses a binary system, which contains just two variables: 0 and 1. These two binary numbers serve as the foundation for all encoding and decoding operations.
On a computer, a variety of algorithms can be used. If a hard drive is malfunctioning, it is simple to retrieve the content or information from that drive.
A college student can store and preserve data like study materials or previously done projects, create projects and research papers, as well as conduct information searches on any topic that they want to gain information on, thanks to computers and information systems.
Learn more about computers here:
https://brainly.com/question/1394311
#SPJ2
Artificial neural networks can learn and perform tasks such as_____. a. generating stories b. filtering spam e-mail c. composing music d. designing software
Answers
Artificial neural networks are computational models inspired by the structure and function of the human brain. They are capable of learning and performing a wide range of tasks. Here are some examples of tasks that artificial neural networks can learn and perform:
1. Generating stories: Artificial neural networks can be trained to generate creative and coherent stories. By learning patterns and structures from a dataset of existing stories, they can generate new stories with similar themes and styles.
2. Filtering spam e-mail: Artificial neural networks can be used to classify incoming e-mails as either spam or legitimate. By training on a large dataset of known spam and non-spam e-mails, neural networks can learn to recognize patterns and characteristics that distinguish spam from legitimate messages.
3. Composing music: Neural networks can be trained to compose music by learning from a dataset of existing compositions. By analyzing the patterns, rhythms, and harmonies in the dataset, the neural network can generate new music that follows similar patterns and styles.
4. Designing software: Artificial neural networks can also be used to design software systems. They can learn from existing software codebases and generate new code that fulfills specific requirements. This can help automate certain aspects of software development and assist programmers in creating more efficient and effective software.
These are just a few examples of the tasks that artificial neural networks can learn and perform. Their ability to learn and adapt from data makes them versatile tools that can be applied to various fields, including language processing, image recognition, and decision-making.
To know more about Artificial neural networks, visit:
https://brainly.com/question/19537503
#SPJ11
Why are user manuals important? Select all that apply.
User manuals contain text and images to describe how to use the program features.
User manuals provide print versions of forum discussions.
User manuals explain the commands and syntax of programming languages.
User manuals often include chapter on problems and their resolutions.
Answers
Answer:
I. User manuals contain text and images to describe how to use the program features.
II. User manuals explain the commands and syntax of programming languages.
III. User manuals often include chapter on problems and their resolutions.
Explanation:
A user manual can be defined as a clear, detailed and an informative guide drafted by the manufacturer (producer) of a product or service, which is to be given to a customer (end user) so as to help them know and understand how to use the product or service properly.
User manuals are important because they contain the following necessary informations;
I. User manuals contain text and images to describe how to use the program features.
II. User manuals explain the commands and syntax of programming languages.
III. User manuals often include chapter on problems and their resolutions.
Additionally, a user manual contains information on the safety precautions that are to be taken by the end user while using a product or service.
Answer:
A C D
Explanation:
Because yes
python. create a program that asks the user to input their first name and their favorite number. Then the program should output the user's name and favorite number in the following format: "[first names]'s favorite number is [number]!"
Answers
name = input("What is you name?")
fav_number = input("What is you favorite number?")
print(name + " your favorite number is " + fav_number + "!")
17. Electrospinning is a broadly used technology for electrostatic fiber formation which utilizes electrical forces to produce polymer fibers with diameters ranging from 2 nm to several micrometers using polymer solutions of both natural and synthetic polymers. Write down 5 different factors that affect the fibers in this fabrication technique. (5p) 18. Write down the definition of a hydrogel and list 4 different biological function of it. (Sp) 19. A 2.0-m-long steel rod has a cross-sectional area of 0.30cm³. The rod is a part of a vertical support that holds a heavy 550-kg platform that hangs attached to the rod's lower end. Ignoring the weight of the rod, what is the tensile stress in the rod and the elongation of the rod under the stress? (Young's modulus for steel is 2.0×10"Pa). (15p)
Answers
The elongation of the rod under stress is 0.09 m or 9 cm. Five factors that affect the fibers in electrospinning fabrication technique.
