When turning uing reference point, which i NOT the correct procedure?
A. Check lane poition o you don’t have to cut acro multiple lane of traffic
B. Slow down only during your turn
C. Reference your turning point to mental ee the forward pivot point your car will follow
D. Search the area you’re moving your car into to ee if it i open or cloed
Answers
B. Slow down only during your turn.
Which i NOT the correct procedure?When turning using reference point, it is important to take the necessary safety measures to ensure the safety of yourself, other drivers, and pedestrians.Firstly, make sure to check your lane position and adjust to avoid cutting across multiple lanes of traffic. Secondly, begin to slow down as you approach your turn and remember to use the reference point to mentally see the forward pivot point your car will follow. Lastly, search the area you are moving your car into to make sure it is open or closed to traffic.This technique of using reference points while turning is known as "defensive driving". Defensive driving is a set of driving skills that allow you to anticipate potential hazards and take action to avoid them.This technique is important to maintain safety on the road and can be used in a variety of situations, such as turning and merging. By taking the necessary steps to check lane position, slow down, and survey the area you are moving your car into, you can practice defensive driving and remain safe on the roads.To learn more about technique of using reference points refer to:
https://brainly.com/question/26481752
#SPJ4
Related Questions
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
An artistic technique that creates the appearance of three dimensions on a flat surface.
Answers
Answer:
atmospheric perspective
in the industry, desktops are typically cloned and images are used on multiple pcs. explain how using the restore point utility can help with the rebuilding and testing of pcs.
Answers
With system restorations in place, you can test out various OS and software patches to see how well they work, and if something goes wrong, you can go back to the time the system was running without that patch loaded.
What is software ?Software is a set of instructions, information, or computer programs that are used to operate equipment and perform certain tasks.
Hardware, which is a term for a computer's external components, is the opposite of it.
In this usage, "software" refers to the running scripts, programs, and apps on a device.
It can be compared to the variable part of a computer, whereas the hardware is the part that will never change.
The two primary subcategories of software are application software and system software.
Applications are software components that perform functions or meet particular needs.
System software, which also serves as a platform for other software to run on, controls how a computer's hardware operates.
One of the other is software that provides programming tools.
Hence, With system restorations in place, you can test out various OS and software patches to see how well they work, and if something goes wrong, you can go back to the time the system was running without that patch loaded.
learn more about software click here:
https://brainly.com/question/28224061
#SPJ4
PLEASE HELP !!!!!!!!!!
An assignment my gaming and animations teacher gave me said to explain (insert game)’s objectives, operation, obstacles, and outcomes. I don’t know what an operation means here. Please help
Answers
Answer:
Operation means what does the game do? What is the purpose. If you press left arrow key what happens...etc. That is what operation is in "gaming" sense.
Hope i helped!
True or false: Big data is a collection of large, complex data sets, including structured and unstructured data, which cannot be analyzed using traditional database methods and tools. True false question. True False
Answers
The statement is true. Big data refers to the collection of large and complex data sets, which can include both structured and unstructured data.
These data sets are typically too large and complex to be processed and analyzed using traditional database methods and tools. Traditional databases are designed to handle structured data, which is data that is organized in a specific format, such as rows and columns. They are not well-suited for handling unstructured data, which can include things like text documents, images, videos, social media posts, and sensor data.
Unstructured data does not have a predefined format and can be more challenging to analyze using traditional database methods. Big data requires specialized tools and techniques to process and analyze the vast amounts of data. These tools can include distributed computing frameworks like Hadoop and Apache Spark, which allow for parallel processing of data across multiple servers.
Additionally, big data analytics platforms and algorithms are used to extract valuable insights and patterns from the data. In conclusion, big data is indeed a collection of large, complex data sets that often contain a mix of structured and unstructured data. Due to its size and complexity, traditional database methods and tools are not sufficient for analyzing big data, requiring specialized approaches and tools.
Learn more about database here: https://brainly.com/question/31449145
#SPJ11
You are required to write a program which will convert a date range consisting of two
dates formatted as DD-MM-YYYY into a more readable format. The friendly format should
use the actual month names instead of numbers (eg. February instead of 02) and ordinal
dates instead of cardinal (eg. 3rd instead of 03). For example 12-11-2020 to 12-11-2022
would read: 12th of November 2020 to 12th of November 2022.
Do not display information that is redundant or that could be easily inferred by the
user: if the date range ends in less than a year from when it begins, then it is not
necessary to display the ending year.
Also, if the date range begins in the current year (i.e. it is currently the year 2022) and
ends within one year, then it is not necesary to display the year at the beginning of the
friendly range. If the range ends in the same month that it begins, then do not display
the ending year or month.
