Identify and list the specififcations for the; a) structure that houses the electronic system b) electronic system within the structure mentioned in ( a ) c ) model house structure
Answers
The specifications for the structure that houses the electronic system include size, environmental conditions, electrical infrastructure, and structural integrity, while the electronic system.
Specifications for the structure that houses the electronic system:
The structure that houses the electronic system should meet certain specifications to ensure the proper functioning and safety of the system. These specifications include:
Size and Layout: The structure should be spacious enough to accommodate the electronic system and provide adequate space for equipment installation, maintenance, and accessibility. It should have a well-planned layout to facilitate the efficient arrangement of components and wiring.
Environmental Conditions: The structure should be designed to provide suitable environmental conditions for the electronic system. This includes controlling factors such as temperature, humidity, and ventilation to prevent overheating and moisture damage. Additionally, provisions should be made to minimize the impact of dust, electromagnetic interference, and other potential hazards.
Electrical Infrastructure: The structure should have a reliable and robust electrical infrastructure to support the power requirements of the electronic system. This includes proper electrical wiring, grounding, and surge protection measures to ensure stable and safe electricity supply.
Structural Integrity: The structure should be structurally sound and capable of withstanding the weight and load of the electronic system. It should be constructed using durable materials and adhere to relevant building codes and standards to ensure its stability and longevity.
Specifications for the electronic system within the structure:
The electronic system within the structure should possess certain specifications to fulfill its intended functions effectively. These specifications include:
Functionality: The electronic system should be designed to perform its intended functions efficiently. It should meet the specific requirements and tasks it is designed for, such as communication, data processing, control, or monitoring.
Compatibility and Integration: The electronic system should be compatible with the required components and technologies it interacts with. It should support necessary interfaces and protocols for seamless integration with other systems or devices.
Reliability and Performance: The electronic system should exhibit reliable operation and consistent performance. It should be able to handle the expected workload, process data accurately, and deliver reliable outputs within the specified timeframes.
Safety and Security: The electronic system should incorporate appropriate safety measures to protect users, prevent accidents, and mitigate risks. It should also implement security features and protocols to safeguard sensitive data and protect against unauthorized access.
Specifications for the model house structure:
The model house structure should serve as a representation or simulation of a real house and should include the following specifications:
Design and Layout: The model house structure should accurately depict the architectural design and layout of a typical house. It should showcase various rooms, spaces, and structural elements such as walls, doors, windows, and roof.
Scale and Proportions: The model house structure should be built to a specific scale to ensure accuracy and realistic representation. The proportions of rooms, furniture, and other features should be consistent with the chosen scale.
Detailing and Finishing: The model house structure should exhibit appropriate detailing and finishing to mimic real-life materials and textures. This includes paintwork, flooring, roof materials, and other decorative elements.
Functionality Representation: The model house structure may incorporate functional representations of certain features, such as movable doors, windows, or working lights, to enhance the realism of the model.
Learn more about the specifications here:
https://brainly.com/question/32619443
#SPJ4
Related Questions
which of these is an aggregator?
a. a browser plug-in b. a widget
c. an RSS reader d. a utility
Answers
Answer:
Answer is C. an RSS reader
1. It defines the amount of white space that appears at the top, bottom, left, and right edge of
our document.
d clipboard.
Answers
Answer:
Margin is the correct answer to the given question .
Explanation:
The main objective of the margin is to setting the white space that are showing up at the top , bottom, left and the right corners of the file or the document .
Following are steps to setting the white space that are showing up at the top , bottom, left and the right corners of the file or the document
Firstly click on the page layout options .After that click on the margin tab .In this tab you will given the the top, bottom, left, and right margin according to your need Finally click on ok to finish them .All are database management systems programs except:
a) corel paradox
b) filemaker pro
c) microsoft database
d) spreadsheets
Answers
A database is a computerised system designed to store large amounts of raw data. ... Databases can then enforce (store and show) the relationship between different records and tables. Spreadsheets cannot do this.
Research the vulnerabilities called Heartbleed and Shellshock. Discuss how they affect a computer system.
Answers
Heartbleed and Shellshock are two separate vulnerabilities that affected computer systems in the past.
What are vulnerabilities?A hole or a weakness in the application is known as a vulnerability, which can be either a design flaw or an implementation error.
The widely-used OpenSSL cryptographic software library had a flaw called Heartbleed.
