You start in square e6 facing south west. move three squares forward. rotate 135 degrees clockwise. move 4 squares forward. rotate 45 degrees clockwise. move 2 squares forward. rotate 90 degrees anticlockwise and move 4 squares backwards. what is the x coordinate of the square you are now in?
Answers
To get to this coordinate, you will need to follow the given sequence of moves and rotations, starting from square e6 facing southwest and ending at an x coordinate of e5.
Starting from square e6, you need to move three squares forward in the southwest direction. This will take you to square b3. Now, you need to rotate 135 degrees clockwise, which will cause you to face the northwest direction. Next, you need to move four squares forward in the northwest direction. This will take you to square d7. After that, you need to rotate 45 degrees clockwise, which will cause you to face the northeast direction. Now, you need to move two squares forward in the northeast direction. This will take you to square f8. Finally, you need to rotate 90 degrees anticlockwise, which will cause you to face the southwest direction, and move four squares backwards in the southwest direction. This will take you to square e5. Therefore, the x coordinate of the square you are now in is e5.
In conclusion, to find the x coordinate of the square you are in, you need to follow the sequence of moves and rotations starting from square e6 facing southwest and ending at the final square e5. By following the steps in the correct order, you can arrive at the final answer.
To know more about clockwise visit:
brainly.com/question/30025140
#SPJ11
Related Questions
I need some questions and answers in spreadsheet
Answers
Answer:
you need to show what you need help with
Explanation:
can you help maybe please

Answers
To automatically show a different cat image alongside its breed name whenever the 'Generate' button is clicked, we can enlist an API:
The ProgramIn this code, jQuery ties a click activity to the tab labeled 'Generate', then dispatches a AJAX request to the CatAPI to collect a random cat picture and its relevant breed.
Upon receiving a reply, the allocated HTML will be modified according to the given image and breed that was sourced out.
The program is in the image file
Read more about HTML here:
https://brainly.com/question/4056554
#SPJ1

When creating a PowerPoint presentation, what does it mean to apply movement to text or an object to control its display during the presentation? Group of answer choices animate hyperlink slide layout transitions
Answers
Answer:
animate
Explanation:
PowerPoint application can be defined as a software application or program designed and developed by Microsoft, to avail users the ability to create various slides containing textual and multimedia informations that can be used during a presentation.
Some of the features available on Microsoft PowerPoint are narrations, transition effects, custom slideshows, animation effects, formatting options etc.
Furthermore, slide transition is an inbuilt feature of a presentation software that automatically changes the slides at regular intervals.
Generally, when a PowerPoint presentation is created, applying movement to a text or an object in order to control its display during the presentation is simply referred to as animation. There are various animation effects that could be applied by the user depending on his or her choice.
Under which accounting method are most income statement accounts translated at the average exchange rate for the period ?
A) current/concurrent method
B) monetary/nonmonetary methode
C)temporal method
D)All of the options
Answers
Under the accounting method where most income statement accounts are translated at the average exchange rate for the period, the correct option is D) All of the options.
The current/concurrent method considers both monetary and nonmonetary balance sheet items and translates income statement accounts at the average exchange rate for the period. This method takes into account the fluctuations in exchange rates throughout the period and provides a more accurate representation of the financial results in the reporting currency.
By using the average exchange rate, the impact of exchange rate fluctuations on income statement accounts is spread out over the period, reducing the impact of currency volatility on reported earnings.
Learn more about accounting method here: brainly.com/question/30512760
#SPJ11
Juan plans on using an algorithm to make cookies what is yye step that he should follow I'm after he makes the cookies?
Answers
Based on a computer system and application, the necessary steps Juan should make after making the cookies include "testing the cookie to know if it works accordingly."
Other necessary steps Juan should make after making the cookies are:He may choose to set the cookie's expiration date.He would need to update the cookie after the expiration date.He may need to set a path for the cookie.He should set the defense mechanism for the cookie against security threats or breaches.What is Cookie?A cookie is a small data or message that web servers transmit to the web browser when users visit Internet sites.
Cookies are generally used to identity and track the activities of users on a website.
Hence, in this case, it is concluded that Cookies are is an excellent option to have on a website to monitor its activities.
