Which option shows the three deployment mode options available for Panorama, which (if necessary) allows for the separation of management and log collection?
A. Prisma, Panorama, IronSkillet
B. Log Collector, Prisma, Panorama
C. Management, Panorama, Prisma
D. Panorama, Management only, Log Collector
Answers
The correct answer is option C. The three deployment mode options available for Panorama, which allows for the separation of management and log collection are Management, Panorama, and Prisma.
In the Management deployment mode, the firewall or firewalls are managed by Panorama, and logs are stored on the firewall locally. In this mode, there is no need for a separate log collector.In the Panorama deployment mode, Panorama serves as the central management platform and log collector for multiple firewalls. In this mode, the firewall sends its logs to Panorama, which stores them centrally.In the Prisma deployment mode, Prisma Access serves as the cloud-based management and log collection platform. This mode is used for managing and collecting logs for Prisma Access deployments.Therefore, option C is the correct answer as it correctly identifies the three deployment modes available for Panorama, which allows for the separation of management and log collection.
To learn more about Panorama click the link below:
brainly.com/question/14913735
#SPJ1
Related Questions
List 10 ways how can graphic design help the community
Answers
Explanation:
Boosts brand awareness and name recognition. Saves time and money in the long run. Builds your brand's visual identity. Boosts employee morale, pride and productivity. Makes you stand out from the competition. Reinforces professionalism. Improves the readability, structuring and presentation of heavy content.
To stored three characters a computer occupies. Bytes memory space
Answers
Answer:
The computer represents all characters and numbers internally in the same fashion. In practice, memory is measured in KiloBytes (KB) or MegaBytes (MB).
Explanation:
The computer represents all characters and numbers internally in the same fashion. In practice, memory is measured in KiloBytes (KB) or MegaBytes (MB).
Alaina has implemented wpa2 and uses enterprise authentication for access points in infrastructure mode. What encryption protocol is her network using?.
Answers
Since Alaina has implemented wpa2 and uses enterprise authentication for access points in infrastructure mode. The encryption protocol that her network is using is Advanced Encryption Standard (AES).
What is the function of the Advanced Encryption Standard, or AES?The Advanced Encryption Standard, also referred to by its former name Rijndael, is a standard for the encryption of electronic data created by the National Institute of Standards and Technology of the United States in 2001.
Hence, The United States government selected the Advanced Encryption Standard (AES) as a symmetric block cipher to safeguard sensitive data. AES is used to encrypt sensitive data in hardware and software across the globe. For the protection of electronic data as well as government computer security and cybersecurity, it is crucial.
Learn more about Advanced Encryption Standard from
https://brainly.com/question/14784819
#SPJ1
One aspect of
is satisfied when a user understands how to use a program.
O accessibility
O reliability
O performance
O learnability
NEED ASAP!!!!!!!
Answers
Answer: learnability
Explanation:
Edg 2021
Answer:
Answer: learnability
Explanation:
The following table shows the responses obtained when a set T of six tests is applied to a two-output combinational circuit C with any one of a set of eight faults F present.101000 100100 7010100 f101011 0010100 101111 5000100 f001011 a a 1 1 1 0 0 0 0 0 0 1 0 0 3000100 0 0 1 0 2010-00 f-01111 f110100 1234.5 6
Answers
The table provided seems to show the test responses obtained for a set T of six tests applied to a combinational circuit C with any one of a set of eight faults F present.
The table includes a mix of binary and decimal numbers, and some values are marked with 'a or 'f'. It is unclear what these values represent without additional context. However, it can be inferred that the tests were conducted to detect faults in circuit C. The results of the tests can be analyzed to identify which faults are present in the circuit. To do this, a fault dictionary can be constructed that maps each possible fault to the corresponding output response for each test. By comparing the actual responses with the expected responses for each fault, the presence of faults in the circuit can be identified.
Learn more about Circuit here:
https://brainly.com/question/15449650
#SPJ11
when asking a question how do u add a photo for others to also see
Answers
Answer:
click on the thing that looks like a paper clip and select a file (microsoft computers)
Explanation:
Match the encoding data properties and features. Point Line Area Form Position Size Angle/Slope Quantity Color: Saturation Color: Lightness Pattern Motion Symbol/Shape Color: Hue Connection/Edge Containment A. Categorical Attributes B. Quantitative Attributes C. Relational Attributes D. Marks
Answers
Answer:
Lightness / Hue - Relational Attribute
Size / Position - Quantitative Attribute
Motion Symbol - Categorical Attribute
Explanation:
Relational Attributes are one which specifies the characteristics of contents in the cell. They are applied to the entire selection. Categorical attributes are one which specifies the content from other. This can be applied to specific content. Quantitative attributes are one which are numerical characteristics of content.