On the other side, Shellshock is a flaw in the Unix Bash shell, a command-line interface that is utilized by many Unix-based operating systems.
Both Heartbleed and Shellshock could have detrimental effects on the computer systems that were impacted.
Heartbleed was a vulnerability that gave attackers access to sensitive data from vulnerable systems, which they may have used to launch additional assaults or jeopardize the user's privacy.
Thus, it is crucial that computer systems are updated often with the most recent security patches in order to guard against these and other vulnerabilities.
For more details regarding vulnerabilities, visit:
https://brainly.com/question/30296040
#SPJ9
Arturo is a security professional. He is strengthening the security of an information system. His design ensures that if a field should contain a number, the system checks the values that a user enters to make sure that the user actually entered numbers. The design also ensures that only authorized users have the ability to move or delete files. What is Arturo attempting to protect
Answers
Arturo is attempting to protect the database (data) of an information system (IS).
What is an information system?An information system (IS) can be defined as a set of computer systems, that is typically used to collect, store, and process data, as well as the dissemination of information, knowledge, and the distribution of digital products.
In Cybersecurity, there are two (2) main techniques that can be used to check data when inputted in an information system (IS) and these include:
VerificationValidationData validation is a type of check which is primarily performed by a software program (application) to make sure that the data which is entered into an information system (IS) is allowable and sensible.
This ultimately implies that, any data that is not allowed or sensible are rejected and discarded by the computer system.
In conclusion, we can deduce that Arturo is attempting to protect the database (data) of an information system (IS).
Read more on data here: https://brainly.com/question/25885448
resources that can be saved through the use of computers
Answers
Answer:
Yes. That's what the internet is all about. Saving resources through interconnected computers.
URGENT! REALLY URGENT! I NEED HELP CREATING A JAVASCRIPT GRAPHICS CODE THAT FULFILLS ALL THESE REQUIREMENTS!

Answers
In the program for the game, we have a garden scene represented by a green background and a black rectangular border. The cartoon character is a yellow circle with two black eyes, a smiling face, and arcs for the body. The character is drawn in the center of the screen.
How to explain the informationThe game uses Pygame library to handle the graphics and game loop. The garden is drawn using the draw_garden function, and the cartoon character is drawn using the draw_cartoon_character function.
The game loop continuously updates the scene by redrawing the garden and the cartoon character. It also handles user input events and ensures a smooth frame rate. The game exits when the user closes the window.
This example includes appropriate use of variables, a function definition (draw_garden and draw_cartoon_character), and a loop (the main game loop). Additionally, it meets the requirement of using the entire width and height of the canvas, uses a background based on the screen size, and includes shapes (circles, rectangles, arcs) that are used appropriately in the context of the game.
Learn more about program on
https://brainly.com/question/23275071
#SPJ1
Computer _ rely on up to date definitions?
A. Administrators
B. Malware Scan
C. Firmware updates
D. Storage Drivers
Answers
Answer: The correct answer is B. Malware Scan
Explanation:
The word "definition" only applies to antivirus and malware removal applications that scan for patterns using the definitions. The other choices do not use definitions. Firmware updates rely on images, storage drives use drivers and administrators are user privilege type.
which type of biometrics is based on the perception, thought process, and understanding of the user?
Answers
biometrics for the brain Emoji more closely resembles the field of cognitive biometrics (Security+ 5e), which is concerned with the user's perception, thought process, and comprehension. In contrast to normal biometrics, which take into account a person's physical traits, this field focuses on the user.
What are the four primary biometrics?Fingerprints, facial, voice, iris, and palm or finger vein patterns are the five most used biometric identifiers. For instance, in order to offer their various services remotely, banks require your biometric information.
What is an illustration of static biometrics?For mobile phone unlocking, bank account login, and other purposes, static biometrics use physical characteristics like a fingerprint scan or facial recognition.
To know more about biometrics visit :-
https://brainly.com/question/20318111
#SPJ4
in the conversation program, which input value was converted to another type after being entered by the user?
Answers
Age input value was converted to another type after being entered by the user.
An early time-sharing system provided by IBM, the Conversational Programming System (CPS), ran on System/360 mainframes from 1967 to 1972 in a partition of OS/360 Release 17 MFT II or MVT or higher.[2] Users had the option of choosing between a fairly complete version of PL/I or a basic version of BASIC when using the CPS interpreter.