Learn more about server cookie here: https://brainly.com/question/14102192
when asking a question how do u add a photo for others to also see
Answers
Answer:
click on the thing that looks like a paper clip and select a file (microsoft computers)
Explanation:
Are all the computer users known as programmer
Answers
Answer:
Nope
Explanation:
programmers are diff
New communication technology can impact seemingly unrelated industries such as the airline industry. This would be an example of a threat of substitute products. threat of entry. Customers tend to have negative opinions of firms that imitate other firms. forward integration.
Answers
Answer: threat of substitute products
Explanation:
Alchool is a
Please let me know thanks it should be a Depressant or both not sure thanks!.

Answers
The answer should be C. Both A and B
PLEASE HELP !!!!
Activity Research different computing platforms and discuss what steps you would take to secure the computing platform of your choice
Answers
Answer:There are many computing platforms available today, each with its own unique security features and risks. Here are some steps you can take to secure some of the most popular platforms:
Windows:
Keep Windows up-to-date with the latest security patches and updates.
Use a reputable antivirus and anti-malware software.
Enable Windows Firewall to block unauthorized access to your computer.
Create strong passwords and use a password manager to securely store them.
Avoid downloading software or attachments from untrusted sources.
Turn on User Account Control (UAC) to prevent unauthorized changes to your computer.
Consider using a virtual private network (VPN) when connecting to public Wi-Fi networks.
macOS:
Keep macOS up-to-date with the latest security patches and updates.
Use a reputable antivirus and anti-malware software.
Enable macOS Firewall to block unauthorized access to your computer.
Use FileVault to encrypt the contents of your hard drive.
Create strong passwords and use a password manager to securely store them.
Avoid downloading software or attachments from untrusted sources.
Use the built-in Time Machine backup software to regularly back up your files.
Consider using a VPN when connecting to public Wi-Fi networks.
Linux:
Keep Linux up-to-date with the latest security patches and updates.
Use a reputable antivirus and anti-malware software.
Enable the built-in firewall to block unauthorized access to your computer.
Use strong passwords and consider using two-factor authentication.
Avoid downloading software or attachments from untrusted sources.
Configure your Linux system to limit user access to sensitive files and directories.
Use a virtual private network (VPN) when connecting to public Wi-Fi networks.
Explanation:
You are building a Desktop PC for a newly hired receptionist. The computer's motherboard doesn't have a wireless network adapter integrated into it. Which of the following motherboard connections will most likely be used to connect the wireless network adapter card?
AGP
PCIe x16
PCIe x1
eSATA
Answers
The most likely connection to be used for connecting a wireless network adapter card to a motherboard without an integrated adapter is a PCIe x1 slot.
When a motherboard lacks an integrated wireless network adapter, an expansion card can be added to provide wireless connectivity. Among the given options, the PCIe x1 slot is the most suitable for this purpose. PCIe stands for Peripheral Component Interconnect Express, and it is a high-speed serial expansion bus standard commonly used in modern computers.
The PCIe x1 slot is designed for smaller expansion cards, such as network adapters, sound cards, or Wi-Fi cards. It provides a sufficient bandwidth for wireless communication and is compatible with a wide range of wireless network adapter cards available in the market. The x1 designation refers to the number of lanes available for data transfer, and while it is smaller than the PCIe x16 slot, it is more than enough for a wireless network adapter.
Using the PCIe x1 slot to connect the wireless network adapter card ensures that the receptionist's desktop PC can access wireless networks and connect to the internet without the need for additional external devices. This provides convenience and flexibility in terms of network connectivity options for the receptionist's daily tasks.
learn more about wireless network here:
https://brainly.com/question/31630650
#SPJ11
you are unable to run the apt-get update command because you do not have root privileges. what command can you run to be able to update the apt (advanced package tool) database of available packages?
Answers
To update the apt database of available packages without root privileges, you can use the command - "sudo apt-get update".
What is a command?A command in programming is a word or phrase thattells the computer to do something.
Commands are usually typed into a command-line interface (CLI), which is a text-based interface that allows users to interact with the computer.
Commands can also be executed from within aprogramming language, such as Python or Java.
Learn more about command at:
https://brainly.com/question/25808182
#SPJ4
difference between tablet and smart phone
Answers
Answer:
What is the difference between tablets and smartphones? The main difference is the size of the screen. Smartphones usually have screen sizes between 4″/10cm and 7″/17cm, a tablet is anything over this. When it comes to processing power and available apps—they usually share the same capabilities.