Arthur Meiners is the production manager for Wheel-Rite, a small manufacturer of metal parts. Wheel-Rite sells 10,378 gear wheels each year. Wheel-Rite setup cost is $45 and maintenance cost is $0.60 per sprocket per year. Wheel-Rite can produce 493 gear wheels per day. The daily demand for the gear wheels is 51 units. Show your work.
1. What inventory management model should we use to solve this problem?
Model for discount purchases
Model Economic Quantity to Order
Model Economic Quantity to Produce
Model to handle dependent demand
2. What is the optimal amount of production? 3. What is the maximum inventory level of gear wheels that will be in the Wheel-Rite warehouse? 4. What is Wheel-Rite's annual setup cost? 5. What is the annual cost of maintaining Wheel-Rite?
Answers
2. To calculate the optimal amount of production using the EOQ model, we need the following information:
- Demand per year (D) = 10,378 gear wheels
- Setup cost (S)= $45
- Production rate per day (P) = 493 gear wheels
- Working days per year (W) = 365 (assuming no downtime)
The formula to calculate the EOQ is:
EOQ = sqrt((2 * D * S) / (P * (1 - (D / (P * W)))))
Plugging in the values:
EOQ = sqrt((2 * 10,378 * 45) / (493 * (1 - (10,378 / (493 * 365)))))
Calculating this equation will give you the optimal amount of production.
3. The maximum inventory level of gear wheels that will be in the Wheel-Rite warehouse can be calculated by multiplying the optimal amount of production (EOQ) by the number of production cycles in a year. The number of production cycles can be calculated by dividing the annual demand (D) by the optimal amount of production (EOQ) and rounding up to the nearest whole number.
Maximum inventory level = EOQ * ceil(D / EOQ)
4. Wheel-Rite's annual setup cost can be calculated by multiplying the setup cost (S) by the number of production cycles in a year.
Annual setup cost = S * ceil(D / EOQ)
5. Wheel-Rite's annual cost of maintaining inventory can be calculated by multiplying the holding cost per unit (which is the maintenance cost per sprocket per year) by the average inventory level. The average inventory level can be calculated by dividing the maximum inventory level by 2.
Annual cost of maintaining inventory = (Holding cost per unit) * (Average inventory level)
In this case, the holding cost per unit is $0.60 per sprocket per year, and the average inventory level can be calculated as (Maximum inventory level / 2).
Please note that you need the calculated EOQ value from question 2 to answer questions 3, 4, and 5.8
what are the answers for theses question?




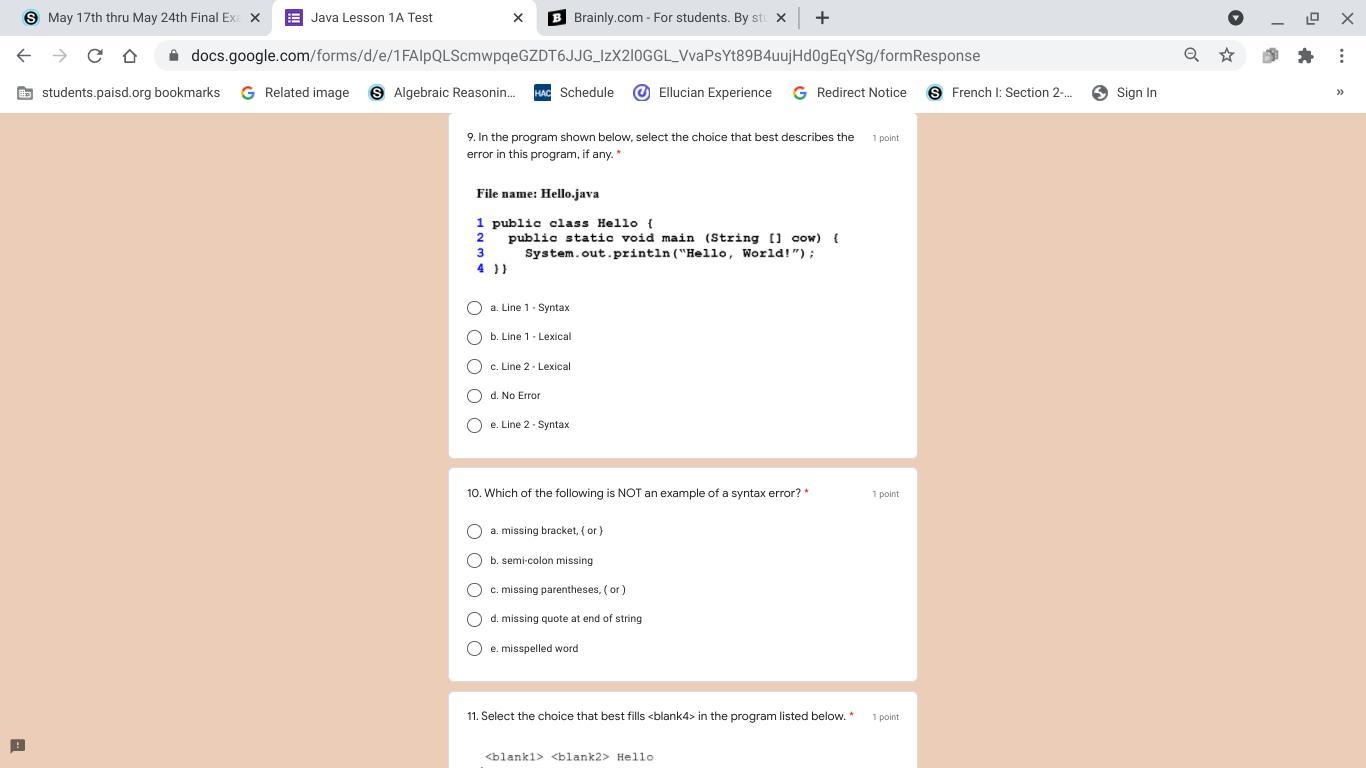
Answers
Answer: me no comprende coding
Explanation:
sorry
Alexis wants to learn HTML and CSS. She wants to test your coding skills in these design languages how can she practice code writing abilities?
Answers
Thank You!
A softcopy is also called
A) draft copy
B) hardcopy
C) print out
D screen output
Answers
Answer:
D) screen output.
A softcopy refers to an electronic version of a document or information that is displayed on a computer screen or other digital device. It is also called screen output because it is displayed on the screen and can be edited or viewed without the need for a physical printout. A hardcopy, on the other hand, refers to a physical printout of a document or information. A draft copy refers to an early version of a document that may be incomplete or subject to further revisions.