The remote job entry (RJE) features of a third option let users submit JCL job streams for batch processing. Control mode was a fourth choice. Control mode would typically only be accessible to the system operator. The features accessible in control mode included:
Send a message to a specific user or to everyone.
Clobber (what we would now refer to as "re-boot") a particular user's virtual CPS
To know more about conversation program, here
https://brainly.com/question/18691764
#SPJ4
why do most operating systems let users make changes
Answers
By these changes you most likely are thinking of the term 'Over Clocking'
Over Clocking is used on most Operating Systems to bring the item your over clocking to the max.
Over Clocking; is mostly used for Crypto mining and gaming.
Which of the following is true about K-Mean Clustering?
1. K-means is extremely sensitive to cluster centroid initializations.
2. Poor initialization can lead to sub-optimal results.
3. Poor initialization can lead to slow convergence.
1 and 2 only
2 and 3 only
1 and 3 only
All of the above
Answers
The option that is true about K-Mean Clustering is options 1 and 3 only:
1. K-means is extremely sensitive to cluster centroid initializations.
3. Poor initialization can lead to slow convergence.
Why is k-means a difficulty for optimization?The goal of clustering, a vector quantization technique that originated in signal processing, is to divide n observations into k clusters, where each observation belongs to the cluster that has the closest mean (also known as the cluster centroid or cluster centers), acting as a prototype for the cluster.
Therefore, By using a deterministic global optimization technique, the global k-means clustering algorithm overcomes the primary drawback of k-means clustering, which is its sensitivity to the initial placements of the cluster centers.
Learn more about K-Mean Clustering from
https://brainly.com/question/15016224
#SPJ1
e) most machine learning algorithms, in general, can learn a model with a bayes optimal error rate. true or false
Answers
The gven statement "most machine learning algorithms, in general, can learn a model with a Bayes optimal error rate." is false. Because most machine learning algorithms, in general, strive to achieve a low error rate, but they cannot guarantee learning a model with a Bayes optimal error rate.
The Bayes optimal error rate represents the best possible performance that can be achieved, and is typically not attainable in practice. In reality, machine learning algorithms are often used to approximate the Bayes optimal error rate as closely as possible, but the actual error rate achieved will depend on factors such as the quality and quantity of the data, the complexity of the model, and the choice of algorithm and hyperparameters.
You can learn more about machine learning algorithms at
https://brainly.com/question/30296528
#SPJ11
Consider the following illustration. What is the value of I4?
Answers
Answer:
10+4=14 or 5+9
Explanation:
i think that is the right answer
How much money would that same computer cost in louisville county, kentucky? what about in coffee county, alabama?.
Answers
The about of money that you save if you bought it in Davidson County is:
It will cost about $1,097.5 in Williamson County.It will cost about $1,092.5 in Davidson County.$5 is the amount which will be saved.What does saving money entail?Savings is the money that remains after expenses and other commitments have been subtracted from income. Savings are the sum of money that would otherwise be lying about, not being risked on investments or used for consumption.
Deferred consumption, or not spending money, is saving. Savings strategies involve setting money aside in places including cash, investment funds, pension accounts, and deposit accounts. Reducing expenses, such as regular expenses, is another aspect of saving.
Hence,
In Williamson County, the sales tax rate is 9.75% = 9.75% × $1,000 = $1,097.5
In Davidson County , the sales tax rate is 9.25% = 9.25% × $1,000 = $1,092.5
The total amount saved will be: $1,097.5 - $1,092.5 = $5.
Learn more about money from
https://brainly.com/question/27167637
#SPJ1
See full question below
If you were to buy a $1,000 computer in Tennessee, how much would it cost in
Williamson County? How much would you save if you bought it in Davidson County?
Answer:
Louisville County $1,060
Coffee County $1,050
Explanation:
Louisville: 6 x 1,000 = 6,000 hit the percent button and you get 60 then just add that to the original 1,000. Do the same thing with Coffee County
Chapter 2 discusses three major information finding tools; web search engines, library discovery tools, and article indexes. Why would you use multiple finding tools when looking for information?.
Answers
Why to use web search engines?
Web search engines are devices that browse the internet based on the keywords you
enter. Bing, DuckDuckGo, and Yahoo are a few of the most widely used search
engines.
Why to use library discovery tools?
A collection of links to numerous journal articles and other online resources the library subscribes to is combined with the standard library catalog (which lists the materials the library holds) in library discovery tools. A sample of a library discovery tool is Quick Search in the ISU Library.