Explanation:
Tablets are overwhelmingly used to play games and access entertainment (67 per cent), while smartphones are divided between games, social networking, and utilities (to name a few). Basically, tablets are seen as an entertainment platform, while smartphones are considered mostly a communications device.
Convert (-5) to its binary notation using 2’s complement
format
Show your full work
Answers
To convert -5 to its binary notation using 2's complement format, follow these steps:
Convert the absolute value of the decimal number (5) to binary notation:
5 in binary = 00000101
Invert all the bits in the binary representation:
Inverting 00000101 gives 11111010.
Add 1 to the inverted binary representation:
Adding 1 to 11111010 gives 11111011.
Therefore, -5 in binary using 2's complement format is 11111011.
To verify the result, you can convert the binary representation back to decimal:
If the most significant bit is 1 (which it is in this case), it indicates a negative number.
Invert all the bits in the binary representation (11111011).
Add 1 to the inverted binary representation (00000101).
The resulting decimal value is -5.
Hence, the binary representation 11111011 represents the decimal value -5.
Learn more about binary notation here:
https://brainly.com/question/10374428
#SPJ11
Which company provides a crowdsourcing platform for corporate research and development?
A: MTruk
B:Wiki Answers
C: MediaWiki
D:InnoCentive
Answers
InnoCentive is the company that provides a crowdsourcing platform for corporate research and development.Crowdsourcing is a method of obtaining services, ideas, or content from a large, undefined group of people, particularly from the internet.
InnoCentive is a company that provides a crowdsourcing platform for corporate research and development. InnoCentive is the world's leading open innovation platform, with over 500,000 solvers in more than 200 countries and a range of Fortune 1000 firms, NGOs, and public organizations in its client list.
Clients use the platform to issue 'Challenges' which are essentially problems that are sent out to the global solver network, who then submit solutions. InnoCentive, founded in 2001, was the first company to commercialize open innovation, and today it is still the market leader in this field.
To know more about company visit:
https://brainly.com/question/30532251
#SPJ11
The appropriate software to use for creating research papers is ________ software.
Answers
The appropriate software to use for creating research papers is a word processing software.
All the researchers use word processing software such as MS Word or Office 360 words for creating the research paper or they may use online word processing software for this purpose . When researcher finishes their research or study, then they need to write their research output to present or display to their audience. They use word processing software to write research papers. In the research papers, they write what they have the research questions, objectives of the research, and its findings.
A word processing software is a type of computer program which allows for the input, output, formatting and editing of text. Modern word processing softwares offers a myriad of different features including but not limited to, spell checks, grammar checks, predictive text and automatic text corrections. All these functions prove extremely helpful in creating efficient research papers.
Presentation, spreadsheets and database softwares are all useful for data collection and analysis. They are all used in the research process but only the word processing software can create the research paper.
You can learn more about word processor at
https://brainly.com/question/985406
#SPJ4
Write a C++ program that encodes the user’s string so that they can send a "secret message" to their friends. In order to encode the string, we will use an integer offset value known as the codeInteger or encryption key. The encryption key must be between 1 and 35, inclusive. It is added to each character’s ASCII (decimal) value thus making it a new ASCII character. The letter "A" is ASCII 65. If we add 10 to it, it becomes ASCII 75, which is the letter K. Remember that spaces are also characters and should be encoded. Refer to an ASCII Character Code set to see a complete set of decimal/character values
Answers
In the `main` function, the user is prompted to enter the message and encryption key. The `encodeString` function is called with the user's inputs, and the resulting encoded message is displayed.
```cpp
#include <iostream>
#include <string>
std::string encodeString(const std::string& message, int encryptionKey) {
std::string encodedMessage = "";
for (char c : message) {
int asciiValue = static_cast<int>(c) + encryptionKey;
encodedMessage += static_cast<char>(asciiValue);
}
return encodedMessage;
}
int main() {
std::string message;
int encryptionKey;
std::cout << "Enter the message to encode: ";
std::getline(std::cin, message);
std::cout << "Enter the encryption key (1-35): ";
std::cin >> encryptionKey;
std::string encodedMessage = encodeString(message, encryptionKey);
std::cout << "Encoded message: " << encodedMessage << std::endl;
return 0;
}
```
This C++ program allows the user to encode a string by adding an encryption key (integer offset) to each character's ASCII value. The program prompts the user to enter the message they want to encode and the encryption key (which must be between 1 and 35).