1. Solution properties: The solution concentration, viscosity, surface tension, and conductivity are examples of solution properties that influence fiber morphology.
2. Parameters of electrospinning: Voltage, flow rate, distance from the needle to the collector, and needle gauge are examples of parameters that influence the fiber diameter and morphology.
3. Physicochemical properties of the polymer: The intrinsic properties of the polymer chain, such as molecular weight, crystallinity, and orientation, influence the morphology and properties of the fibers.
4. Ambient conditions: Humidity, temperature, and air flow rate can all influence fiber morphology.
5. Post-treatment: Electrospun fibers can be subjected to post-treatments such as annealing, solvent treatment, and crosslinking, which can influence their mechanical, physical, and chemical properties.Answer to question 18:A hydrogel is a soft, jelly-like material that is primarily composed of water and a polymer network. Hydrogels have a range of biological functions due to their properties such as mechanical and biocompatible. Some of the biological functions of hydrogel are mentioned below:
1. Drug delivery: Hydrogels are widely utilized in drug delivery systems, particularly for the sustained release of drugs over time.
2. Tissue engineering: Hydrogels are frequently used as biomaterials in tissue engineering due to their similarities to the extracellular matrix (ECM).
3. Wound healing: Hydrogels are employed in wound healing due to their potential to promote tissue regeneration and repair.
4. Biosensing: Hydrogels are utilized in the production of biosensors that are capable of detecting biological and chemical compounds. Answer to question 19:Given,Magnitude of the force acting on the rod, F = 550 kg × 9.8 m/s² = 5390 NArea of the cross-section of the rod, A = 0.30 cm³ = 0.3 × 10^-6 m³Length of the rod, L = 2.0 mYoung's modulus of steel, Y = 2.0 × 10¹¹ N/m²The tensile stress in the rod is given by the relation;Stress = Force / Areaσ = F / Aσ = 5390 N / 0.3 × 10^-6 m²σ = 1.80 × 10^10 N/m²The elongation of the rod under stress is given by the relation;Strain = Stress / Young's modulusε = σ / Yε = 1.80 × 10¹⁰ N/m² / 2.0 × 10¹¹ N/m²ε = 0.09. The elongation of the rod under stress is 0.09 m or 9 cm.
Learn more about morphology :
https://brainly.com/question/1378929
#SPJ11
Prove that a tree with n, n>=2, vertices has at least two
leaves.
Answers
A tree with n, n>=2, vertices always has at least two leaves.
Can we prove that a tree with n vertices, where n is greater than or equal to 2, always has at least two leaves?To prove that a tree with n vertices has at least two leaves, we can use induction.
In a tree, a leaf is defined as a vertex with degree 1, meaning it has only one adjacent vertex.
For the base case, when n = 2, the tree consists of two vertices connected by a single edge. In this case, both vertices are leaves.
Assuming the statement holds true for a tree with k vertices, we need to show that it also holds true for a tree with k+1 vertices.
When we add one more vertex to the tree, it must be connected to an existing vertex. This new vertex has degree 1 and becomes a leaf. Additionally, at least one of the existing leaves remains, resulting in the tree having at least two leaves.
By the principle of mathematical induction, we have proven that a tree with n vertices, where n is greater than or equal to 2, always has at least two leaves.
Trees and mathematical induction to gain a deeper understanding of their properties and applications in various fields.
Learn more about tree
brainly.com/question/29294762
#SPJ11
which of the listed factors are important for local seo? choose three answers. localized site content total number of backlinks from trusted websites mentions of your business name, address, and phone number links from local websites follow/nofollow backlink property
Answers
The three important factors for local SEO are:
1. Localized site content: It is important to have content on your website that is relevant to the local area you are targeting. This includes using local keywords, mentioning local landmarks or attractions, and providing information about your business's location and services in the local area.
2. Total number of backlinks from trusted websites: Backlinks are links from other websites that direct users to your website. Having a high number of backlinks from trusted and authoritative websites can greatly improve your local SEO. Search engines consider backlinks as a vote of confidence for your website's credibility and relevance.