Rules:
1. Your program should be able to handle errors such as incomplete data ranges, date
ranges in incorrect order, invalid dates (eg. 13 for month value), or empty values
2. Dates must be readable as how they were entered
Answers
The program which will convert a date range consisting of two dates formatted as DD-MM-YYYY into a more readable format will be:
from datetime import datetime
def convert_date_range(start_date, end_date):
start_date = datetime.strptime(start_date, '%d-%m-%Y')
end_date = datetime.strptime(end_date, '%d-%m-%Y')
return f"{start_date.strftime('%B %d, %Y')} - {end_date.strftime('%B %d, %Y')}"
# Example usage:
start_date = '01-04-2022'
end_date = '30-04-2022'
print(convert_date_range(start_date, end_date)) # Output: April 01, 2022 - April 30, 2022
How to explain the programIn this code example, we first import the datetime module, which provides useful functions for working with dates and times in Python. Then, we define a function called convert_date_range that takes in two arguments, start_date and end_date, which represent the start and end dates of a range.
Inside the function, we use the datetime.strptime() method to parse the input dates into datetime objects, using the %d-%m-%Y format string to specify the expected date format. Then, we use the strftime() method to format the datetime objects into a more readable string format, using the %B %d, %Y format string to produce a string like "April 01, 2022".
Learn more about program on:
https://brainly.com/question/1538272
#SPJ1
1.It is a good practice to identify a group of core methods to implement and test beforecontinuing with the rest of the class definition. What type of methods should you begin with?
2.Why is it better to implement the add operation in a collection before implementing the removeoperation?
3.What is the difference between thenumberOfEntriesdata field in the ArrayBag implementationand the DEFAULT_CAPACITY field?
4.Why is it a safer practice for thetoArraymethod to return a copy of the array instead of areference to the array?
5.What is fail-safe programming?
6.Why is it a good security practice to declare the ArrayBag to be a final class?7.Why doesn’t thecontainsmethod return the index of a located entry?
Answers
1. The method to begin with before continuing with the rest of the class definition is the core methods that serve as a foundation for the class implementation. This helps identify the correct implementation to use and simplify the remaining tasks in the class implementation.
It is better to implement the add operation in a collection before implementing the remove operation because add has more implementation methods than remove. When implementing remove, one can use the methods from the add method to simplify the implementation process.3. The numberOfEntries data field in the ArrayBag implementation refers to the number of entries that are currently in the array. The DEFAULT_CAPACITY field refers to the maximum number of entries that the array can hold when it is first created.
It is safer for the toArray method to return a copy of the array instead of a reference to the array because it prevents unintended modifications of the array. This ensures that the original array is not modified, which could cause the program to malfunction.5. Fail-safe programming is the practice of designing a program to minimize the risk of unintended consequences and errors. This is done by anticipating errors and implementing safeguards to prevent them.6. Declaring the ArrayBag to be a final class is a good security practice because it prevents the class from being modified or overridden by other classes. This ensures that the class is not tampered with and remains secure.7. The contains method does not return the index of a located entry because it is designed to simply check if the entry exists in the collection. It does not need to know the index of the entry, as it is only checking for its existence.
To know more about array visit:
https://brainly.com/question/13261246
#SPJ11
Viết thuật toán và chương trình: Tính tổng:
S=1+2+...i
Answers
Answer:
skdjsjwjdjcdjejxjdjxjdjwjsjxjdwiskxmdjxkdnejxj
Explanation:
justnejedjdfhjxnfbcjccjcuvjjfhedcjcjchcjeidchdjchcjdjcjcucjf
How to calculate usps rate online?
Answers
Please choose one of the options below. Price a postcard, please. Look at the flat rate envelopes. A look at Flat Rate Boxes Determine the cost based on the shape and size.
How do boxes work?Boxes come in many sizes, from the size of a matchbox to the size of a shipment box for furnishings, and they may be used for anything from practical to decorative purposes. packaging a variety of products that could require additional protection while being transported or stored. Also, they provide more efficient thermal protection than other kinds of packaging that could damage goods while in transit.
A postcard: What Is It?Moreover, postcards are kept as mementos. Currently, the majority of businesses and individuals utilise postcards for marketing objectives due to their efficiency.