The `encodeString` function takes the user's message and encryption key as inputs. It iterates over each character in the message, converts it to its corresponding ASCII value, adds the encryption key to the ASCII value, and then converts it back to the corresponding character. The encoded characters are concatenated to form the encoded message.
In the `main` function, the user is prompted to enter the message and encryption key. The `encodeString` function is called with the user's inputs, and the resulting encoded message is displayed.
learn more about encodeString here:
https://brainly.com/question/31839440
#SPJ11
write a public static method named meterstofeetandinches that will take a single argument of type double and will return a string. when called, and passed a distance value (in meters), this method must compute and return a string value with the equivalent distance in feet and inches.
Answers
double feet = meters * 3.28084;
double inches = feet * 12;
return String.format("%.2f meters is equivalent to %.2f feet and %.2f inches.", meters, feet, inches);
}
please help will give brainliest

Answers
Answer:
waterfall- google search
Explanation:
refer to the exhibit. a network administrator needs to configure router-on-a-stick for the networks that are shown. how many subinterfaces will have to be created on the router if each vlan that is shown is to be routed and each vlan has its own subinterface?
Answers
The PC, printer, IP phone, and switch control VLAN are all on different VLANs based on the IP addresses and masks provided.
Four sub interfaces on the router are necessary in this circumstance. Finally, we set sub-interfaces to begin our router configuration. We set up sub-interfaces for each VLAN on the port that connects the router and the switch. Additionally, we configured 802.1Q encapsulation using the sub-VLAN interface's number. This suggests that switching between different VLANs can be accomplished using a router and switch with a single physical interface. Multi-vendor VLAN support is provided by the IEEE 802.1Q (Dot1q) protocol, which establishes a system of VLAN tagging for Ethernet frames.
Learn more about Ethernet here-
https://brainly.com/question/13441312
#SPJ4
FILL THE BLANK. the term systems development life cycle (sdlc) describes the life of an information system from conception to _____
Answers
The term Systems Development Life Cycle (SDLC) describes the life of an information system from conception to deployment or implementation.
The Systems Development Life Cycle (SDLC) is a structured approach used in software development and information system management. It encompasses various phases, including requirements gathering, system design, development, testing, deployment, and maintenance.
The last phase of the SDLC is the deployment or implementation stage, where the developed system is installed and made operational. This involves activities like data conversion, user training, system integration, and finalizing hardware and software configurations. Once the system is successfully deployed, it enters the maintenance phase, where ongoing support and enhancements are provided. The completion of the SDLC is marked by the deployment or implementation stage, ensuring that the developed system is ready for use by its intended users.
Learn more about Systems Development Life Cycle here:
https://brainly.com/question/14804328
#SPJ11
Greg is looking around an art exhibition displaying American art from different ages. He spots the works of some famous artists. Match the
artists to the era of which they belong.
Benjamin West
Georgia O'Keeffe
Native Americans
Thomas Crawford
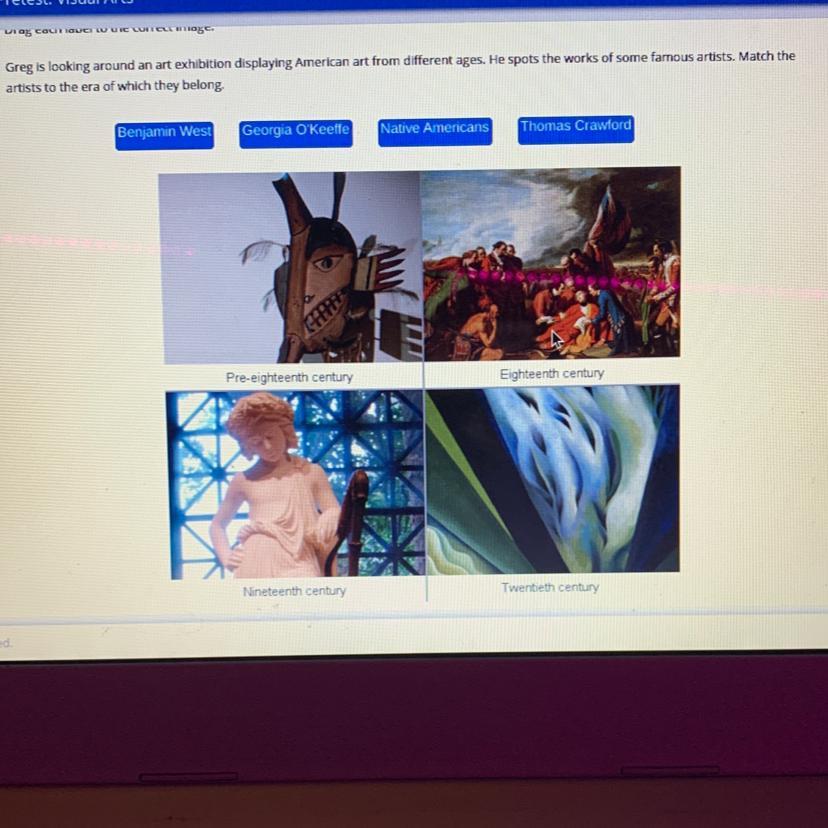
Answers
Answer:
Benjamin west is 18th century
Thomas Crawford is 19th century
Native Americans is pre-18th century
Georgia O'Keeffe is 20th century
Explanation:
Solid-state storage uses___ to store data

Answers
Answer: Capacitors
Explanation: Soild-State drives use conductors to work.
