Which of the following files and directories may be involved in setting up the environment for all system users? (Choose all that apply.)
A. /etc/bash_profile/
B. /etc/profile
C. /etc/profile.d/
D. /etc/bashrc
E. /etc/bash.bashrc
Answers
The files and directories that may be involved in setting up the environment for all system users are "A; /etc/bash_profile, B; /etc/profile, C: /etc/profile.d/, D: /etc/bashrc, and E; /etc/bash.bashrc".
The user environment is established in these files and directories. Different actions occur when the user is logging in, including launching applications and executing scripts. The user's environment is used in all of these situations, so it's essential to keep it organized and well-maintained.
The following files and directories may be involved in setting up the environment for all system users:
/etc/bash_profile: This file is executed whenever a user logs in, and it is generally used to establish the user's initial environment. The user's environment is established by setting environment variables, creating aliases, and running scripts./etc/profile: This file is read by all Bourne-style shells, including bash, and it is executed when a user logs in./etc/profile.d/: This directory contains files that will be read by /etc/profile. /etc/bashrc: This file is read whenever bash is started as a non-login shell. In other words, it's executed when a shell is started in an already established shell environment. /etc/bash.bashrc: This file is read by every bash shell, including login shells and non-login shells.You can learn more about files and directories at
https://brainly.com/question/14614936
#SPJ11
Related Questions
What is single user operating system? Write two examples.
Answers
Answer:
Single-User/Multitasking OS
An operating system that allows a single user to perform more than one task at a time is called Single-User Multitasking Operating System. Examples include Microsoft Windows and Macintosh OS.
Answer:
The single user operating system is a system which provides the facilities to be used on one computer by only one user
Explanation:
Eg: Ms Dos , mobile operating system , windows 95 , etc.
What can organizations use in their computer systems that allow the system to continue to process database transactions after a hard drive failure
Answers
Organizations can utilize technologies such as redundant arrays of independent disks (RAID) and database replication to ensure continued processing of database transactions even after a hard drive failure.
To ensure uninterrupted processing of database transactions in the event of a hard drive failure, organizations can employ redundant arrays of independent disks (RAID) and database replication. RAID technology involves combining multiple physical disks into a single logical unit, which provides increased data redundancy and fault tolerance. Different RAID levels, such as RAID 1 (mirroring) or RAID 5 (parity), offer various levels of redundancy and performance trade-offs.
By implementing RAID, organizations can distribute and replicate data across multiple drives, allowing the system to continue processing transactions even if one or more drives fail. In the case of a hard drive failure, the system can retrieve the necessary data from the redundant drives, ensuring data integrity and minimizing downtime.
Additionally, organizations can employ database replication techniques to further enhance data availability. Database replication involves maintaining multiple copies of the database across different systems or servers. In the event of a hard drive failure, the system can switch to a replica or secondary database instance, allowing uninterrupted transaction processing. Through replication, organizations can ensure data consistency and provide failover capabilities to handle hardware failures without significant disruption.
In conclusion, technologies such as RAID and database replication enable organizations to maintain the processing of database transactions even after a hard drive failure. These approaches provide data redundancy, fault tolerance, and failover capabilities, ensuring continuous availability and minimizing the impact of hardware failures on the system's operations.
Learn more about RAID here:
https://brainly.com/question/31107356
#SPJ11
1. what is the internet infrastructure stack? what is the relevance of this technological concept to marketers? what is the significance of cloud computing in relationship to the internet infrastructure? who is the leader in cloud computing for third parties by revenue, cisco, ibm, , or amazon?
Answers
The correct answer is Internet infrastructure stack are sets of hardware and services combined together which helps in making the data and information available on the web page.
Any hardware component that is housed inside a computer. a set of guidelines or software that instructs a computer on what to do or how to carry out a certain task (computer software runs on hardware). a computer application that gives users the resources they need to do a certain task. any hardware component that is housed inside a computer. a set of guidelines or software that instructs a computer on what to do or how to carry out a certain task (computer software runs on hardware). a computer application that gives users the resources they need to do a certain task.