Explanation:
One way to insert a page break is to choose page break from the Insert tab.
true or false
Answers
music sites through schools wifi 2020 What is one thing a person should do to stay safe when exercising? 100 pts.!
Answers
Answer:
They should stay away from others (keep workout short or at home)
always do The exercise right-properly
Explanation:
Answer:
they should stay at home and do workouts or they can start a fitness program in a safe area.
Cryptography has requirements include:
A. easy to compute and not invertible
B. tamper-resistant
C. collision-resistant
D. All the above
Answers
Answer:A i think
Explanation:
How do i fix this? ((My computer is on))

Answers
Answer:
the picture is not clear. there could be many reasons of why this is happening. has your computer had any physical damage recently?
Answer:your computer had a Damage by u get it 101 Battery
and if u want to fix it go to laptop shop and tells him to fix this laptop
Explanation:
which of the methods below are static methods? i. length ii. substring iii. pow iv. sqrt group of answer choices only iii and iv only i, ii and iii all the methods are static only ii and iv
Answers
Only ii and iv that is substring & sqrt are static methods.
What is substring ?A substring is a segment of the named string. A substring is, in other words, a subset of another String. The built-in substring() method of the Java String class allows one to extract a substring from a given string using index values that are specified as parameters. A frequently used java.lang function is substring. Creates smaller strings from a larger one using the string class. Since strings in Java are immutable, the original string is left unchanged and a new string is returned by the method.
To know more about substring , visit
https://brainly.com/question/28290531
#SPJ4
What does business informWhat does business information management do?
A.
identify information requirements for coworkers
B.
identify information requirements for different management levels
C.
create project plans for the project management team
D.
produce sales turnover summary for the sales professionals
E.
create financial documents for the finance departmentation management do?
Answers
Answer:
B) identify information requirements for different management levels
Explanation:
Business information management is based off of identifying the needs of a company. (This is also a plato answer)
under private inheritance what will properties/methods visibility be in the child class?
Answers
Under private inheritance, the properties and methods of the base class are inherited as private members in the child class.
What will be the visibility of properties and methods in the child class when using private inheritance?When using private inheritance, the child class inherits the properties and methods of the base class as private members. This means that these members are only accessible within the scope of the child class and cannot be accessed directly by any external code.
Private inheritance is often used when the child class needs to implement the functionality of the base class, but without exposing that functionality to other classes or code outside the child class itself.