Cynthia writes computer programs for mobile phones and has received five job offers in the last week. This is most likely because:
Answers
Answer:i)the use of algorithms in the programs are efficient and less time consuming
ii)there are no errors in the programs and are very easy to understand
iii)the code is easily understandable but the program is strong and good
I NEED THIS ASAP PLS
A program that contains a command that will play a song if the user hits the “play” button is what kind of program?
A.
edited
B.
iterative
C.
selection
D.
sequence
Answers
Answer:
C
Explanation:
explain the uses of computer in police department
Answers
Answer:
Not only can police officers store records and reports in online databases, but they can also use computers and hard drives to store thousands of images, reports and videos. Computers make mass storage possible, and enable giant online databases that can accurately ID suspects anywhere in the country.
COMPUTER IN POLICE DEPARTMENT
EXPLANATION:
Not only can police officers store records and reports in online databases, but they can also use computers and hard drives to store thousands of images, reports and videos. Computers make mass storage possible, and enable giant online databases that can accurately ID suspects anywhere in the country.
HOPE THIS WILL HELP U. AND PLZ MARK ME AS A BRAINLIEST.What devices do not need device drivers to be manually installed, and start to function as soon as they are connected to a computer?.
Answers
Plug-and-play devices are electronic devices that do not require any device driver to be manually installed on the host device (computer) and as such they start functioning immediately they are connected to the host device (computer).
Plug-and-play (PnP) can be defined as a technology that is designed and developed to allow an operating system (OS) of a computer to automatically detect and configure a peripheral (input and output device) as soon as they are connected to the computer.
On a related note, a plug-and-play device is an electronic device that do not require any device driver to be manually installed on the host device (computer) and as such it start to function immediately it is connected to the host device (computer).
In Computers and Technology, some examples of a plug-and-play device include the following:
External hard-driveComputer monitorKeyboardWeb-camMouseFind more information: https://brainly.com/question/17402566
Write a program to:
• It will collect and output some basic data about the user such as name, and gender which will be
displayed with an accompanying welcome message [3]
• Use appropriate data structures to store the item code, description and price information for
the mobile devices, SIM cards and accessories [2]
• Allow the customer to choose a specific phone or tablet [3]
• Allow phone customers to choose whether the phone will be SIM Free or Pay As You Go [2]
• Calculate the total price of this transaction [4]
• Output a list of the items purchased and the total price. [3]
• Any other choice outside of these three categories would give out appropriate message to the
user and requesting the user to make a new choice. [2]
Answers
According to the question, a program using appropriate data structures are given below:
#include <iostream>
#include <string>
#include <vector>
#include <map>
using namespace std;
int main() {
string name;
string gender;
cout << "Please enter your name: ";
cin >> name;
cout << "Please enter your gender (male/female): ";
cin >> gender;
cout << "Welcome " << name << ", you are a " << gender << ".\n\n";
map<string, vector<string>> items;
items["mobile"] = {"iphone11", "1000", "samsungs20", "800"};
items["sim"] = {"sim1", "30", "sim2", "40"};
items["accessories"] = {"charger", "20", "headphone", "30"};
string choice;
cout << "Please choose a device (mobile/sim/accessories): ";
cin >> choice;
string phone;
if (choice == "mobile") {
cout << "Which phone do you want to buy (iphone11/samsungs20) ? ";
cin >> phone;
cout << "Do you want to buy a SIM Free or Pay As You Go ? ";
cin >> choice;
}
int totalPrice = 0;
for (auto item : items[choice]) {
totalPrice += stoi(item);
}
cout << "You have chosen " << phone << " (SIM Free/Pay As You Go) and your total price is: " << totalPrice << endl;
if (choice != "mobile" && choice != "sim" && choice != "accessories") {
cout << "Please choose a valid item from the list (mobile/sim/accessories)." << endl;
}
return 0;
}
What is data structures?Data structures are the way in which data is organized and stored in a computer system. Data structures provide a means to manage large amounts of data efficiently, such as large databases and internet indexing services. Data structures are used in almost every program or software system. They are essential in providing an efficient way to store and retrieve data. Data structures are divided into two categories: linear and non-linear. Linear structures include arrays, linked lists, stacks, and queues.