To learn more about hardware click on the link below:
brainly.com/question/15232088
#SPJ4
Write a program that takes a string as an input. If the string entered is equal to
“Chicken”, print “This is equal” to the screen. If the string entered is not equal to
“Chicken”, print “This is not equal” to the screen.
Answers
The program could be written using a python script.
Python script on string operationThe program takes a string as an input. First, declare a variable for the input:
var = str()
#The above code will ask for a string to be inputted
Next would be to condition the script in a particular direction using the 'if' statement. That is, a Boolean function.
if var ==('chicken'):
#The above code will compare the inputted string to the word 'chicken'.
print("This is equal")
#The screen will display 'This is equal' if the inputted stringis the same as 'chicken'.
else:
print("This is not equal")
#The screen will display "This is not equal" if the inputted string is not the same as 'chicken'.
In summary, the code goes thus:
var = str()
if var ==('chicken'):
print("This is equal")
else:
print("This is not equal")
More on python scripts can be found here: https://brainly.com/question/14378173
#SPJ1
Point to ______ of a cell to fill the cell to the right or down.
A. The bottom right corner
B. An edge
C. The bottom left corner
D. The center
Answers
Answer:
It's "The bottom left corner"
Explanation:
Hope this helps:):)
do you have to be in hard mode in terraria to make the timeless traverler vanity set
Answers
For this challenge you will need to write a program that will produce the display for the individual frames, given the user inputting the number of pins knocked down in each frame of bowling.
Rules:
• The game of bowling consists of 10 frames, where a player gets 2 attempts to knock down 10 pins.
• If the player knocks down all 10 pins on the first roll, that should be displayed as X, and the next number will be the first roll of the next frame.
• If the player doesn't knock down any pins, that should be displayed as -
• If the player gets a spare (knocks down the remaining pins on the second roll of the frame, that should be displayed as /
The user will input integers tha represent the number of pins that have been kncked down on each roll. The list is not a fixed size, as bowling a perfect game requires only 12 rolls, while most games would use more rolls. Use anvil to make this and send the link.
Answers
This method takes a list of numbers that represent how many pins were knocked down on each roll and outputs a string that displays the separate frames in accordance with bowling rules.
In bowling, how many pins are there?At the start of each frame, ten pins are placed at the end of the bowling lane. With the triangle's point towards the bowler, they are positioned in a triangle arrangement.
function score(display frames):
body num = 1
0 for roll num
Result: ""
range(len(scores)) for I
If roll num = 3 and frame num = 10:
break
If roll num = 1 and scores[i] = 10:
result += "X "
frame num plus one
if roll num == 1, then
score(s[i]) + output += str(i) + " "
roll num plus one
else:
if scores[i-1] plus scores[i] equal 10, then
result += "/ "
else:
score(s[i]) + output += str(i) + " "
frame num plus one
0 for roll num
bring back output.strip ()
# A sample of usage
Result = [10, 7, 3, 9, 0, 10, 0, 8, 8, 2, 0, 6, 10, 10, 10, 8, 1]
print(display frames(scores)) # Results: X 7/9 - X 0/8 - X X/X/X 8 1
To know more about outputs visit:-
https://brainly.com/question/19088371
#SPJ1
how many conductors are provided by the ata-66 ide cable specification?
Answers
The ATA-66 IDE cable specification provides a total of 80 conductors.
These conductors consist of 40 data conductors and 40 grounding conductors, which helps to reduce signal interference and improve data transfer speeds.
Ultra ATA/66 is the next generation ATA/IDE hard drive interface. This high-speed interface allows host computers to send and retrieve data faster removing bottlenecks associated with system performance. Short for Integrated Drive Electronics, IDE is more commonly known as ATA or PATA (parallel ATA). It is a standard interface for IBM computers that was first developed by Western Digital and Compaq in 1986 for compatible hard drives and CD or DVD drives.
Learn more about signal interference: https://brainly.com/question/23179434
#SPJ11
Which of the following is NOT a method for applying the SDLC model?