Learn more about Child class
brainly.com/question/29850140
#SPJ11
write a program that reads in integers separated by a space in one line and displays distinct numbers in their input order and separated by exactly one space (i.e., if a number appears multiple times, it is displayed only once). hint: read all the numbers and store them in list1. create a new list list2. add a number in list1 to list2. if the number is already in the list, ignore it. sample run enter numbers: 1 2 3 2 1 6 3 4 5 2 the distinct numbers are: 1 2 3 6 4 5
Answers
Using the codes in computational language in python it is possible to write a code that write a program that reads in integers separated by a space in one line and displays distinct numbers in their input order and separated by exactly one space
Writting the code:numbers = input("Enter your numbers: ")
list1 = numbers.split()
list2 = []
for i in range(len(list1)):
if not list1[i] in list2:
list2.append(list1[i])
print("The distinct numbers are: ")
for i in range(len(list2)):
print(list2[i], end=' ')
print()
See more about python at brainly.com/question/18502436
#SPJ1

determine whether some c compiler to which you have access implements the free function.
Answers
We are aware that the functions malloc() and calloc() are utilized to allocate memory for any data we wish to store in memory.
Deallocating allocated memory allows us to use that memory for other purposes when we no longer require the data in it. The free() function in C is used to reallocate allocated memory.
What is a compiler for C?A special program called a compiler converts the source code of a programming language into machine code, bytecode, or another programming language. Most of the time, the source code is written in a high-level, readable language like Java or C++.
Why use a compiler?You need a compiler to convert your code from high-level C++ to machine language that the CPU can understand because the architecture of a computer is made up of electronic switches and cables that can only function with binary 1s and 0s.
Learn more about C compiler:
brainly.com/question/28275208
#SPJ4
With _____ transmission, both parties in a global network are connected at the same time, as in a phone call
Answers
Answer:
synchronous
Explanation:
During synchronous transmission parties are exchanging messages in real time.
T/F: when we have enough buffer caches, the index-based nested loop join outperforms the block nested loop join.
Answers
The given statement "When we have enough buffer caches, the index-based nested loop join outperforms the block nested loop join" is True because the reason for this is that the index-based nested loop join utilizes the indexes that are present in the table to find the matching rows, whereas the block nested loop join reads the entire block of data from one table for each row in the other table.
When the buffer cache is large enough to hold the entire index, the index-based nested loop join can perform much faster than the block nested loop join. This is because the index-based join only needs to read the data that is necessary to complete the join, whereas the block nested loop joins has to read the entire block of data, which can be much larger.
In summary, if we have a large enough buffer cache, the index-based nested loop join can provide better performance than the block nested loop join because it utilizes the indexes present in the table and reads only the necessary data.
You can learn more about indexes at: brainly.com/question/14887928
#SPJ11
Which line of code will allow a decimal point to be stored in a variable?
Answers
Answer:
a float value u mean right?Explanation:
Answer: the answer is A
Explanation:
I got it right on my flvs 3.01 test!!!!!!!!!!!!!
For complex web development, programmers often useODNAO Visual Basic.O Swift.O scripting languages.
Answers
A scripting language may be used to control a variety of different systems, from simple applications to complex systems that span multiple servers and databases.
Scripting languages are often used in web development to create dynamic web pages that can interact with users and provide real-time feedback.
There are many different scripting languages that can be used for web development, each with its own strengths and weaknesses.Some of the most popular scripting languages for web development include JavaScript, Python, Ruby, and Perl. JavaScript is widely used for creating interactive web pages that can be updated in real-time, while Python and Ruby are often used for creating complex web applications that require large amounts of data processing and analysis. Perl is another popular scripting language that is often used for creating web applications that require a high degree of flexibility and customization.In addition to these scripting languages, web developers may also use other programming languages, such as C++, Java, and PHP, to create web applications. These languages are often used for developing more complex web applications that require a higher level of performance or that require integration with other systems or databases. Overall, the choice of scripting language for web development will depend on the specific needs and requirements of the project at hand.For complex web development, programmers often use scripting languages. These languages allow developers to create dynamic, interactive websites and applications, providing a better user experience. Some popular scripting languages used in web development include JavaScript, Python, and PHP.JavaScript is widely used for client-side scripting, meaning it runs directly in a user's web browser. This allows for real-time interactions, such as animating elements, validating form inputs, and handling user events. JavaScript frameworks, such as React, Angular, and Vue.js, can also be used to further simplify complex web development tasks.Python is a versatile scripting language often used for server-side scripting. With web frameworks like Django and Flask, Python can be used to create robust web applications and handle back-end tasks, such as database management and server-side logic.PHP is another server-side scripting language, designed specifically for web development. It is embedded within HTML, allowing developers to create dynamic web pages with ease. PHP is popular for creating content management systems (CMS) like WordPress, which powers millions of websites worldwide.In conclusion, for complex web development, programmers prefer to use scripting languages like JavaScript, Python, and PHP due to their flexibility, efficiency, and ability to create dynamic and interactive websites. While Visual Basic and Swift have their own applications, they are not the go-to languages for complex web development projects.