To learn more about data structures
https://brainly.com/question/24268720
#SPJ9
A circle surrounding the earth at the equator would consist of ___________ “degrees” of angular measurement.
90
Answers
Answer:
360°
Explanation:
Earth rotation can be defined as the amount of time taken by planet earth to complete its spinning movement on its axis.
This ultimately implies that, the rotation of earth refers to the time taken by earth to rotate once on its axis. One spinning movement of the earth on its axis takes approximately 24 hours to complete with respect to the Sun. Therefore, in a 24 hour period, the earth rotates 360 degrees about its axis and as such in an hour it rotates 15 degrees to create a 24-hours time zones.
When the earth's equatorial plane intersect with the surface of a celestial sphere, it results in the formation of a great circle which divides or cuts the earth into two equal halves known as celestial equator. This great circle divides the earth into a circumference having two (2) equal halves.
Hence, a circle surrounding the earth at the equator would consist of 360 “degrees” of angular measurement. Thus, giving rise to latitude (zones of latitude) which is north or south of the equator that includes equatorial, low latitude, mid latitude, tropical, subtropical and polar regions.
This act creates a set of requirements that allow for insurance portability, significant provisions regarding "administrative simplification" and standards for "privacy and security."
a. Consumer Directed Health Plans
b. Health Insurance Portability Accountability Act
c. Healthcare Integrity and Protection Data Bank
d. Employee Retirement Income Security Act
Answers
The correct answer is: b. Health Insurance Portability Accountability Act (HIPAA).
HIPAA ensures that employees and their families who lose their job-based health insurance are able to continue their coverage through the Consolidated Omnibus Budget Reconciliation Act (COBRA). The act also introduced administrative simplification provisions to promote efficiency and cost savings in the healthcare system.
HIPAA creates a set of requirements that allow for insurance portability, includes significant provisions regarding "administrative simplification" and establishes standards for "privacy and security." The other options, such as Consumer Directed Health Plans, Healthcare Integrity and Protection Data Bank,
To know more about HIPAA visit:-
https://brainly.com/question/14308448
#SPJ11
The act that creates a set of requirements allowing for insurance portability, significant provisions regarding "administrative simplification," and standards for "privacy and security" is the Health Insurance Portability Accountability Act (HIPAA). HIPAA was signed into law in 1996 and aims to protect individuals' health information while also making it easier for them to switch health insurance plans and providers.
One significant provision of HIPAA is the establishment of national standards for electronic healthcare transactions and code sets, which aim to simplify the administrative process and reduce healthcare costs. Additionally, HIPAA created the Privacy and Security Rules, which require healthcare providers and insurance companies to protect patients' personal health information from unauthorized access and disclosure.
HIPAA also established the Healthcare Integrity and Protection Data Bank, which is a national database that tracks healthcare providers who have been convicted of fraud or abuse. Finally, while HIPAA is often associated with healthcare providers and insurers, it also has provisions that relate to employee benefits under the Employee Retirement Income Security Act (ERISA).
Overall, HIPAA is a complex law with far-reaching implications for the healthcare industry, patients, and employers.
To know more about Health Insurance Portability visit:
https://brainly.com/question/30677213
#SPJ11