ITIL
Lean
IPO
Agile
Answers
Answer:
IPO is not a mehod for applying the SDLC .
How is the aperture speed of three hundred and twentieth of a second displayed on a camera?
Answers
The aperture speed of three hundred and twentieth of a second displayed on a camera is known to be one that the shutter seen in your camera will be open for about three hundred and twentieth of a second of a second.
How is the shutter speed shown?The diameter of the aperture stop is referred to as the "aperture" in photography (sometimes known as the "f-number") (the stop that determines the brightness in a photo at an image point). Contrarily, shutter speed refers to the overall amount of time the camera's shutter is open.
Therefore, Always express shutter speed in seconds or fractions of seconds. For instance, a single number with a quote mark or the letter "s" at the end, such as 1′′ or 1s, is often used to indicate a shutter speed of one second.
Learn more about aperture speed from
https://brainly.com/question/13972212
#SPJ1
The aperture speed of three hundred and twentieth of a second is displayed on a camera as \(f\)/ 320.
What is aperture speed?Aperture speed means how wide the aperture slot is. It's the diameter of the aperture slot. It also intensifies the amount of light that reaches the sensor of the camera.
There are two things displayed on the camera, the aperture speed is written as \(f\) and the number. The other is the shutter speed, which is written as; if the speed is supposed three hundred and twentieth of a second. Then it will be written as 1 / 320.
Therefore, on a camera, the aperture speed is shown as \(f\) / 320, or three hundred and twentieth of a second.
To learn more about aperture speed, refer to the below link:
https://brainly.com/question/28959586
#SPJ1
What type of cloud infrastructure delivers services based on security requirements, the mission-critical nature of the applications, and other company-established policies that supports organizations that want to maintain higher security standards for some data but have less-sensitive data that does not require intranet-level protection?.
Answers
Private cloud computing offers features like scalability and self-service that are similar to those of public cloud computing.
What is cloud infrastructure ?
The set of hardware and software components needed to enable cloud computing make up cloud computing infrastructure. It consists of computer and network resources.Through the development of cloud networks that effectively store data remotely, a cloud infrastructure engineer contributes to the development of the networks and systems needed for computer cloud systems.Public, private, hybrid, and multiclouds are the four primary categories of cloud computing. The three primary categories of cloud computing services are infrastructure as a service (IaaS), platforms as a service (PaaS), and software as a service (SaaS).Network, servers, storage, and virtualization are the four elements of cloud infrastructure that each contribute to the success of an organization's application deployment and service delivery.To learn about infrastructure refer to :
https://brainly.com/question/29745873
#SPJ1
How can we, with one line of code, remove all apostrophes from our column names so that the column `is_women's_fiction` would be called `is_womens_fiction` but any other column with an apostrophe in the column name would also be renamed
Answers
To remove all apostrophes from column names in one line of code, you can use the string `replace()` method in Python.
In Python, the `replace()` method allows us to replace occurrences of a specified substring in a string with a new substring.
To remove all apostrophes from column names, we can use the `replace()` method on the column names and replace the apostrophe character with an empty string.
For example, let's assume you have a dataframe with column names and you want to remove apostrophes from all the column names. You can use the following one-liner code:
df.columns = [col.replace("'", "") for col in df.columns]
This code iterates over each column name in the dataframe (`df.columns`), and for each column name, it applies the `replace()` method to remove the apostrophe (`'`) character and replace it with an empty string (`""`).
By assigning the modified column names back to `df.columns`, all the apostrophes in the column names will be removed.
This approach ensures that all column names with an apostrophe will be renamed correctly, while leaving the other column names unchanged.
Learn more about apostrophes
brainly.com/question/18077041
#SPJ11
An organization with multiple facilities wishes to reduce its water consumption. Is the following practice a 3G approach, a 4G approach, consistent with both 3G and 4G approaches, or neither a 3G nor a 4G approach. The EHS department might develop a generic approach to reduce facility water consumption, based on its expert knowledge. Yet each EHS expert would have the flexibility to work with a facility in any way he or she saw fit to reduce water consumption. Within a facility, the focus will be on high water consumption areas. That is a third generation approach, but not a fourth generation approach. That a fourth generation approach, but not a third generation approach. That is both a third and fourth generation approach. That is neither a third or fourth generation approach.