Why to use article indexes?
Finding scholarly materials like journal articles, book chapters, and more is made easier with the use of article indexes and databases. Finding specific results is made possible by these tools, which employ the keywords you supply to search through information on scholarly sources (such as themes, authors, and titles).
Hence, its best to use multiple finding tools when looking for information.
You can learn more about web search engines for finding information from the given link:
https://brainly.com/question/512733
#SPJ4
in this assignment, we’ll follow the database design process with a step-by-step example. your client, wellness week is a small, specialized publisher that publishes articles on health and wellness issues. the owner would like to have a small database that would track authors and articles.
Answers
By following these steps, you can design a small database for Wellness Week that tracks authors and articles. The tables "authors" and "articles" will hold the necessary information, and the relationship between them will be established through the use of foreign keys.
To design a database for Wellness Week, a small specialized publisher, that tracks authors and articles, you can follow the database design process with a step-by-step example.
Explanation:
1. Identify the entities: The entities in this case are "authors" and "articles". These entities represent the main objects of interest in the database.
2. Identify the attributes: For the "authors" entity, you may include attributes such as "author_id", "name", "email", and "specialty". For the "articles" entity, you may include attributes such as "article_id", "title", "content", "publication_date", and "author_id" (to establish a relationship between authors and articles).
3. Establish relationships: In this case, there is a relationship between authors and articles, as an author can write multiple articles and an article can be written by a single author. To establish this relationship, you can use the "author_id" attribute in the "articles" entity as a foreign key referencing the "author_id" attribute in the "authors" entity.
4. Create tables: Based on the identified entities and attributes, create tables in your database. In this case, you would create a table called "authors" with columns for "author_id", "name", "email", and "specialty". You would also create a table called "articles" with columns for "article_id", "title", "content", "publication_date", and "author_id".
5. Define primary and foreign keys: Choose the appropriate attribute(s) to be the primary key for each table. In this case, "author_id" can be the primary key for the "authors" table, and "article_id" can be the primary key for the "articles" table. The "author_id" attribute in the "articles" table will also be a foreign key referencing the "author_id" attribute in the "authors" table.
Conclusion:
By following these steps, you can design a small database for Wellness Week that tracks authors and articles. The tables "authors" and "articles" will hold the necessary information, and the relationship between them will be established through the use of foreign keys.
To know more about database visit
https://brainly.com/question/6447559
#SPJ11
3.5 code practice
grade = str(input("What year of high school are you in?: "))
if ("grade ==Freshman"):
print("You are in grade: 9")
elif ("grade == Sophomore"):
print("You are in grade: 10")
elif ("grade == Junior"):
print("You are in grade: 11")
elif ("grade == Senior"):
print("You are in grade: 12")
else:
print("Not in High School")
It keeps printing your are in grade 9. Why?
Answers
The fixed code is shown below. input() function already returns string that's why you don't have to convert string again. Also the syntax in if-else scope is wrong.
grade = input("What year of high school are you in?: ")
if(grade.lower()=="freshman"):
print("You are in Grade 9.")
elif(grade.lower()=="sophomore"):
print("You are in Grade 10.")
elif(grade.lower()=="junior"):
print("You are in Grade 11.")
elif(grade.lower()=="senior"):
print("You are in Grade 12.")
else:
print("Wrong input!")
Which is the best example of an unreliable narrator?
O A. A guilty criminal
O B. A loyal friend
O C. A strict parent
O D. A bored academic
Answers
Software that interprets command from the keyboard and mouse is also known as?
Answers
Answer:
I believe the answer is, Operating System.
Which logical address is responsible for delivering the ip packet from the original source to the final destination, either on the same network or to a remote network?.
Answers
Source and destination IP logical address is responsible for delivering the IP packet from the original source to the final destination, either on the same network or to a remote network.
The IP packet field holding the IP address of the workstation from which it originated is known as the source IP address. The IP packet field holding the IP address of the workstation to which it is addressed is known as the destination IP address. An IP address is a logical address that is given by router or server software, and that logical address may occasionally change. For instance, when a laptop starts up in a different hotspot, it is likely to receive a new IP address. The IP addresses for the source and destination can match. That merely denotes a connection between two peers (or client and server) on the same host. Ports at the source and destination may also match.