To know more about Box visit :
https://brainly.com/question/23951385
#SPJ4
Mary is writing an article about the animal kingdom she wants to place a image below the text which menu should Mary choose for this purpose
Answers
Answer:
we any
Explanation:
it doesn't really matter
insert the following letters into an empty b-tree of order 5 in the order given: box in your final b-tree. h o t q b f x j d s g z i r e v c k w a
Answers
The final B-tree would look like this:
```
q
/ | \
h o t b f j x r
\ / \ / \ / | / \
d g i k w a box v c e s z
```
To insert the given letters into an empty B-tree of order 5, we start by creating a root node with the first letter "h". Since the order is 5, we can insert up to 4 more letters in the root node. Next, we insert "o", "t", and "q" in the root node in the order given.
Now the root node is full, so we split it and move the middle value "q" up to a new root node. The left node contains "h", "o", and "t", and the right node contains "b", "f", "x", "j", "d", "s", "g", "z", "i", "r", "e", "v", "c", "k", "w", and "a".
We can now insert "box" into the B-tree. Starting at the root node, we compare "b" with "q" and follow the left child pointer since "b" is less than "q". In the left node, we compare "b" with "h" and follow the left child pointer since "b" is less than "h". In the leftmost node, we can insert "b" since there is room.
Next, we compare "o" with "q" and follow the right child pointer since "o" is greater than "h" but less than "q". In the right node, we compare "o" with "f" and follow the right child pointer since "o" is greater than "f". In the second rightmost node, we can insert "o" since there is room.
Next, we compare "x" with "q" and follow the right child pointer since "x" is greater than "q". In the right node, we compare "x" with "r" and follow the left child pointer since "x" is less than "r". In the second leftmost node, we can insert "x" since there is room.
Finally, we compare "box" with "q" and follow the right child pointer since "box" is greater than "q". In the right node, we compare "box" with "r" and follow the right child pointer since "box" is greater than "r". In the rightmost node, we can insert "box" since there is room.
The final B-tree would look like this:
```
q
/ | \
h o t b f j x r
\ / \ / \ / | / \
d g i k w a box v c e s z
```
This is a valid B-tree of order 5 that contains all the given letters in the order given.
Learn more about pointer here:
https://brainly.com/question/31666990
#SPJ11
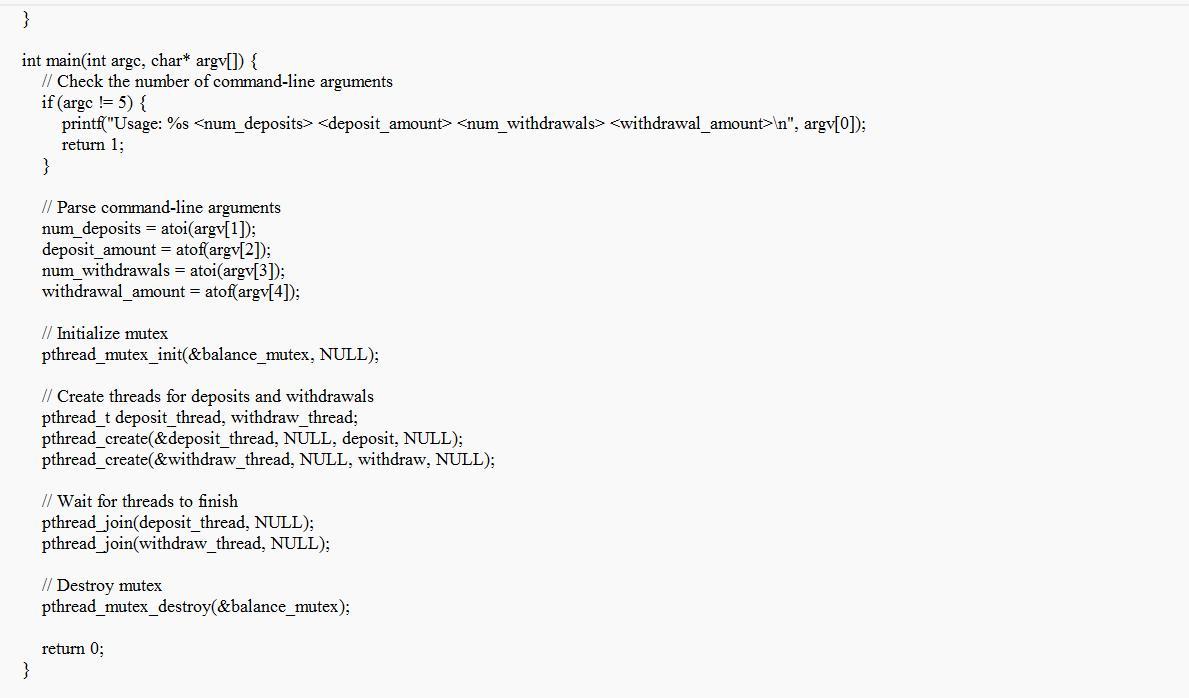
Using pthread library, write a program abc123-prog.c, which takes 4 command line arguments as follows (abc123 should be your abc123):
> ./abc123-prog a b c d
a int (# of deposits)
b double (amount of each deposit)
c int (# of withdrawals)
d double (amount of each withdrawal)
Answers
The example of a program written in C using the pthread library that takes 4 command-line arguments and performs deposits and withdrawals is given below
What is the program?In the code given, One is presuming that there are no limitations on performing deposits and withdrawals simultaneously. In practical situations, it may be necessary to use further synchronization techniques to maintain the accuracy of data and avoid situations in which multiple processes compete for resources.