Answers
The described practice combines elements of both 3G and 4G approaches, as it involves developing a generic approach while allowing flexibility for individual experts and emphasizes targeting high water consumption areas within facilities.
The described practice is consistent with both 3G and 4G approaches.
Explanation:
Third Generation (3G) approach: The practice aligns with a 3G approach as it involves the EHS department developing a generic approach to reduce water consumption based on expert knowledge. Each EHS expert has the flexibility to work with facilities in their own way to achieve the goal, indicating a decentralized and adaptable approach.
Fourth Generation (4G) approach: The practice also aligns with a 4G approach as it focuses on specific areas within each facility that have high water consumption. This demonstrates a targeted and data-driven approach to identify and address areas of improvement.
To know more about 4G visit :
https://brainly.com/question/29761693
#SPJ11
TRUE / FALSE. for a wheat farmer in the middle of harvesting system, a fixed input would be trucks rented to haul the wheat. combines rented. workers hired. the land that had been planted.
Answers
True. For a wheat farmer in the middle of the harvesting system, trucks rented to haul the wheat, combines rented, workers hired, and the land that had been planted would be considered fixed inputs.
Fixed inputs are those that cannot be easily varied or changed in the short run. In the context of a wheat farmer in the middle of harvesting, trucks rented to transport the harvested wheat, combines rented for harvesting, workers hired to operate the machinery, and the land that has already been planted are fixed inputs. These inputs are not easily altered during the harvesting process and are necessary for the successful completion of the harvest. The farmer cannot quickly adjust or change these inputs without disrupting the ongoing operation.
Learn more about input here:
https://brainly.com/question/29310416
#SPJ11
Team leaders do NOT choose which of the following?
Team members
Team facilitators
Team meetings
Team skills
Answers
Answer:
Team skills
Explanation:
The team leaders in a particular team do not choose D. Team skills.