Learn more about Destination here-
https://brainly.com/question/12873475
#SPJ4
encryption and decryption technology are example of safeguards? physical, administrative, technical network
Answers
Encryption and decryption technology are an example of technical safeguards. Technical safeguards are measures to protect data stored in an information system from unauthorized access.
Decryption is the process of converting encrypted data back to its original form, while encryption is the process of converting plain text into cipher text that is unreadable by unauthorized parties. Technical safeguards also include firewalls, intrusion detection systems, and access controls. Technical safeguards are just one aspect of a comprehensive information security program. Physical, administrative, and network safeguards are also important to consider in ensuring that data is protected from unauthorized access.
Encryption is, at its most fundamental level, the process of scrambling data or information using mathematical models in such a way that only those parties who possess the key to unscramble it can access it.
Know more about Encryption, here:
https://brainly.com/question/30225557
#SPJ11
When a web site vulnerability assessment is completed, the report typically contains a common vulnerabilities and exposures (cve)for each vulnerability. what does this represent?
Answers
The Common Vulnerabilities and Exposures (CVE) is a standardized identifier that helps track and communicate software vulnerabilities. It allows security professionals to discuss vulnerabilities effectively and ensures a common understanding across different organizations and tools.
When a web site vulnerability assessment is completed, the report typically contains a Common Vulnerabilities and Exposures (CVE) for each vulnerability. The CVE represents a unique identifier assigned to a specific software vulnerability. It serves as a standardized way to reference and track vulnerabilities across different organizations and security tools.
The CVE is important because it allows security professionals and researchers to communicate and share information about vulnerabilities effectively. It provides a common language and framework to discuss and analyze vulnerabilities in software applications and systems.
Each CVE has a unique identification number, such as "CVE-2021-1234." This identifier helps identify the specific vulnerability in question. It allows security teams to accurately reference and discuss vulnerabilities, ensuring everyone is referring to the same issue.
The CVE system is maintained by the MITRE Corporation, a non-profit organization that collaborates with various security communities and stakeholders. They assign CVE numbers and maintain a public database where detailed information about each vulnerability is available.
For example, if a vulnerability assessment identifies a specific flaw in a website's software, the report will include the CVE number associated with that vulnerability. This number can then be used to look up additional information about the vulnerability, such as its severity, impact, and possible mitigation measures.
Learn more about Common Vulnerabilities and Exposures here:-
https://brainly.com/question/33478441
#SPJ11
List out differences in the ways global communities were formed before and after the advent of the internet and social media.
Answers
Answer:
is a remarkably complex technical system built on the creative contributions of scientists around the world from the 1950s to the present. Throughout its evolution, the Internet and other networks have been promoted by governments, researchers, educators, and individuals as tools for meeting a range of human needs. A combination of high-level policy and grassroots improvisation has produced social benefits including easier and more widespread access to computers and information; increased scientific collaboration; economic growth; the formation of virtual communities and an increased ability to maintain social ties over long distances; the democratization of content creation; and online political and social activism. The Internet’s rapid growth has also spawned technical crises, such as congestion and a scarcity of network addresses, and social dilemmas, including malicious and illegal activities and persistent digital divides based on income, location, age, gender, and education. Such problems continue to demand creative solutions from scientists, policy makers, and citizens.
Several general themes characterize the technical development of the Internet. First, from the 1950s to the present there has been a steady increase in the size of data networks and the variety of services they offer. Rapid growth and diversity have forced network designers to overcome incompatibilities between computer systems and components, manage data traffic to avoid congestion and chaos, and reach international agreement on technical standards. These challenges have led to fundamental advances in research areas such as operating systems and queuing theory. A second trend has been the modeling of network functions as a series of layers, each of which behaves according to a standard protocol, a set of rules for interaction that is implemented in software or hardware. Layering reduces the complexity of the network system and minimizes the amount of standardization necessary, which makes it easier for networks to join the Internet. A third important feature of the Internet’s technical development has been an unusually decentralized and participatory design process. This has opened the system to innovation from a variety of directions and has encouraged informal worldwide collaboration. The following sections describe some of the major milestones in the evolution of the Internet and its predecessors.
If you give someone ______ to your device, they can control it through another phone or computer.
Answers
If you give someone Remote access to your device, they can control it through another phone or computer.
What is Remote entry?An authorized user can use remote access to connect to a computer or network from a different location using a network connection. Users can connect to the systems they require through remote access even if they are physically far away.