3. Mentions of your business name, address, and phone number: Consistently mentioning your business's name, address, and phone number (NAP) across various online directories, review sites, and social media platforms is crucial for local SEO.
To know more about SEO visit:
https://brainly.com/question/29582565
#SPJ11
Document that tells important facts about the project is called
Answers
The document that tells important facts about the project is known as Project Charter.A project charter is an essential document that gives a high-level overview of the project's objectives, scope, stakeholders, and deliverables.
It is used to give the team a clear understanding of the project's purpose and goals, as well as their roles and responsibilities in the project's successful completion. The document includes all the critical components that affect the project's success or failure, such as risks, constraints, assumptions, and success criteria.The project charter is also used as a reference throughout the project's life cycle to ensure that the project remains aligned with its objectives and goals.
The project manager creates the project charter and receives approval from the project sponsor before the project begins. This document is a crucial element in defining the project and ensuring that it is delivered on time, within budget, and according to quality standards.In conclusion, the project charter is a comprehensive document that outlines the project's key details, including its objectives, scope, stakeholders, and deliverables.
To know more about stakeholders visit:
https://brainly.com/question/30241824
#SPJ11
please help
match the features with the software
Word Processor, Spreadsheet, Database
- addiction of images, drawings, tables and graphics to text
- centralized data management
- data security
- digital version accounting sheets
- supports multiple users for adding data simultaneously
- visual representation of data
- digital version of a typewriter
Answers
Answer:
word processor- addition of images, drawing tables, and graphics to texts and digital version of a typewriter. spreadsheet- digital version of accounting sheets and visual representation of data. database- centralized data management, data security, and supports multiple users for adding data simultaneously
Just switch the two I got wrong and you'll get the correct answers. :)
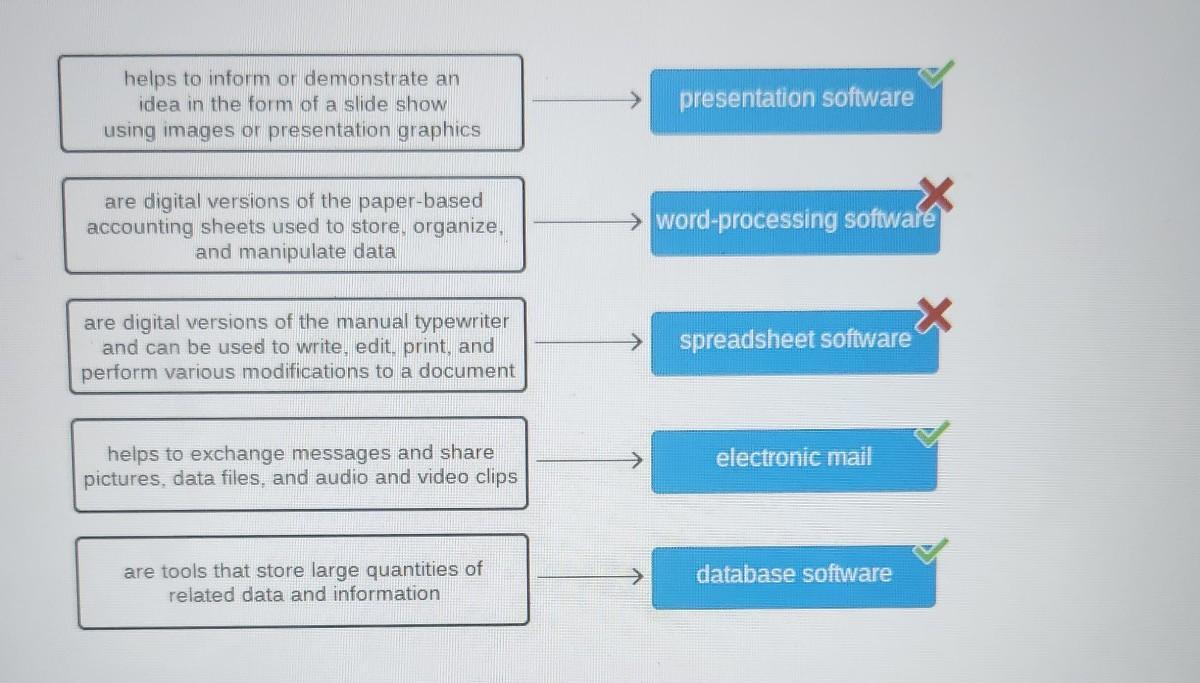
PLEASEEE HELPPP im gonna cry
What’s the name for the array of buttons that provides quick access to commonly used commands?