So, this instance involves making three deposits of $100 and two withdrawals of $50. In order to securely conduct deposits and withdrawals in a multi-threaded environment, the program utilizes mutex locks to synchronize access to the balance variable.
Learn more about program from
https://brainly.com/question/26134656
#SPJ4


What is the name of an application that appears to look like a helpful application but instead does harm to your computer
Answers
Hope this helps (:
Answer:
Trojan Horse
Explanation:
What is the name of an application that appears to look like a helpful application but instead does harm to your computer
TROJAN HORSE
To add a button to a screen in App Inventor, where would the Button component be dragged to
Answers
The Button component would be moved to the design area on the right-hand side of the screen by dragging it from the "User Interface" part of the Palette.
Where in App Inventor can you add elements to the screen of your app?Components are dragged from the Components Palette and dropped on the design screen. Label, Sound, and Button are a few examples of components.
Which element is utilised in app design to display text on the screen?Label. Labels are tools for displaying text. The text that is defined by the Text attribute is shown on a label. The positioning and look of the text are governed by additional characteristics, all of which can be changed in the Designer or Blocks Editor.
To know more about User Interface visit:-
https://brainly.com/question/15704118
#SPJ1
In the code below, what's the final value of the variable x?
var x = 10;
X = x + 7;
X = X* 3;
A:51
B:34
C:10
D:21
Answers
x=10 so we substitute 10 into the spots for x in the beginning
x=10+7
x=17*3
x=51
Where you see the var x replace it with 10.
X = x + 7
X = 10 + 7 = 17
Substitute the value of the first var X in the equation
X = X* 3
X = 17 * 3 = 51
Therefore the final value of var x is 51 option A
A database opened in ________ mode allows only one user at a time the ability to open and edit the database
Answers
Answer:
A database opened in exclusive mode allows only one user at a time the ability to open and edit the database.
10. Specify a suitable quality number for the gears in the
drive
for an automotive transmission.
Answers
In the case of automotive transmissions, the ideal quality number for gears in the drive is greater than 6.
Quality number is the number of speeds divided by the number of gears. A higher quality number indicates that the transmission can handle a wider range of speeds with a smaller number of gears. The number of gears and speeds in an automotive transmission varies depending on the manufacturer and the intended use of the vehicle.
A typical automotive transmission, for example, may have between four and ten speeds, with six being the most common. However, transmissions with higher quality numbers are becoming increasingly popular because they provide a more efficient and comfortable driving experience.
To know more about transmissions visit:-
https://brainly.com/question/33396210
#SPJ11
which generational group is most comfortable using digital technologies?
Answers
Generation Z is the generational group most comfortable using digital technologies.
The generational group that is most comfortable using digital technologies is often referred to as Generation Z, also known as Digital Natives. Generation Z includes individuals born between the mid-1990s and the early 2010s, who have grown up in a world where digital technologies are prevalent.
Generation Z has been immersed in digital technologies from a young age, and they have grown up using smartphones, tablets, social media platforms, and various digital applications. They are highly skilled in navigating digital interfaces, adapting to new technologies, and utilizing online resources for communication, learning, entertainment, and other aspects of their lives. This comfort and familiarity with digital technologies can be attributed to their exposure and early adoption of these tools throughout their formative years.
The digital native characteristics of Generation Z make them the most comfortable and proficient when it comes to using digital technologies. Their inherent understanding and ease of use with digital tools have shaped their behaviors, preferences, and expectations in the digital realm. As a result, they are often considered early adopters of new technologies and play a significant role in shaping digital trends and innovations.
To know more about Generation Z, visit
https://brainly.com/question/23344425
#SPJ11
Select the best answer to the following question.