Therefore, the dangers to remote access are:
There is a risk of device loss or theft due to a lack of physical security safeguards.as the data is transmitted through a public internet, eavesdropping.unapproved access to systems or data, possibly while oblivious to the screen.If someone gets access to the gadget, they could watch and change the data.Learn more about Remote access from
https://brainly.com/question/28900477
#SPJ1
the volume of two similar solids are 1080cm and 1715cm .if the curved surface area of the smaller cone is 840cm .fond the curved surface area of the larger cone
Answers
Answer:
\(A_{big} = 1143.33cm^2\)
Explanation:
The given parameters are:
\(V_{small} = 1080\)
\(V_{big} = 1715\)
\(C_{small} = 840\)
Required
Determine the curved surface area of the big cone
The volume of a cone is:
\(V = \frac{1}{3}\pi r^2h\)
For the big cone:
\(V_{big} = \frac{1}{3}\pi R^2H\)
Where
R = radius of the big cone and H = height of the big cone
For the small cone:
\(V_{small} = \frac{1}{3}\pi r^2h\)
Where
r = radius of the small cone and H = height of the small cone
Because both cones are similar, then:
\(\frac{H}{h} = \frac{R}{r}\)
and
\(\frac{V_{big}}{V_{small}} = \frac{\frac{1}{3}\pi R^2H}{\frac{1}{3}\pi r^2h}\)
\(\frac{V_{big}}{V_{small}} = \frac{R^2H}{r^2h}\)
Substitute values for Vbig and Vsmall
\(\frac{1715}{1080} = \frac{R^2H}{r^2h}\)
Recall that:\(\frac{H}{h} = \frac{R}{r}\)
So, we have:
\(\frac{1715}{1080} = \frac{R^2*R}{r^2*r}\)
\(\frac{1715}{1080} = \frac{R^3}{r^3}\)
Take cube roots of both sides
\(\sqrt[3]{\frac{1715}{1080}} = \frac{R}{r}\)
Factorize
\(\sqrt[3]{\frac{343*5}{216*5}} = \frac{R}{r}\)
\(\sqrt[3]{\frac{343}{216}} = \frac{R}{r}\)
\(\frac{7}{6} = \frac{R}{r}\)
The curved surface area is calculated as:
\(Area = \pi rl\)
Where
\(l = slant\ height\)
For the big cone:
\(A_{big} = \pi RL\)
For the small cone
\(A_{small} = \pi rl\)
Because both cones are similar, then:
\(\frac{L}{l} = \frac{R}{r}\)
and
\(\frac{A_{big}}{A_{small}} = \frac{\pi RL}{\pi rl}\)
\(\frac{A_{big}}{A_{small}} = \frac{RL}{rl}\)
This gives:
\(\frac{A_{big}}{A_{small}} = \frac{R}{r} * \frac{L}{l}\)
Recall that:
\(\frac{L}{l} = \frac{R}{r}\)
So, we have:
\(\frac{A_{big}}{A_{small}} = \frac{R}{r} * \frac{R}{r}\)
\(\frac{A_{big}}{A_{small}} = (\frac{R}{r})^2\)
Make \(A_{big}\) the subject
\(A_{big} = (\frac{R}{r})^2 * A_{small}\)
Substitute values for \(\frac{R}{r}\) and \(A_{small}\)
\(A_{big} = (\frac{7}{6})^2 * 840\)
\(A_{big} = \frac{49}{36} * 840\)
\(A_{big} = \frac{49* 840}{36}\)
\(A_{big} = 1143.33cm^2\)
Hence, the curved surface area of the big cone is 1143.33cm^2
Complete the body of the format_name function. This function receives the first_name and last_name parameters and then returns a properly formatted string. Specifically: If both the last_name and the first_name parameters are supplied, the function should return like so:
Answers
Answer:
Here is the Python program:
def format_name(first_name, last_name): #function definition of format_name that takes first_name and last_name as parameters
if first_name != '' and last_name != '': #checks if first_name and last_name both are not equal to " "
return ("Name: " + last_name + ", " + first_name) #returns first name and last_name in format: "Name: last_name, first_name"
elif first_name != '' or last_name != '': #checks if either of the first_name or last_name is not equal to " "
return ("Name: " + last_name + first_name) #returns first name and last_name in format: "Name: last_name" or "Name: first_name"
else: #if both names are blank
return '' #return ""
Explanation:
The working of the above function can be checked by using the following statements:
print(format_name("Ernest", "Hemingway"))
print(format_name("Voltaire", ""))
print(format_name("", "Madonna"))
print(format_name("", ""))
The program has a function format_name which takes two strings i.e. the first_name and last_name as parameters and returns the formatted string.