for more such question on Java
https://brainly.com/question/29966819
#SPJ11
NEXT
Internet and World Wide Web: Mastery Test
1
Select the correct answer
An instructor receives a text message on her phone. Next, she reads out the text to the whole claws. Which network component plays a similar
role by receiving a message and broadcasting it to all other computers connected to the component?
OA Switch
OB .
hub
OC bridge
OD
router
Reset
Wext
Answers
Answer:
hub is the correct answer
hope it is helpful to you
consider a codebase that includes a significant number of string constants, such as those used in flutter text widgets. such an application is not immediately adhering to principles of... group of answer choices adaptivity accessibility internationalization responsiveness
Answers
internationalisation . The application does not instantly follow the internationalisation tenets. Internationalization is the process of creating software that can be readily translated into other languages and cultural contexts.
The internationalisation principles are not immediately followed by the application. The process of internationalising software entails making it easily adaptable to many linguistic and cultural settings. The programme may be difficult to translate to different languages or locations if it uses a large number of string constants since these constants may be hardcoded in the source. Developers should avoid hardcoding strings in the codebase and instead employ localization strategies, such as putting them in resource files, to accomplish internationalisation. This makes it simple to translate the application into other languages and cultural contexts.
learn more about application here:
https://brainly.com/question/31164894
#SPJ4
8.if converting scada systems to the internet protocol increases the risk of a hacker taking control of an industrial process, why are companies doing just that?
Answers
Companies are trying to convert SCADA systems to Internet Protocol in order to save money and perform remote maintenance and monitoring.
What is a hacker?Computer hackers are unauthorized users who gain access to computer systems with the intent of stealing, changing, or destroying data, frequently by installing dangerous malware without your knowledge or consent.
Their deft tactics and in-depth technical knowledge enable them to gain access to information you don't want them to have.
If a SCADA system is not properly supervised, it is vulnerable. These systems are designed to keep up with the latest technological advances.
Companies are attempting to convert SCADA systems to Internet Protocol in order to save money on maintenance and monitoring.
Thus, due to this, companies are converting SCADA systems to IP.
For more details regarding hacker, visit:
https://brainly.com/question/29215738
#SPJ1
What's the difference between HTML and CSS
Answers
The difference between HTML and CSS is that HTML is used for providing a structure (skeleton) for a website while CSS informs the style (skin).
What is CSS?CSS is an abbreviation for Cascading Style Sheets and it can be defined as a style sheet programming language that is designed and developed for describing and enhancing the presentation of a webpage (document) that is written in a markup language such as:
XMLHTMLWhat is HTML?HTML is an abbreviation for hypertext markup language and it can be defined as a standard programming language which is used for designing, developing and creating websites or webpages.
In conclusion, we can reasonably infer and logically deduce that the difference between HTML and CSS is that HTML is used for providing a structure (skeleton) for a website while CSS informs the style (skin).
Read more on CSS style here: brainly.com/question/14376154
#SPJ1
When the supervisor-to-subordinate ratio exceeds a manageable span of control, additional Teams, Divisions, Groups, Branches, or Sections can be established. Which NIMS Management characteristic does this describe? Possible Answers:
a.Management by Objectives
b.Comprehensive Resource Management
c.Formal Communication
d. Modular Organization
Answers
This describes the Modular Organization characteristic of the National Incident Management System (NIMS). Modular Organization refers to the structure of an incident management organization that is divided into functional or geographical units, with each unit having defined responsibilities, resources, and reporting relationships.
Modular Organization is a structure used in incident management that divides the organization into functional or geographical units. Each unit has defined responsibilities, resources, and reporting relationships. This structure allows for efficient and effective response by managing the span of control within manageable limits and providing a clear chain of command and unity of effort. It is a key characteristic of the National Incident Management System (NIMS).
Learn more about Modular Organization: https://brainly.com/question/12774819
#SPJ4
Which graph is the solution to the system 2x – 3 and y < 2x + 4?
Answers
Answer:
B
Explanation:
Answer:
Explanation:
Edge 2021