A.
menu bar
B.
toolbar
C.
ruler
D.
scroll bar
Answers
Your answer is:
B. toolbar
Answer:
B) Toolbar
_______________
Step into my world
Bittersweet love story about a girl
Shook me to the core
Voice like an angel, I've never heard before
Here in front of me
Shining so much brighter than I have ever seen
Life can be so mean
But when he goes, I know he doesn't leave
[Pre-Chorus 1: Charlie Gillespie & Madison Reyes]
The truth is finally breaking through
Two worlds collide when I'm with you
Our voices rise and soar so high
We come to life when we're
[Chorus: Charlie Gillespie & Madison Reyes]
In perfect harmony
Woah, woah
Perfect harmony
Woah, woah
Perfect harmony
[Verse 2: Charlie Gillespie, Madison Reyes, Charlie Gillespie & Madison Reyes]
You set me free
You and me together is more than chemistry
Love me as I am
I'll hold your music here inside my hands
[Pre-Chorus 2: Charlie Gillespie & Madison Reyes]
We say we're friends, we play pretend
You're more to me, we're everything
Our voices rise and soar so high
We come to life when we're
[Chorus: Charlie Gillespie & Madison Reyes]
In perfect harmony
Woah, woah
Perfect harmony
Woah, woah
Perfect harmony
[Bridge: Charlie Gillespie, Madison Reyes, Charlie Gillespie & Madison Reyes]
I feel your rhythm in my heart, yeah-yeah
You are my brightest, burning star, woah-woah
I never knew a love so real (So real)
We're heaven on earth, melody and words
When we are together we're
[Chorus: Charlie Gillespie & Madison Reyes]
In perfect harmony
Woah, woah
Perfect harmony
Woah, woah
[Outro: Charlie Gillespie, Madison Reyes, Charlie Gillespie & Madison Reyes]
We say we're friends
We play pretend
You're more to me
We create a perfect harmony
Answers
Answer:
THIS SONG IS FIRE AND WHEN IT HAPPENED IN THE SHOW, I FAINTED*
Explanation:
Julie and the Phantoms is my favorite thing in the world.
In order to generate a public and private key for use with SSH, what command line utility should you use?
Answers
To generate a public and private key for use with SSH, you should use the command line utility called "ssh-keygen".
SSH (Secure Shell) uses public-key cryptography to establish a secure connection between two computers. This involves generating a pair of keys: a public key and a private key. The public key is shared with the remote computer, while the private key is kept on the local computer.
1. Open a terminal or command prompt.
2. Type "ssh-keygen" and press Enter.
3. Follow the prompts to specify a file location for the keys, or use the default location by pressing Enter.
4. If desired, set a passphrase for added security, or leave it empty by pressing Enter.
5. The public and private keys will be generated and saved in the specified location.
By using the "ssh-keygen" command line utility, you can successfully generate a public and private key for use with SSH.
To know more about command prompt visit:
https://brainly.com/question/2555135
#SPJ11
Nora has shared a document with others, and she needs to be able to easily identify when others are modifying the
documents and where those modifications have been made.
Which feature should Nora use?
Password Protection
OneDrive storage
Track Changes
Protected View
Answers
Answer:
C, Track Changes
Explanation:
Answer:
C. Track Changes
Explanation:
hope this helps :)
the weekly question would you rather be the smartest but ugliest at your school or most handsome but not smart.
Answers
Answer:
lol I would be the most handsome but not smart
Explanation:
Answer:
Imao- i'd be the most handsome(cute) but not smart.
Explanation:
have a great weekend ( ̄▽ ̄)ノ