Remote data storage and the ability to access data from any device using the Internet is called
Answers
Answer:
I think its called "cloud computing"
Answer:
cloud computering
Explanation:
I need help please hurry!!!!!!! jay works in the it department. his main responsibility at work is to keep all equipment working. he needs to know what maintenance to perform and when. he should _____.
inventory all equipment
copy the user's manual and distribute it to all the employees
read the manuals
update the software in the office
establish the frequency of maintenance tasks
identify individuals to complete the tasks
set up auto reminders
list the maintenance tasks
create a log to document maintenance
Answers
Jay is employed with the it division. Maintaining the functionality of all equipment is his primary duty at work. He must understand what upkeep to execute and when to decide to perform maintenance.
He needs to decide how often to perform maintenance. The number of jobs that must be completed in a certain amount of time is referred to as maintenance frequency. Its periodicity can also vary based on the set time, from daily to weekly. Work equipment comprises a working platform, fall arrest devices, and any gear, computers, apparatus, tools, or installations used exclusively or mostly for work-related purposes. Task analysis examines how a task is carried out and includes a thorough description of both manual and mental processes, the lengths of the task and its elements, and task frequency.
Learn more about computers here
https://brainly.com/question/20414679
#SPJ4
is it okay to say that you picture yourself walking to morning classes at a univesrity on an application
Answers
Answer:
It is generally acceptable to describe your goals and aspirations in a college application or other similar document. If you are describing your goals in the context of applying to a university, it is fine to mention that you envision yourself walking to morning classes at the university. However, it is important to keep in mind that the purpose of a college application is to showcase your skills, achievements, and potential as a student, so it is a good idea to focus on demonstrating your readiness for academic success and your potential to contribute to the university community. It may also be helpful to explain why you are interested in attending that particular university and how it aligns with your long-term goals and aspirations.
Explanation:
Using style guidelines help a writer determine which topics to cover. arguments to cover. sources to cite. margin settings to apply.
Answers
Answer:
sources to cite.
Explanation:
A citation style guidelines is used by the writer to cite the sources of other writers in his/her work. These style guidelines are used in academic writings to acknowledge the rightful person of any thought or an idea, to avoid plagiarism.
Plagiarism, in simple terms, can be defined as an academic theft. It is an act in which a person uses other's thoughts and ideas to convey it as their own thoughts and idea. To avoid such academic crimes, various citation style guidelines are formes. Such as MLA, APA, etc.
So, the correct answer is 'sources to cite.'
Answer:
C
Explanation:
Microsoft vs Sony who wins
Answers
Answer:
Microsoft
Explanation:
Can a dod activity enter into a service contract for a military flight simulator without getting a waiver from the secretary of defense?.
Answers
Answer: DoD is prohibited from entering into a service contract to acquire a military flight simulator.
Explanation:
hope this helps
Yes, it is possible for a DoD activity to enter into a service contract for a military flight simulator without obtaining a waiver from the Secretary of Defense
What is dod activityThe rules and needs for a military flight simulator contract for a DoD activity can change depending on different factors like the type and size of the contract, where the money is coming from, and any laws or rules that apply.
Usually, a DoD activity can make a deal for a military flight simulator without needing permission from the Secretary of Defense. However, sometimes it may be necessary to get permission or approval if special circumstances apply.
Read more about secretary of defense here:
https://brainly.com/question/1498711
#SPJ2
what are overlapping geographical areas within a cellular network called?
Answers
2. What changes, if any, could Lisa make to her income?
Ramsey classroom
Answers
Answer: what changed if any could lisa make to her income
Explanation:
Where do the projection lines converge in a perspective sketch?
Answers
Answer:
Option B, Vanishing point
Explanation:
The complete question is
Where do the projection lines converge in a perspective sketch?
A. the ground line
B. the vanishing line
C. the eye point
D. the horizon line
Solution
A point lying on the image of a perspective drawing where the drawings ( two-dimensional perspective projections) of two parallel line meet in three dimensional space is known as Vanishing point
In 3 sentence explain what is a spreadsheets.
Answers
Answer:
A spreadsheet is a computer application for organization, analysis and storage of data in tabular form. Spreadsheets were developed as computerized analogs of paper accounting worksheets. The program operates on data entered in cells of a table.
Hope this helped, have a good day
HELPPPP
When searching for information on the Internet, you will often need to use more than one ____.
--------------------------------------------------------------------------------------------------------
a. browser
b. search engine
Answers
Answer:
Browser
Explanation:
Answer:
Shaerch engine
Explanation:
I just did it
state three advantages of using a printer
Answers
Answer:
Advantage: Convenience. One of the key advantages of printing out material is that it is convenient.
Advantage: Secure Delivery. Paper records can be anonymously delivered
Advantage: Ease of Reading
I hope It helps