The first if condition checks if both the first_name and last_name are blank. For example if first_name = "Ernest" and last_name= "Hemingway" this means both the first_name and last_name are not blank or empty. So If this condition evaluates to true then the following statement is returned:
return ("Name: " + last_name + ", " + first_name)
This returns the last_name string first followed by a comma in between and then first_name string in the last. For the above example the string is printed in the following format:
Name: Hemingway, Ernest
The elif condition checks if either of the first_name or last_name is blank. For example if first_name = "Voltaire" and last_name= "" this means last_name is blank or empty. So if this condition evaluates to true then the following statement is returned:
return ("Name: " + last_name + first_name)
This returns the last_name string. For the above example the string is printed in the following format:
Name: Voltaire
IF none of the above condition is true and both the first_name and last_name are blank then the following statement is returned
return ''
This will just print and blank space in output.
The program and its output is attached.

SRS Template 1. Introduction 1.1 Purpose This document has been created to serve as a guide for developers in the development of ________, and as a description of deliverables for the Customer.
Answers
The completed statement with regard to SRS is "This document has been created to serve as a guide for developers in the development of software, and as a description of deliverables for the Customer."
What is SRS?A software requirements specification (SRS) is a document that clarifies what the program will accomplish and how it should function. It also outlines the functionality required by the product to meet the demands of all stakeholders (businesses and consumers).
The amount of formality and information in the SRS will vary depending on the approach used (agile versus waterfall), but in general, an SRS should contain a representation of the technical specifications, system requirements, operational specifications, constraints, assumptions, and acceptance criteria.
Learn more about software requirement specifications.:
https://brainly.com/question/24003956
#SPJ1
Barack often sends funny jokes to Hillary. He does not care about confidentiality of these messages but wants to get credit for the jokes and prevent Bill from claiming authorship of or modifying them. How can this be achieved using public-key cryptography
Answers
The public-key cryptography can help Barack achieve the goal of getting credit for the jokes and prevent Bill from claiming authorship of or modifying them by using a digital signature.
Digital signature and public-key cryptography together can ensure the confidentiality of the messages sent between Barack and Hillary, the integrity of the messages and prevent any unauthorized person from claiming the authorship of or modifying the messages.The digital signature is created by combining the message and a hash function. The hash function creates a fixed-size output or message digest that represents the original message.
This hash function ensures that if any change is made to the original message, the digital signature will not match the new message and the recipient will know that the message has been tampered with.To create a digital signature, Barack must first use his private key to encrypt the hash value of the message. This creates a unique signature for the message that only he can create since only he has access to his private key. He then sends the message and the signature to Hillary. Hillary can verify the digital signature by using Barack's public key to decrypt the signature.
To know more about digital signature visit:
https://brainly.com/question/32663138
#SPJ11
please help me i will award brainliest
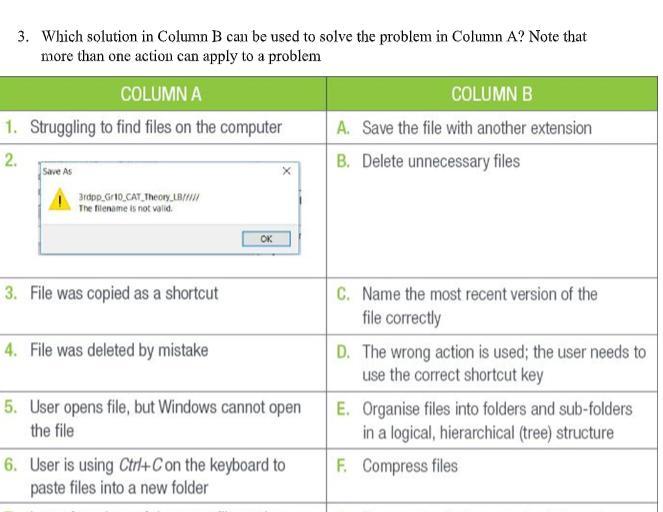

Answers
Answer: It would be option C.
Explanation: The file name is invalid, so therefore it would make sense to rename the most recent version correctly.