A team leader refers to a person that is charged with the responsibility of providing instructions, guidance, leadership, and direction to a team in order to achieve a particular goal.A team leader chooses the members of a team. The team leader chooses the people that he or she believes will help the team to achieve their goals.Also, the team leader chooses the team facilitators and team meetings. The team leader selects the appropriate time that the team members will be available. This is done to ensure that every member of a team is available.It should be noted that the team leader doesn't choose the team skills. Every member of a team has different skills and everyone is unique in their own way.In conclusion, the team leader doesn't choose the team skills.
Read related link on:
https://brainly.com/question/24813191
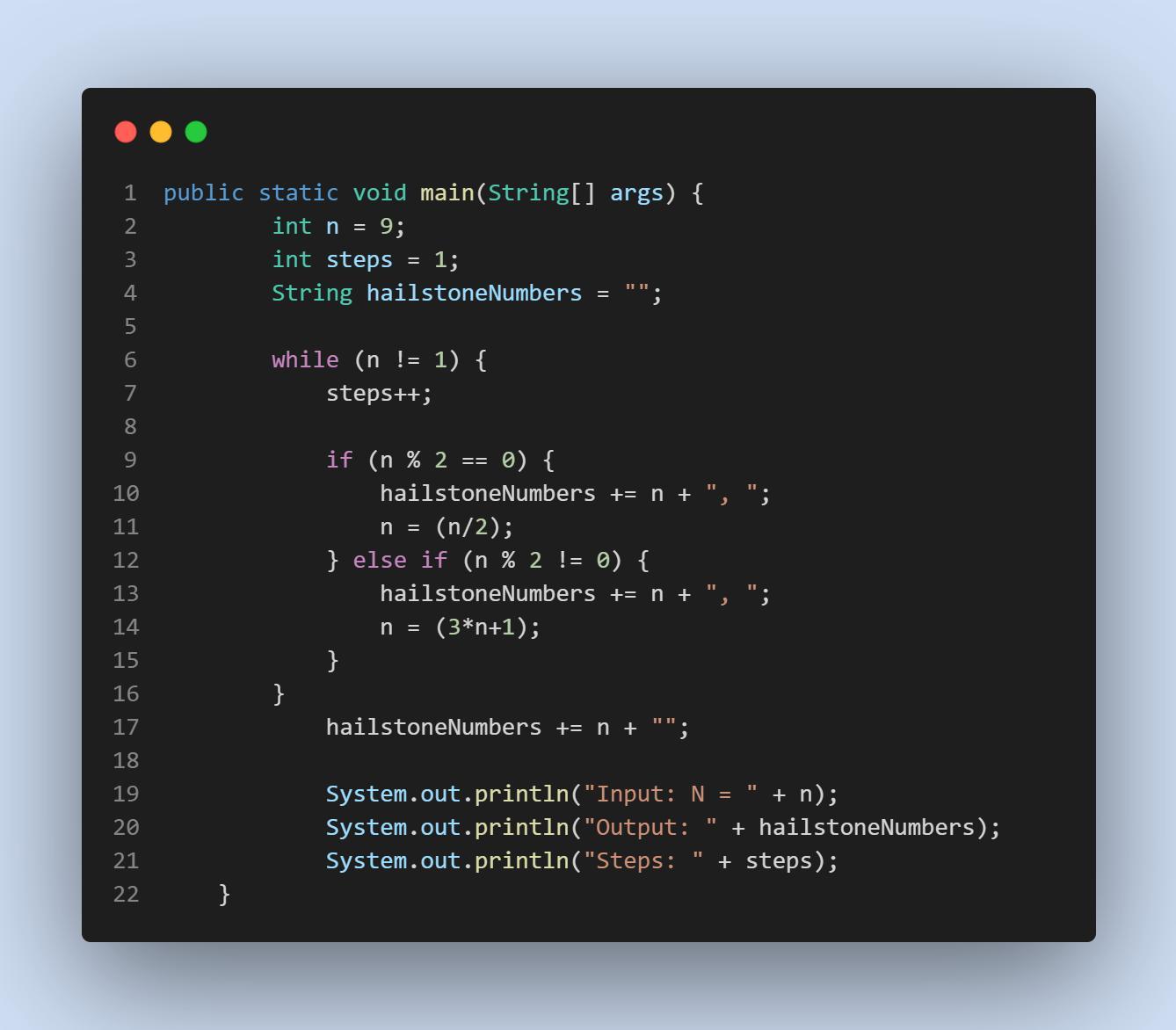
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
The____________ mode screen shows the welcome message with version details. FILL THE BLANKS
Answers
Answer:
3d mode screen shows the welcome massage with version details
write a class named acc2 containing: an instance variable named sum of type integer initialized to 0
Answers
The TupleClassObject's value can be obtained from the index passed as a parameter by calling the getValue() method in the org. javatuples library.
What is JavaTuples getValue() method?The value of the TupleClassObject is retrieved from the index supplied as a parameter using the getValue() function in the org.javatuples package. Any tuple class object from the javatuples library can be used using this function. It returns an Object value that is the TupleClassObject element present at the index that was supplied as an argument. Use of getValue() forfeits type safety because the returned Value is of the Object type.Create the class Acc2 and include the instance variable sum of type integer with an initial value of 0.A getSum method that returns the sum's value.public class Acc2 {
private int sum=0;
public int getSum() {
return sum;
}
}
To Learn more About TupleClassObject's value refer to:
https://brainly.com/question/25528419
#SPJ4
15.Every CPU needs to:
a. Dissipate heat
b. Be refreshed by the computer's ROM
C. Spend time in the off state
Answers
Answer:
Dissipate heat
Explanation:
As CPU works efficiently while there is cool
What is a good first step to understanding any kind of text?
A. Create meaning
B. Find the main idea
C. Take some notes
D. Focus on details
Answers
Answer:
thanks , that's really useful
D. Focus on details
Explanation:
Another Brainly post has the answer
Find all data dependencies using the code below (with forwarding)
loop:
slt $t0, $s1, $s2
beq $t0, $0, end
add $t0, $s3, $s4
lw $t0, 0($t0)
beq $t0, $0, afterif
sw $s0, 0($t0)
addi $s0, $s0, 1
afterif:
addi $s1, $s1, 1
addi $s4, $s4, 4
j loop
end:
Answers
Write-after-Write (WAW) dependencies are present in the given code. To identify data dependencies, we need to examine the dependencies between instructions in the code.
Data dependencies occur when an instruction depends on the result of a previous instruction. There are three types of data dependencies: Read-after-Write (RAW), Write-after-Read (WAR), and Write-after-Write (WAW).
Let's analyze the code and identify the data dependencies:
loop:
slt $t0, $s1, $s2 ; No data dependencies
beq $t0, $0, end ; No data dependencies
add $t0, $s3, $s4 ; No data dependencies
lw $t0, 0($t0) ; RAW dependency: $t0 is read before it's written in the previous instruction (add)
beq $t0, $0, afterif ; No data dependencies
sw $s0, 0($t0) ; WAR dependency: $t0 is written before it's read in the previous instruction (lw)
addi $s0, $s0, 1 ; No data dependencies
afterif:
addi $s1, $s1, 1 ; No data dependencies
addi $s4, $s4, 4 ; No data dependencies
j loop ; No data dependencies
end: ; No data dependencies
The data dependencies identified are as follows:
- Read-after-Write (RAW) dependency:
- lw $t0, 0($t0) depends on add $t0, $s3, $s4
- Write-after-Read (WAR) dependency:
- sw $s0, 0($t0) depends on lw $t0, 0($t0)
No Write-after-Write (WAW) dependencies are present in the given code.
To learn more about WAW click here:
brainly.com/question/31558213
#SPJ11
The _________________ component defines the correct granularity for access controls and oversees the relationships between identities, access control rights, and IT resource availability. A. Authentication B. Authorization C. User Management D. Credential Management
Answers
The correct answer to your question is option B: Authorization. The authorization component is responsible for defining the correct granularity for access controls .
which means it determines who can access which IT resources based on the user's identity and access control rights. The component oversees the relationships between identities, access control rights, and
IT resource availability to ensure that access to sensitive data and systems is restricted only to authorized users.
The authorization component uses a set of rules and policies to determine the level of access that each user should have based on their role and responsibilities.
This component is a critical part of any security infrastructure, as it ensures that sensitive information and resources are protected from unauthorized access, theft, and misuse.
To learn more about : access controls
https://brainly.com/question/29645753
#SPJ11
__________ is used to create a document for multiple recipients.
Answers
32.
To give an existing document a different name
A. retype and give it another name,
B. use the save command
C. use the same as command
D. use windows explorer to copy.
Answers
Answer:
B.
Explanation:
If you are trying to save an existing document you would use the save command and you will be prompted if you want to rename it to what ever you wish
Hope this helps :)
enables multiple users to communicate over the Internet in discussion forums is called?
Answers
The technology that enables multiple users to communicate over the internet in discussion forums is called "online forum software" or simply "forum software".
Forum software allows users to post messages and replies, create new discussion topics, and engage in conversations with other users. It provides a platform for users to share ideas, ask questions, and provide feedback on a wide range of topics.
In a typical forum, users can browse and search for topics of interest, read and reply to posts, and interact with other members of the community. Forum software can be designed for specific purposes, such as support forums for a product or service, educational forums for students and teachers, or social forums for hobbyists and enthusiasts.
Some popular examples of forum software include phpBB, vBulletin, Discourse, MyBB, and Vanilla Forums. These platforms provide various features and customization options to create a unique online community and encourage engagement among members.
Overall, online forum software provides a valuable means of communication and collaboration over the internet, allowing individuals with similar interests and ideas to connect and interact with one another.
Learn more about engagement here:
https://brainly.com/question/8081362
#SPJ11
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
What is by far the most popular dns server software available?.
Answers
Answer:
I use the server
8.8.8.8
and
8.8.4.4
Explanation:
BIND (Berkeley Internet Name Domain) is by far the most popular DNS server software available.
What is the BIND?BIND(Berkeley Internet Name Domain) is open-source software that executes the Domain Name System (DNS) protocols for the internet. It is widely used on Unix-like operating systems, including Linux and macOS, as well as on Microsoft Windows.
BIND is developed and sustained by the Internet Systems Consortium (ISC), a nonprofit organization that encourages the development of the internet.
It is the most widely deployed DNS software in the world and is used by many internet service providers, businesses, and organizations to manage their DNS infrastructure.
Thus, BIND (Berkeley Internet Name Domain) is by far the most widely used DNS server software.
To learn more about DNS server software click here:
https://brainly.com/question/13852466
#SPJ12
Using for staement. Write a C++ program to find and print the sum of values greater than a number'k, and the number of values above 'k'. Insert your number: 10 Insert the number of values 5 1 20 5 70 10 The number of values above 10 is :2 The sum of numbers above 10 is: 90
Answers
The provided C++ program uses a for loop to find and print the sum of values greater than a given number 'k' and the count of values above 'k'.
The program takes input for the number 'k' and the number of values to be entered.
It then iterates through the entered values, checks if each value is greater than 'k', and calculates the sum and count accordingly. Finally, the program displays the count and sum of values above 'k'.
The C++ program starts by prompting the user to enter the value of 'k' and the number of values to be entered. It then creates variables to store the sum and count of values above 'k', initializing them to zero.
A for loop is used to iterate through the entered values, where each value is read and checked if it is greater than 'k'. If a value is greater, it is added to the sum, and the count is incremented.
After the loop completes, the program prints the number of values above 'k' by displaying the count variable. It also prints the sum of values above 'k' by displaying the sum variable.
By utilizing a for loop, the program efficiently processes each entered value, calculates the sum and count, and provides the desired output.
To learn more about iterate click here:
brainly.com/question/30039467
#SPJ11
consider the following indicators in the ir process. no incident response plan no recording of commands failure to control access to digital info failure to report what best describes this status?
Answers
A phrase which best describes the aforementioned status in an incident response (IR) process is common forensic mistakes.
What is incident management?Incident management can be defined as a strategic process through which a business organization (company or firm) identifies, analyzes, and correct hazards and potential problems, in order to ensure that normal service operation is restored as quickly as possible to its end users after a disruption, as well as to prevent a re-occurrence of these hazards and mistakes in the future.
Generally speaking, some examples of common forensic mistakes (indicators) in an incident response (IR) process include the following:
"No incident response plan.""No recording of commands." "Failure to control access to digital info.""Failure to report.""Underestimating the scope of an incident."Read more on incident management here: brainly.com/question/11595883
#SPJ1
which of the following is something that an information systems (IS) professional would do? A. devise new ways to use computers B. turn information into meaningful decisions C. help people with their technology needs D. create and maintain computer network
Answers
Answer:B
Explanation:
it professionals build and repair computers, create and aunts in networks, and help people with their technology needs.
An example of something that an information systems (IS) professional would do is: B. turn information into meaningful decisions.
An information system (IS) can be defined as a set of components or computer systems, that is typically used to collect, store, and process data, as well as for the dissemination of information, knowledge, and the distribution of digital products.
Basically, an information system (IS) interacts with its environment by receiving data in raw forms while information are received in a usable format.
Generally, all organizations make use of an information system (IS) in the following areas:
Supply chain management.To process financial accounts.Manage their workforce.Marketing channels to reach their customers or potential customers.Transform information into meaningful decisions.In conclusion, the transformation of an information into meaningful decisions that are in tandem with organizational goals and objectives is something that an information systems (IS) professional would do.
Read more here: https://brainly.com/question/25162387